2022-7-26 17:6:11 Author: infosecwriteups.com(查看原文) 阅读量:21 收藏
Hi Everyone!,
Hope you all are doing well :)
This article is about my recent finding of a mail server misconfiguration among multiple targets that allowed me to perform unauthorized actions on vulnerable web applications, This vulnerability is common among multiple targets and different types of web applications. Dropbox fixed the issue and awarded me a bug bounty of $4,913.
Description
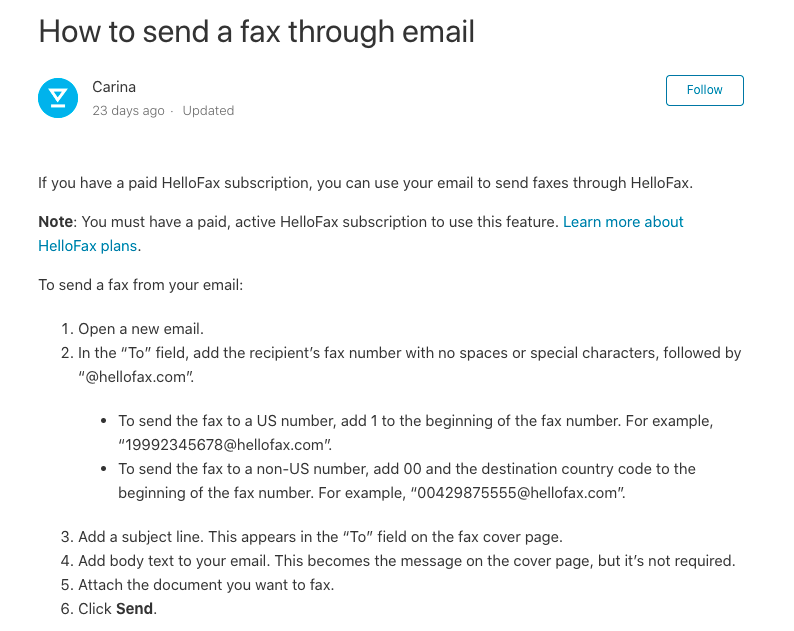
I was working on the HelloFax application at Dropbox BBP and looking for auth issues but the application is well sanitized against authorization issues such as IDOR and Access Control so I thought to look for more interesting functionalities, I found a functionality that allows users to send a fax using their email without logging into their HelloFax account

So , when a paid user sends an email to [email protected], the application sends the content of the email as a fax to FAXNUMBER from the user’s HelloFax account, For eg. If I send an email [email protected], then the application sends a fax to +13456789000 from my HelloFax account
Exploitation
Here the first thing that came to my mind was to send a fake email to [email protected] by putting the victim’s email into FROM field, I quickly went to http://anonymailer.net/ and sent a fake email to [email protected], Surprisingly it worked well and I received this mail from HelloFax

This email says that our fax has been sent successfully and the mail server at Hellofax did not verify the authenticity of the fake email sent by me and it sent the email from the victim’s account
Here is how the vulnerability works:-
- Target allows us to perform an action by sending an email to [email protected]
- An attacker sends a fake email to [email protected] by putting the victim’s email in FROM field
- The target server receives the email and does not verify its authenticity and considers it as a legit email sent from a user
- Application processes the email and performs action from the victim’s account and leads to authorization bypass
I reported the bug immediately to Dropbox BBP on Hackerone and it got triaged the next day but the team downgraded the severity to High stating the following reason

Though they paid me a bounty of $4913 on High category as per their policy

Other Exploitation Scenarios
- I found the same vulnerability on a bug reporting portal that allowed me to create bug tickets from the victim’s account by sending an email to [email protected]
- This bug could be found on applications that are using their own support panels and we can create tickets there on behalf of the internal team or any other user
- Any other kind of application that performs actions or creates tickets/bugs by sending email to them
The root cause of this vulnerability is that the target server does not verify SPF records, Email clients configured to use SPF and DMARC will automatically reject emails that fail validation and this should be applied to applications to prevent this vulnerability
Timeline
16-Dec-2021 — Reported bug to Dropbox BBP on Hackerone
17-Dec-2021 — Bug Triaged by Hackerone Triage Team
31-Dec-2021 — $4913 Bounty awarded by Dropbox Team
17-March-2022 — Dropbox Team fixed the issue
02-May-2022 — Report closed as resolved
Thanks for reading this, If you have any queries, feel free to reach me on Twitter at @ehsayaan or [email protected]
Special thanks to Sam Curry for proofreading this writeup
Until next time!
From Infosec Writeups: A lot is coming up in the Infosec every day that it’s hard to keep up with. Join our weekly newsletter to get all the latest Infosec trends in the form of 5 articles, 4 Threads, 3 videos, 2 Github Repos and tools, and 1 job alert for FREE! https://weekly.infosecwriteups.com/
如有侵权请联系:admin#unsafe.sh