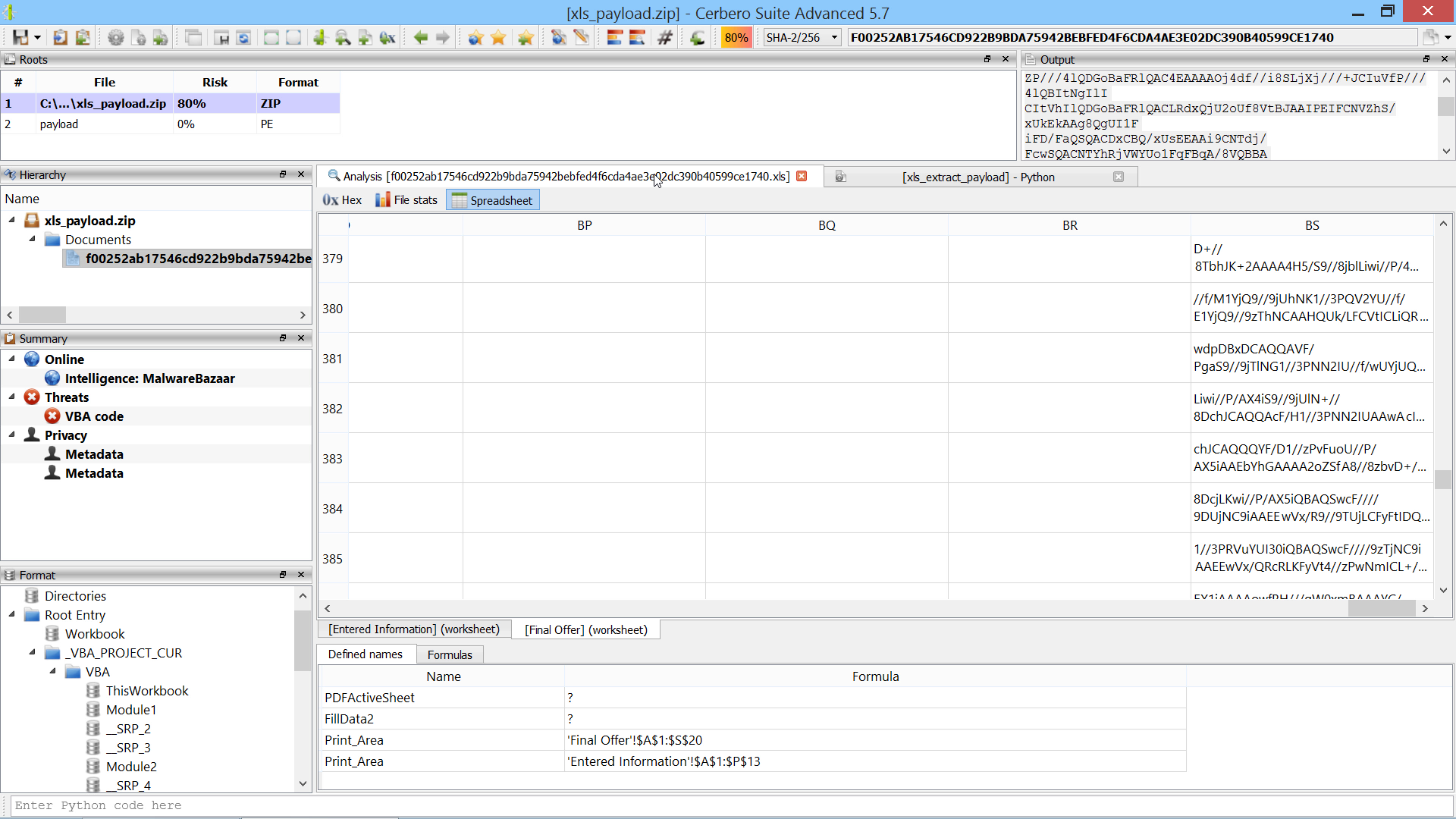
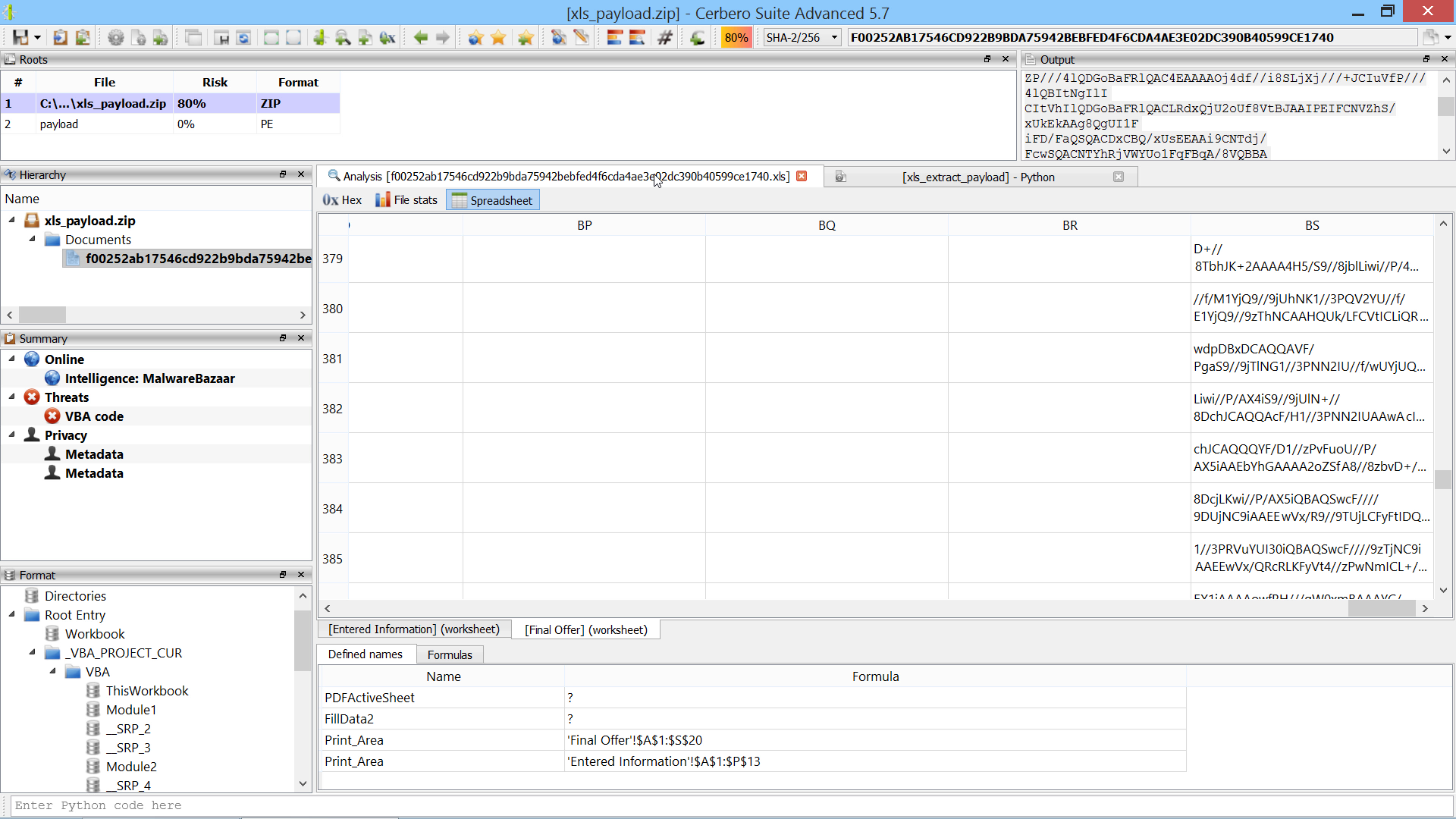
The malware sample analyzed in this video uses VBA code to extract a payload contained in Excel spreadsheet cells.
SHA256: F00252AB17546CD922B9BDA75942BEBFED4F6CDA4AE3E02DC390B40599CE1740
The following is the Python code which mimics the VBA extraction code.
from Pro.SiliconSpreadsheet import *
from Pro.UI import proContext
v = proContext().getCurrentAnalysisView()
if v.isValid():
view = SiliconSpreadsheetWorkspaceView(v)
ws = view.getSpreadsheetWorkspace()
sheet = ws.sheetFromName("Final Offer")
col = SiliconSpreadsheetUtil.colIndex("BS")
text = ""
for i in range(100, 701):
cell = sheet.getCell(col, i)
if cell.isEmpty():
continue
text += cell.value
print(text[::-1])
Note: the code must be executed while the spreadsheet is open in the analysis view.