
2022-7-27 15:22:45 Author: infosecwriteups.com(查看原文) 阅读量:284 收藏
Moral of the story — test concurrent requests
I wrote about race conditions in a previous article titled “This is why you should ALWAYS check for Race Conditions (even in JavaScript) — an Infinite Money Glitch”, and then I went through an example in a Hack The Box (HTB) capture the flag challenge.
Now, here is a real-life example of a race condition two hackers, HackerOne users @cyberboy and @z0mb13, found that led them to a $5000 bounty.

The original, full disclosed report can be found here at HackerOne. The bug was found on a platform called Starport. Note: the Github repo can be found here. Starport is the “easiest way to build a blockchain,” and is built on the Cosmos SDK (quote source: Github repo). According to the Cosmos site and as of July 26, 2022, the market cap of tokens built on Cosmos is over 53 Billion USD, most notably Binance Coin. That’s a lot of moola.
Users @cyberboy and @z0mb13 found a race condition in Starport implementation of the crypto faucet. I’m not an expert in crypto, but my understanding is that a crypto faucet is an application that rewards users with a certain amount of tokens in exchange for completing tasks. Essentially, tokens are given out for “free.” Here is good link for further understanding.
In the Starport implementation, the builder can set a configuration on the max number of tokens that can be rewarded from the faucet. The purpose of this is so that users can only get a certain number of max tokens per task. In the PoC, our hackers set max to 11 with 5 tokens sent on each POST request.

The duo sent two POST requests to do two transfers to Alice’s account. Now, with 10 tokens in Alice’s account, the duo should not be able to send more on subsequent requests to Alice’s account. Note: this is EXACTLY like our exploit on HTB Diogenes’ Rage. However, the duo sent 50 concurrent requests…
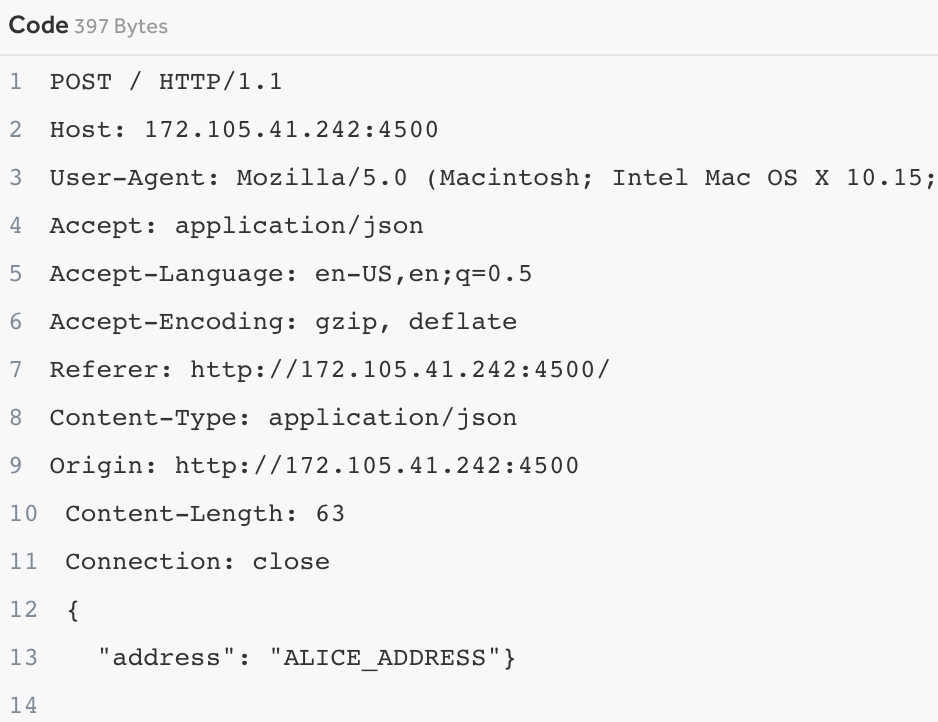
Bingo! The team found that Alice’s account had 30 tokens instead of 10. The implications of this bug are that a user could extract many more “free” tokens on any faucet application built on the Starport services, meaning many crypto token developers in theory could hemorrhage tokens. This proved to be a huge and dangerous race condition with a severity rating of 9.3!!! Again, please read the H1 original report here as well as the initial Github issue here to see the source code.
Incredible work again by @cyberboy and @z0mb13, and congrats on your $5000 bounty. Thanks for reading through and please leave any constructive feedback, suggestions, or questions below! If you enjoyed, please consider following me on Medium. Contact me at [email protected], follow me on twitter, and connect with me on LinkedIn!
From Infosec Writeups: A lot is coming up in the Infosec every day that it’s hard to keep up with. Join our weekly newsletter to get all the latest Infosec trends in the form of 5 articles, 4 Threads, 3 videos, 2 Github Repos and tools, and 1 job alert for FREE! https://weekly.infosecwriteups.com/
如有侵权请联系:admin#unsafe.sh