
Elcomsoft iOS Forensic Toolkit supports checkm8 extraction from all compatible devices ranging from the iPhone 4s and all the way through the iPhone X (as well as the corresponding iPad, iPod Touch, Apple Watch and Apple TV models). The new update removes an important obstacle to the acquisition of the iPhone 7 and iPhone 7 Plus devices running recent versions of iOS.
The Issue
At the time checkm8 was initially released, it was often referenced as a “permanent, unpatchable” exploit. However, Apple introduced new security measures in iOS 14 specifically for the newer devices including the iPhone 7, iPhone 8 and iPhone X range that changed the way the device boots and how the data volumes are unlocked. These patches had an immediate result on iOS forensics. In order to extract the file system and decrypt the keychain, the screen lock passcode had to be removed from the device prior to exploiting and unlocking. There are several problems with this approach:
- The extraction process is no longer forensically sound as many changes are made to the device.
- Under certain circumstances, the passcode cannot be removed until one signs in to iCloud from the affected device, which creates the obvious risks of remote wipe/lock, as well as unwanted data sync.
- If you use a workaround described in How to Remove The iPhone Passcode You Cannot Remove, the reset of device settings causes even more changes on the device, let along it’s not always possible (e.g. if a Screen Time password is set, or the device is managed).
- The passcode removal causes some data to be permanently lost, such as Apple Pay transactions, downloaded Exchange-based mail, some application tokens etc.
- The device is no longer “trusted” in a sense of accessing end-to-end encrypted data stored in iCloud.
The Solution
Our approach to solving the issue is applying a SEP exploit. SEP (Secure Enclave Processor) is exploitable on the iPhone 7, and the exploit is available in public. With this exploit, we were able to improve the checkm8 extraction of the iPhone 7, eliminating the need to remove the screen lock passcode. The data partition is successfully unlocked even in iOS 15, but only if you know the passcode. If you don’t, you will be limited to BFU (Before First Unlock) extraction, which is honestly not a lot but still better than nothing.
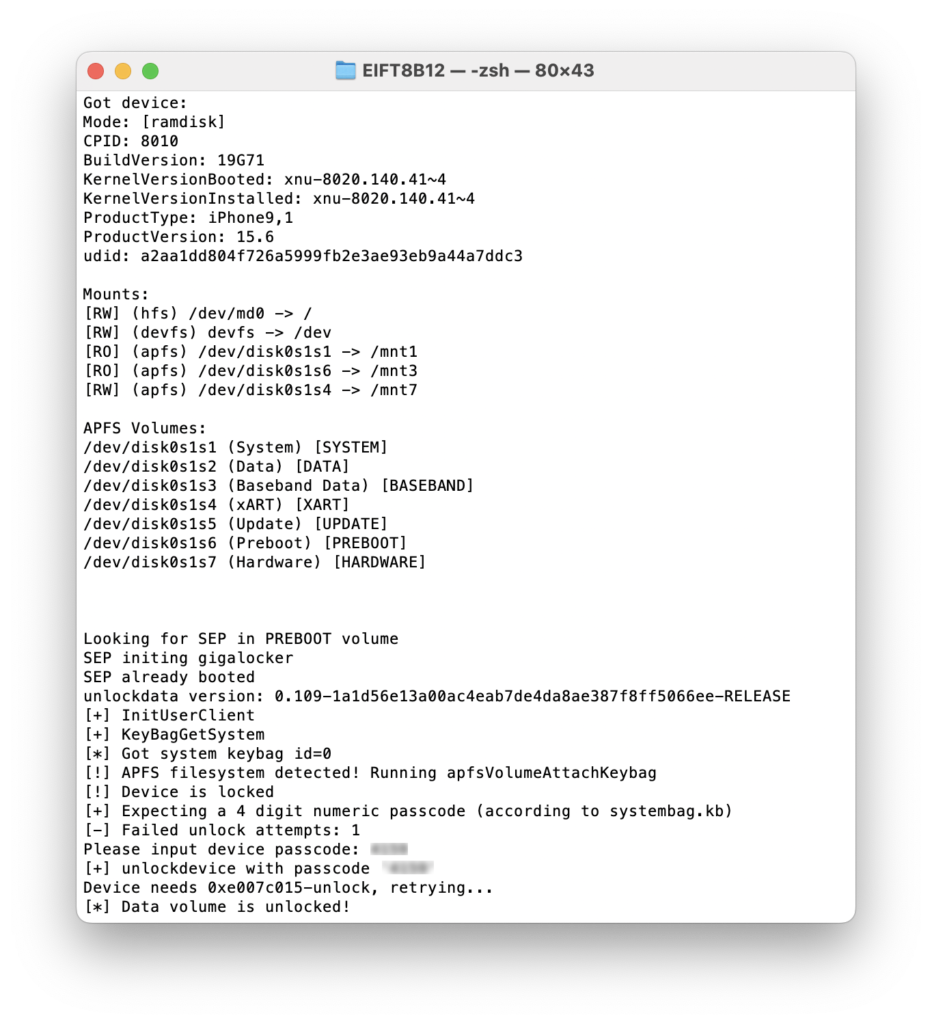 Unfortunately, the same approach cannot be implemented for the iPhone 8 and iPhone X devices running iOS 14 or newer. No SEP exploit is available for these models, and so performing a full file system extraction with checkm8 still requires you to remove the screen lock passcode from the device. Alternatively, you may perform agent-based acquisition, which is currently limited to iOS 15.1 and lower (support for newer versions is under development).
Unfortunately, the same approach cannot be implemented for the iPhone 8 and iPhone X devices running iOS 14 or newer. No SEP exploit is available for these models, and so performing a full file system extraction with checkm8 still requires you to remove the screen lock passcode from the device. Alternatively, you may perform agent-based acquisition, which is currently limited to iOS 15.1 and lower (support for newer versions is under development).
Conclusion
With the latest update, Elcomsoft iOS Forensic Toolkit becomes the most advanced iPhone acquisition product on the market, supporting all possible acquisition methods (extended logical, checkm8 and agent) supporting a wide range of devices and iOS versions.
REFERENCES:
![]()
Elcomsoft iOS Forensic Toolkit
Extract critical evidence from Apple iOS devices in real time. Gain access to phone secrets including passwords and encryption keys, and decrypt the file system image with or without the original passcode. Physical and logical acquisition options for all 64-bit devices running all versions of iOS.
Elcomsoft iOS Forensic Toolkit official web page & downloads »
如有侵权请联系:admin#unsafe.sh