2022-7-26 15:29:44 Author: blog.avast.com(查看原文) 阅读量:24 收藏
The malware was found in more than 300 restaurants that used them and exposed more than 50,000 paid orders.
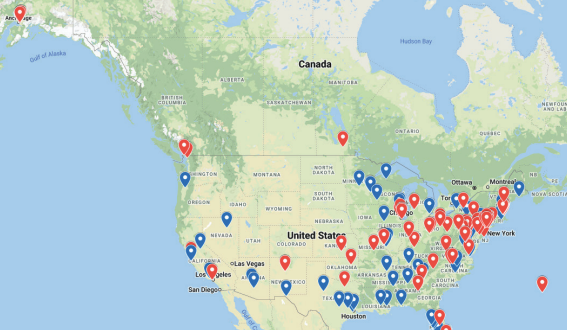
Magecart, the notorious credit card stealing cybercrime syndicate, is once again in the news. We last wrote about it last summer, where it compromises Magento shopping cart software pages to steal credit card information. That post had a long list of various attacks going back to 2018 and showed a progression of “enhancements.” Magecart is the gift that keeps on giving – it has recently taken root in three different online restaurant ordering websites: MenuDrive, Harbortouch, and InTouchPOS. The malware was found in more than 300 restaurants that used them and exposed more than 50,000 paid orders, according to one analysis. What’s especially noteworthy about this latest development is the fact that the malware was present in some of these systems for many months before they were discovered. Indeed, some attacks began last November and are still active. The malware takes advantage of shared code libraries in the ordering systems and modifies this code so as to redirect the payment process to domains owned by the criminals. The payment data is collected and then sold across the Dark Web. In some cases, the malicious scripts are still present, but the domains used by the criminals have been neutralized by the internet providers involved. Many of the restaurants involved were small local places. In the map below, the red markers represent restaurants that use MenuDrive, while the blue ones are restaurants using Harbortouch. Image credit: Recorded Future If Harbortouch sounds vaguely familiar, it may be because 4,200 outlets using their software were compromised with a similar breach back in 2015 and were reported by Brian Krebs. What makes these attacks difficult to find is the fact that the infected web pages are buried deep within subdirectories on the ordering sites, so some website security scanners may not discover them or may not have run a scan since the page’s JavaScript code has been modified. This means that restaurants must now carefully select online ordering platforms to prioritize security and have a thorough understanding of these third-party platforms’ security practices, too. Delivery apps have other problems, as we've written about separately. We've explained the various privacy incursions of DoorDash and GrubHub and what data they share with social media sites as well as your exact location of your phone. What's the best defense against Magecart attacks? To stay protected against these malicious campaigns, there are a few reliable practices that you can implement. First, host as many of your third-party scripts on your own servers, vet them periodically, and apply software updates quickly. We recognize that that may not always be entirely possible, especially for the restaurant or food delivery cases cited above. In these cases, you can tune your news alerts to notify you about compromises in the main tech apps that you use. You should also remain aware of when your software versions are outdated so that you can get in touch with your providers to perform necessary updates.
如有侵权请联系:admin#unsafe.sh