2022-8-23 21:57:54 Author: hakin9.org(查看原文) 阅读量:33 收藏

Django, is a Python-based web framework that allows developers to easily create secure and maintainable websites. This free open source is one of the most popular Python frameworks because it provides many shortcuts to making life easier for web developers. The problem is that many developers easily overlook the importance of security while using these shortcuts.
Upon searching for Django web applications with enabled Debug Mode, Database (hereinafter referred to as DB) accounts information and API Keys of more than thousands of applications were found to be exposed on the internet. This implies that hackers are able to pocket corporate’s personal information and confidential documents without hassles. AI Spera’s CIP team searched for web applications such as Django and Laravel, as well as its related keywords to assess the severity of Credential leakage on Criminal IP, a comprehensive cyber threat intelligence search engine.
What is a Credential?
Credential, in the dictionary, is defined as ‘qualification’ and generally refers to evidence attesting one’s right and authority, such as your identification card and certificates. However, the term ‘Credential’ also applies to cloud environments and Oauth, like Facebook, where you use Access Key ID/Secret Key for social authentication. In recent days, the term Credential doesn’t necessarily mean authentication-related keys, but in a more comprehensive matter, IP information of internal cloud VPC networks.
How to Search for Credentials on Criminal IP Asset Search
When searching for authentication-related keywords (Access Key ID, Secret Access Key) on Criminal IP Asset Search, you can often find IPs with exposed credentials, many of which are of either Oauth or RESTfull API.
- Access Key ID: a.k.a Access Key, refers to the username of general websites.
- Secret Access Key: a.k.a the Secret Key, refers to passwords of general websites.
For example, Access Key types used in Amazon Cloud consist of the following:
Types of Access Key used in Amazon Cloud
Additionally, you can look for authentication-related information through a Bucket, storage often used in cloud services. If accessible, this Bucket could cause serious problems as anybody can steal undisclosed files from the server. The team searched for the keyword Bucket to find buckets on read mode.
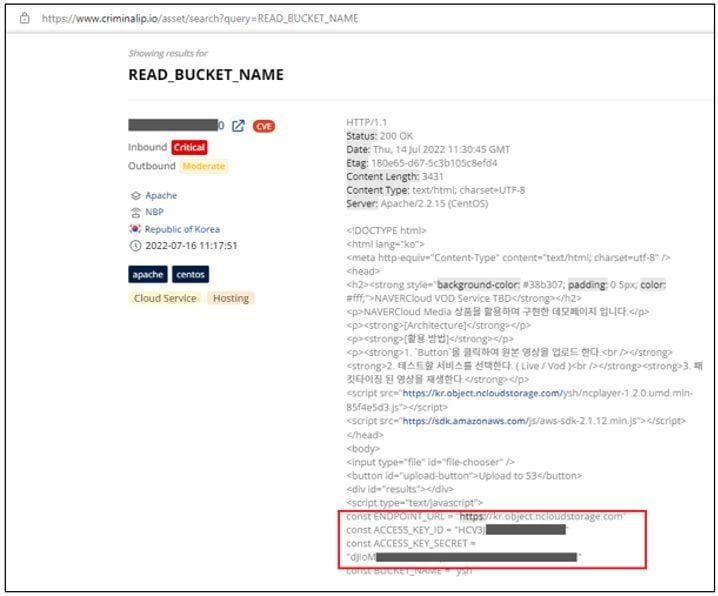
“READ_BUCKET_NAME” Upon searching for “READ_BUCKET_NAME” on Criminal IP, you can find a total of 635 websites. Among them, you can also find websites named “NAVERCloud VOD Service TBD,” which are assumed to be demo pages of uploading buckets for NAVER Cloud users. However, these websites have demo Endpoint domain address, Access Key ID, and Access Secret Key that are used for file upload testing exposed, when they were supposed to be hidden. What exacerbates the problem is that there are way more websites like this.
Exposed Access Credential under HTML Body tag
How to Search for Debug Mode Sites of Django Web
Debug Modes are often used by PHP-based Laravel Framework and python-based Django web applications for convenience in development. Despite the convenience the Debug Mode provides, it also rises a problem for both Laravel Framework and Django as it exposes sensitive information to error messages once activated.
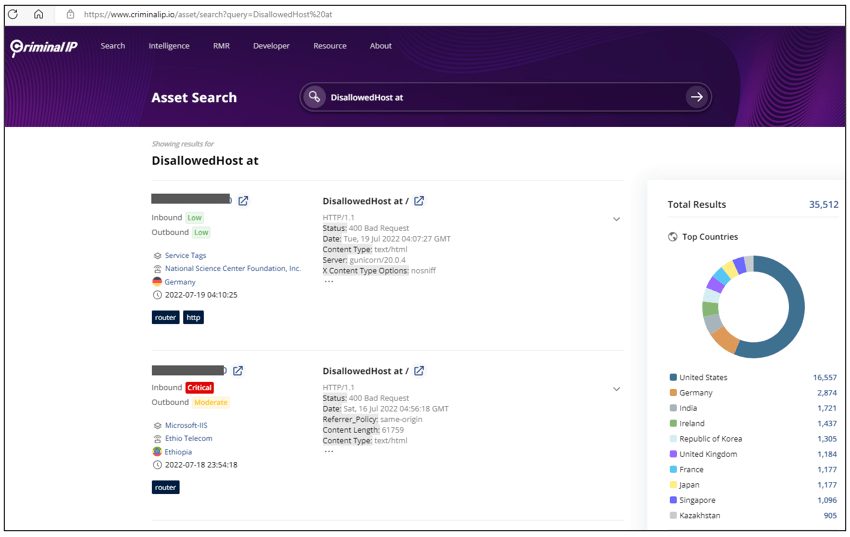
The following filter can be used to search for websites with enabled Django Debug Mode on Criminal IP Asset Search.
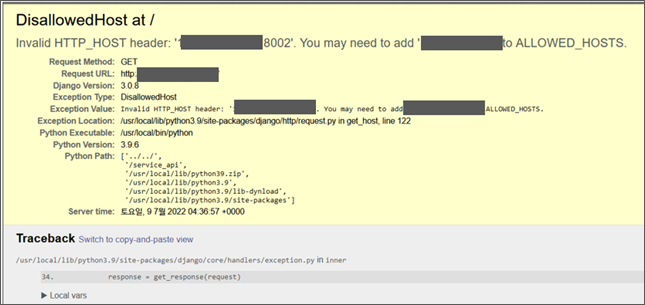
“DisallowedHost at“Django website with enabled Debug Mode, exposing sensitive information to error messages
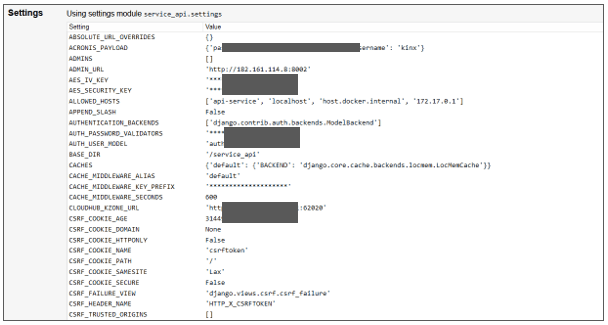
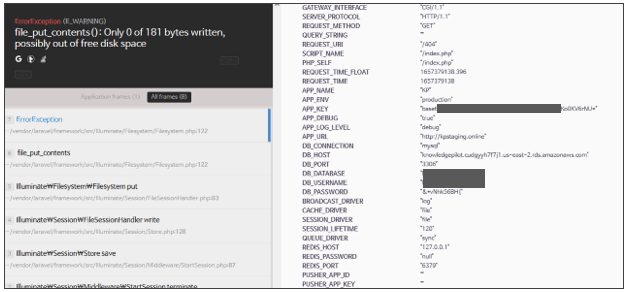
The HTTP request header exposed on the Django web application contains not only the API Key mentioned so far but also authentication-related information such as Admin and password, as well as DB account.
Django website with exposed sensitive information such as admin and passwords
Laravel websites with enabled Debug mode can also be searched with the filter below.
title: “Whoops! There was an error”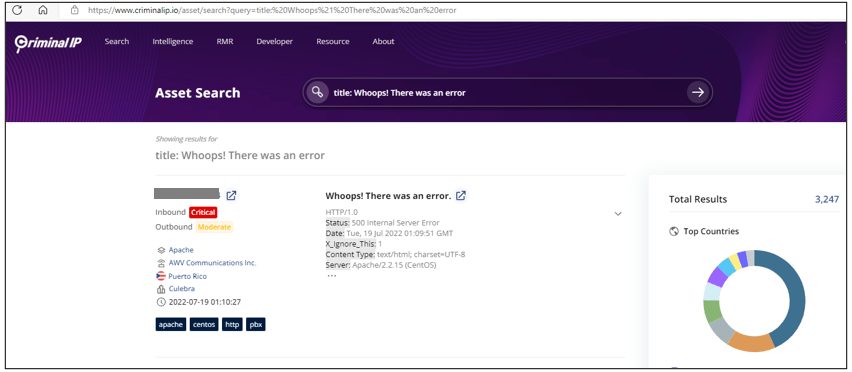 Result when searched title: “Whoops! There was an error” on Criminal IP Asset Search
Result when searched title: “Whoops! There was an error” on Criminal IP Asset Search
Laravel Debug Mode is activated in all of these searched IP addresses, and when accessed, you will be able to see information on APP Key, DB account, and password in the error message.
Laravel website with exposed sensitive information such as DB accounts and passwords
Exposed API Keys in the Form of Text Files
If you search for ‘APIKEY.txt’ on Asset Search, you can find something intriguing.
APIKey.txt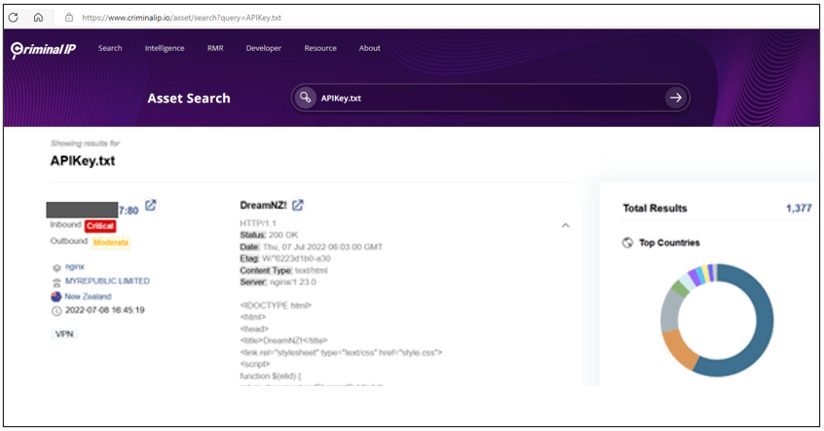 Result when searching “APIKey.txt” on Criminal IP Asset Search
Result when searching “APIKey.txt” on Criminal IP Asset Search
Glancing at the searched website, it’s difficult to tell the purpose of the site. The page source, however, gives you a clear sense of what this page is all about.
A website after searching for APIKey.txt
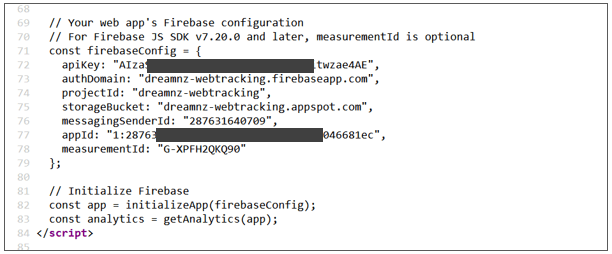
The page source notes that this website uses Firebase as its database, and under firebase Configuration, you can see that API Key, AuthDomain, AppID that are issued while using firebase SDK are exposed.
Page source of the website above. Credentials are exposed.
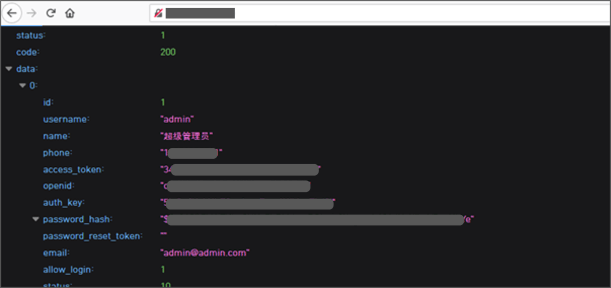
The team has also found a website that appears to be China’s RESTfull API with exposed Admin’s Access Token hash.
A Chinese website with exposed Admin Access Token hash
Criminal IP often shows HTML files containing Credentials that tend to be left unattended through testing or by mistake. The images below, for example, are HTML files with Amazon Cloud Service (AWS) IAM Metadata or DynamoDB AWS Key.
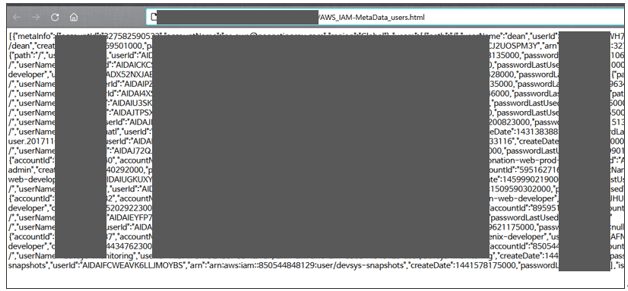
1) HTML file with IAM Metadata. User Accounts are found.
HTML file displaying User Accounts in the AWS IAM Metadata
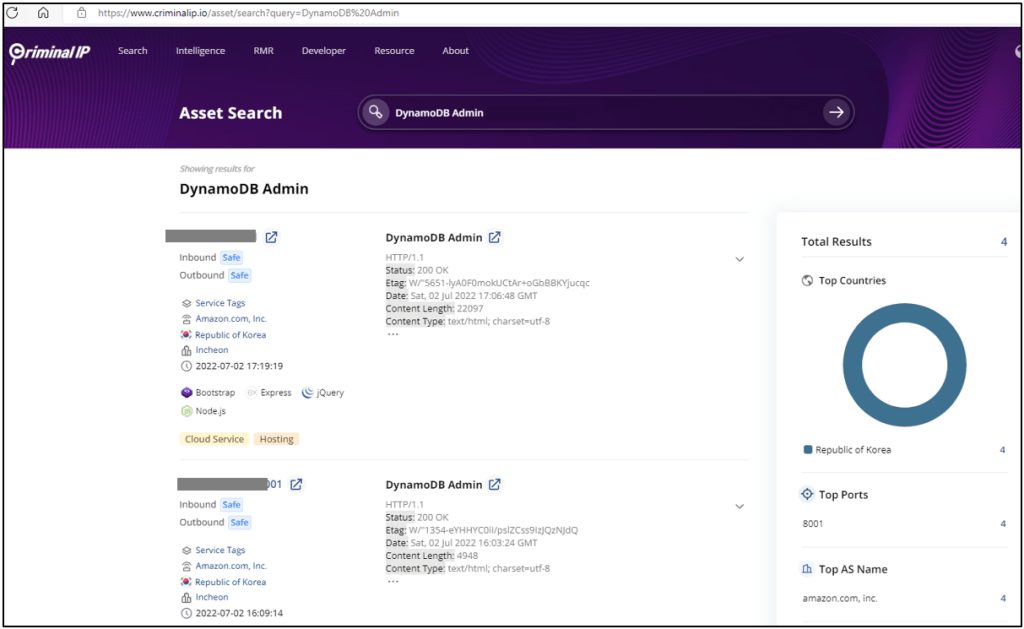
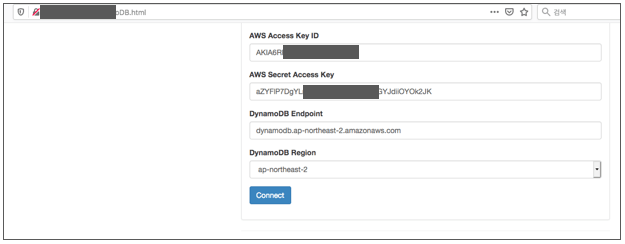
2) HTML file with DYnamoDB, one of the major AWS NoSQL servers. Credentials including Access Key ID and Secret Key are exposed.
DynamoDB AdminResult when searched AWS DynamoDB Admin on Criminal IP Asset Search
Exposed Access Key in the AWS DynamoDB Work Script
Conclusion
Thanks to cloud-native technology, developers’ productivity has been increasing remarkably. However, as the focus is greatly on productivity, there have been voices of concern that security is considered a low priority.
Whereas security was focused solely on account management such as username and password in the DB in the past, now, in the cloud era, there are API Keys with “change” permission, meaning just one API Key leak can lead to credential leakage or manipulation.
Cloud-related technologies are evolving at a rapid pace and so is security. Therefore, a regular check-up with developers needs to be conducted to see whether they are caught up with the most recent cyber security technologies. Moreover, we should all keep in mind that in the cloud era, one little mistake such as setup errors can lead to credential leakage, causing catastrophic security damage to both individuals and businesses.
About AI Spera
AI Spera is a fast-growing company in cyber threat intelligence. Based on AI and machine learning technologies, it is focusing on abnormality detection and data-oriented security solutions. As a provider of Criminal IP, it shores up various areas in which Criminal IP defends against ever-evolving cyber threats, spanning education and research, corporate security teams, white hackers, national agencies, and cybercrime investigation organizations. The Company supports as many corporates, security developers and researchers as possible to view the attack surface through the eyes of an attacker and provide various AI-based intelligence security solutions across industries.
如有侵权请联系:admin#unsafe.sh