Have you ever looked at your server or website logs and realized that they make absolutely no sense to you? Or thought that logs just seem to take up a lot of valuable server space? Or perhaps they fail to provide clear insights into what happened in the first place?
As a security company, we deal with a lot of compromised websites on a daily basis. Unfortunately, we often have limited access to customer logs, which is one of the reasons why we don’t offer forensic analysis.
Website infections can be caused by something as simple as a compromised admin user — and resetting the password for all admin users would be a simple fix for this issue. However, most of the infected websites we clean have no logs to tell us exactly what happened that led to the website compromise, which can make it difficult to know exactly how the website was infected in the first place.
In this post, we’ll explain why logs are so important and help you understand how to use website logs to level up your security and maintain compliance.
Why are website logs so important?
Logs are exceptionally valuable when it comes to website monitoring. Maintaining up-to-date logs is vital for accountability and the security of your website.
They can help you monitor for important changes to your website, alert you of any indicators of compromise, reveal intrusion points and vulnerabilities, and provide insights into whether or not something has gone wrong. Logs are also very helpful when you need to troubleshoot technical issues or ensure user accountability.
Furthermore, if you have a website with an ecommerce store-front, logs are mandatory for PCI DSS compliance. Storing logs for future analysis is also a critical piece for GDPR, CIPA, and other regulations.*
*You’ll want to coordinate with your legal or security team about which specific regulations apply to your website.
What is the difference between a server log and an activity log?
A web server log file is an unfiltered look at the traffic to your website and contains every single request to the server.
Server logs are stored as a simple text document and automatically created and maintained by the server itself. These files document all activities for that specific server environment within a defined time-frame. For example, every time any user agent or browser requests pages, images, JavaScript or PHP from your server, this is documented and added to the server log file.
Unfortunately, Apache and NGINX server logs are not very user-friendly if you are not familiar with the structure or familiar with what each section of the log entry means. This is when activity logging comes in exceptionally handy for keeping tabs on what’s going on around your site.
Activity logs, on the other hand, provide a clear list of all actions taken by every user on the system and are a lot easier to read than server logs.
It’s much easier to trace back to what happened on a WordPress site if it has auditing plugins installed.
How to read server logs
Many hosting providers keep web server logs. However, only a few of them keep extensive logs and are able to provide them to their customers on short notice.
If you’re able to get your hands on a server log, it might look a little something like the contents found in this Apache log file.
15.34.56.78 - - [10/Aug/2022:12:19:19 -0500] "POST /wordpress/wp-login.php HTTP/1.1" 302 1259 "http://localhost/wordpress/wp-login.php" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:103.0) Gecko/20100101 Firefox/103.0" 15.34.56.78 - - [10/Aug/2022:12:20:10 -0500] "GET /wordpress/index.php/wp-json/wp/v2/posts/1?_locale=user HTTP/1.1" 200 2854 "http://localhost/wordpress/wp-admin/post.php?post=1&action=edit" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:103.0) Gecko/20100101 Firefox/103.0" 15.34.56.78 - - [10/Aug/2022:12:21:41 -0500] "POST /wordpress/index.php/wp-json/wp/v2/posts/1?_locale=user HTTP/1.1" 200 4084 "http://localhost/wordpress/wp-admin/post.php?post=1&action=edit" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:103.0) Gecko/20100101 Firefox/103.0"
Let’s break down the information here to analyze what’s provided here.
For example, the second line item contains:
- 15.34.56.78 – IP address of the client that made the request
- [10/Aug/2022:12:20:10 -0500] – date and time of the request
- “GET /wordpress/index.php/wp-json/wp/v2/posts/1?_locale=user HTTP/1.1” – request type and resource being requested
- 200 – HTTP response status code
- 2854 – size of the object returned to the client
- “http://localhost/wordpress/wp-admin/post.php?post=1&action=edit” – HTTP referer, which represents the address from which the request for the resource originated
- “Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:103.0) Gecko/20100101 Firefox/103.0” – User Agent, which identifies information about the browser/OS that the client is using to access the resource
While experienced webmasters might immediately understand from a cursory review of this log sample that a visitor logged in to a WordPress site and made a change to a post before saving it, we understand that these logs can be downright intimidating for novice users.
Server logs provide visibility on GET, HEAD, and POST requests — the requests made by visitors to download a web page (GET) or submit content to the server (POST). And server logs give a lot of insight into what was visited on the website. But you typically can’t find information that tracks user sessions or individual user behavior, such as cookies or the contents of POST requests.
How to read website activity logs
Enabling activity logs on your website will give you a quick and easy glimpse into actions that are taken on your site, and helps you associate these actions with specific users.
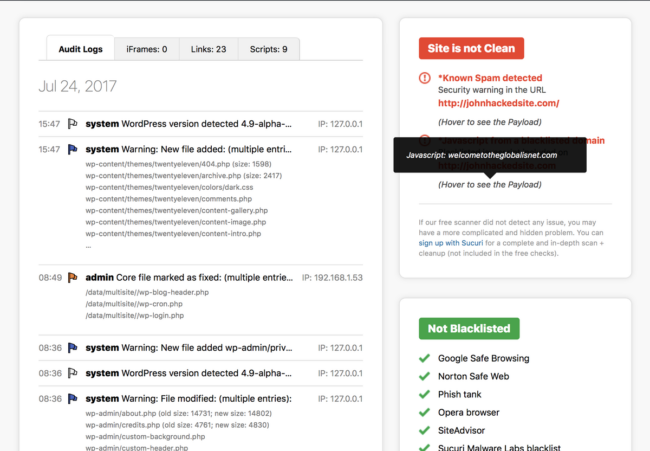
For example, if you have the Sucuri WordPress plugin installed, you’ll see clear insights into important changes made on your WordPress website.
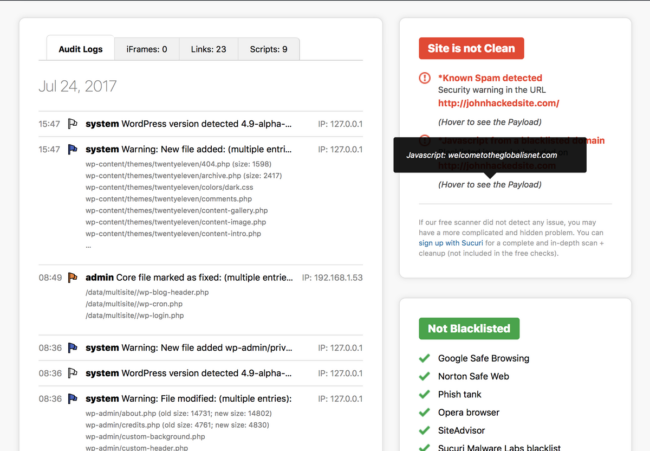
You’ll also find information about core file modifications.
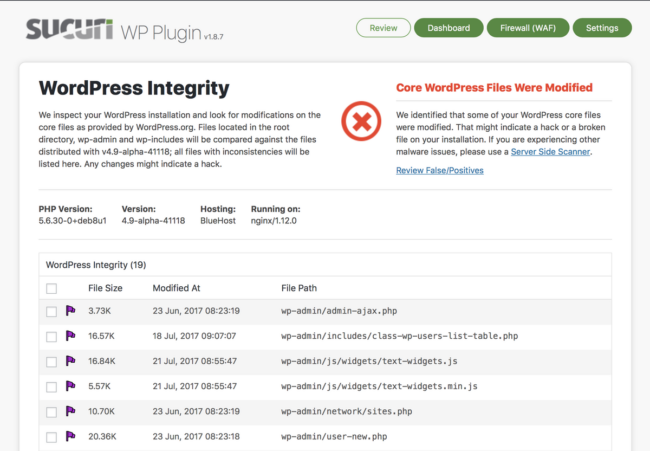
And failed login attempts for specific users.
As you can see from these screenshots, analyzing and tracking behavior across a WordPress site is pretty simple from the Sucuri plugin interface when compared to the data found in the server log.
Don’t discount server logs just because they’re hard to read, however. In many cases a website can be compromised due to an exploit in a vulnerable plugin — which means the attacker wouldn’t have logged into the WordPress site at all. This is where activity logs really fall short.
In a scenario where a plugin vulnerability has been exploited, you won’t find malicious behavior in your activity logs until a foothold has already been established and the attacker has created a malicious user.
Furthermore, if any changes are made directly to the database, you won’t see those activities either since the changes weren’t made directly from the wp-admin interface.
What changes should you track on your website?
Your server will already be documenting important requests like the sample we provided for server logs. But enabling activity monitoring for any and all changes across your CMS will help gain easy access to insights about activity on your site.
Some important activities to monitor include:
- Successful and unsuccessful login attempts
- Creation, updates and deletion of blog posts
- Creation, updates, and deletion of users
- Creation and modification of user roles and permissions
- Activation, modification, and deactivation of plugins and themes
- File uploads, modifications, and deletions
- Changes to core website files
It’s worth noting that, in this context, a website visitor is not a user. A user is someone who can log in and directly access the CMS or website.
How to log activity with WordPress plugins
WordPress doesn’t immediately log activity straight out of the box. But one of the easiest ways to start logging activity on your WordPress website is to activate a plugin.
We have our own free WordPress auditing plugin which includes some useful features:
- Security activity auditing
- File integrity monitoring
- Remote malware scanning
- Blacklist monitoring
- Effective security hardening
- Post-hack security actions
- Security notifications
- Integration with website firewall (premium)
There are quite a few other excellent WordPress audit log plugins available on the WordPress plugin repository as well.
Like with any other software, which plugin you choose depends on your requirements. Here are some personal suggestions:
- Simple History shows recent changes made within WordPress and logs important events like post updates, attachments, comments and plugin changes.
- The WP Activity Log has a great number of resources and offers a lot of visibility on a website’s logs. The Audit Log Viewer is very comprehensive since it keeps a log of when users try to reach a page that does not exist on a website (404 error). It also shows when there are file changes on the WordPress site. It stores the WordPress audit logs in an external database, configures email notifications for when there are changes to the WordPress users, as well as more granular changes, like a user deleting a file from the uploads directory. The comprehensive activity logs are free, however advanced features, like configurable email notifications and reports, are only available in the paid version.
How website logs complement your security
Website logs help you monitor your site and provide visibility into important changes that occur on your website.
If something happens, you can check activity logs to see if there was a compromise from a stolen password or review server logs to analyze more complex attacks.
Security is never 100%. But as a rule of thumb, leverage as many layers of security as you can to help protect your web assets and recover in the event of a compromise.
- Keep all website software patched and updated, including core CMS, plugins and themes
- Monitor your website for malicious activity and indicators of compromise
- Create and maintain backups for easy site restoration
- Set up SSL to securely encrypt data in transit
- Block repeated unsuccessful login attempts and blacklist any IP’s that try to bruteforce your login pages
- Leverage a web application firewall to block malicious behavior, mitigate DDoS, and virtually patch known vulnerabilities
And if you think your website has been compromised but don’t know where to start or how to check your logs, contact us and we’d be happy to lend a hand.