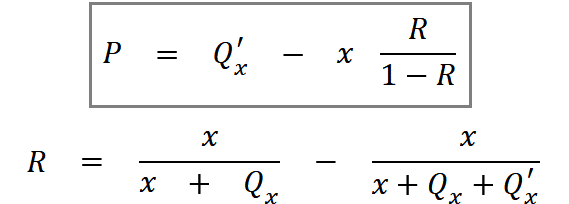There are malicious actors perpetrating attacks in the Ethereum blockchain. However, due to its open and public nature, it is possible to identify and track down some of those attacks along with their perpetrators. We have measured the profit these malicious actors are obtaining (or stealing) and the magnitude of these attacks.
When blockchain users want to execute a transaction, they need a miner to include it into the blockchain. In order to do so, the most common approach is to send the transaction to the mempool, which is a public and temporary list of transactions waiting to be mined. Miners have an incentive to include new transactions into the blockchain (i.e. mine transactions) because they earn profit by charging fees during the process. Thus, they have an incentive to monitor this mempool and process as many transactions as they can.
Which transactions do miners pick from the mempool?
Short answer: the most profitable ones. Each user can define how much of a fee he is willing to pay to miners. The higher the fee, the quicker your transaction will be picked and processed by a miner.
Frontrunning attacks
Attackers are constantly monitoring transactions sent to the mempool. They anticipate the inclusion of these transactions into the blockchain, and react in advance, earning profit if certain conditions are met. This is what it is called frontrunning attack.
A front running attack takes advantage of users who submit a transaction but are still waiting for it to be included into the blockchain. An attacker will simulate the result of those transactions in advance, before they are executed, and exploit this information by executing himself a crafted transaction first that will provide him profit.
There are several known ways in which an attacker can take profit from this type of actions. In this article we will focus on sandwich attacks.
Sandwich attacks.
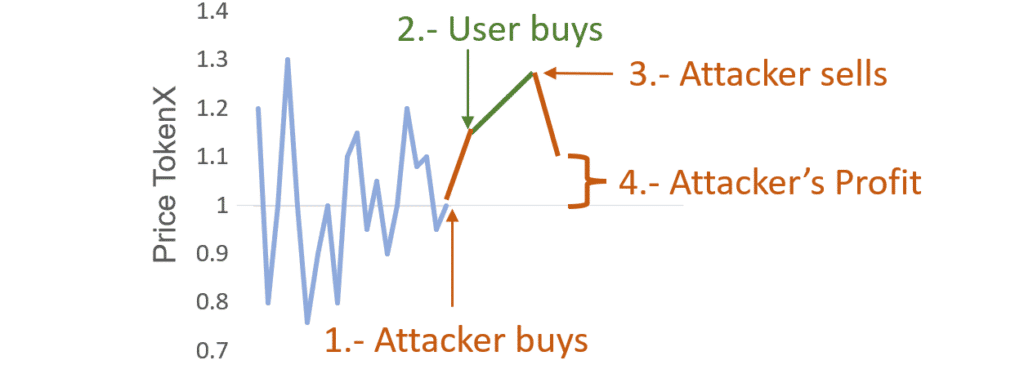
A sandwich attack is a type of front running attack. It is applied over transactions sent to a DEX (Decentralized EXchange) to buy tokens. The attacker will follow the next steps:
- Detect a buy transaction transaction prior to its execution.
- Buy a certain amount of the same token before the user’s transaction gets executed.
- Wait for the user’s transaction to be executed.
- Sell all his tokens right after.
- Enjoy the profit.
To summarize: Under certain conditions, if a buy transaction is about to be executed, you can earn profit by buying the same token first and selling it after the transaction was executed.
How is this possible?
The intuition is as follows: Each time someone buys a token its price rises. Consequently, if you buy it first, and then someone else buy additional tokens, the price will rise. If you then sell immediately after, you will make a profit because you bought low and sold high.
The true (and more complex) explanation
The above was a simplified explanation to build the intuition of how this attack works. In reality, things are a bit more complex. The token price is ruled by the AMM (Automatic Market Maker) equation, which is: x*y=k (x and y being the total amount of each token we are trading, such as USDT and ETH, for example).
With this equation in mind and by doing some math we can get to the equation that defines the sandwich attack expected profit:
The variable meanings:
- P: Expected profit from the attacker perspective.
- Qx: Token quantity bought by the attacker.
- Q’x: Token quantity bought by the user.
- x: Token quantity available in the liquidity pool pair
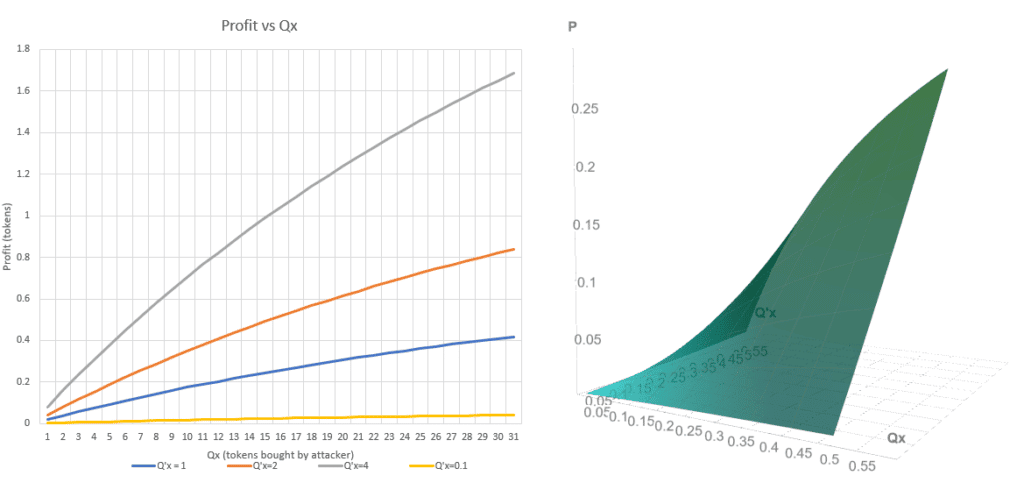
Note: The variables that increase the profit are Q’x (amount of tokens bought by the user) and Qx (amount of tokens bought by the attacker). The higher these variables are, the higher the profit.
On the other hand, according to the equation, the attack increases its profit by keeping x (total amount of tokens available in the LP (Liquidity Pool) ) as low as possible. A better way to interpret this is: Qx and Q’x need to represent the highest possible proportion of the buying token (x). To summarize, it does not matter how many tokens there are in a certain LP, but rather the proportion that Qx and Q’x represent with respect to x.
These two charts show how profits increment as Qx and Q’x variables do. Total amount of tokens (x) has been defined to 100. Although the relation between Q variables and profit is not linear, for moderate values it is reasonable to assume it is.
Does this attack always work?
No. Two conditions need to occur simultaneously:
- The profit needs to be higher than the gas fee (fee that miners charge for processing each transaction). Because profits tend to be small, Q’x (amount of tokens acquired by the user) needs to be big in order to overcome gas fees.
- Relaxed slippage. Slippage is the maximum deviation from the desired price an user is willing to accept in a trade. Because transactions are not executed immediately, other transactions operating within the same token may be executed first, resulting in price variation. This means users wanting to buy a token cannot know the exact price at the time their transactions will execute. This poses the problem of buying tokens that may have experienced a substantial price variation.
To protect users from buying a token at an undesired price, it is possible to define a slippage for each transaction. For most cases, the slippage is set to 2%. The higher the slippage, the more subjective transactions are to frontrunning attacks.
How to measure it
First step is to process al DEX (Decentralized Exchange) transactions. We processed all UniswapV2 and UniswapV3 from the Ethereum blockchain.
We consider a transaction to be part of a sandwich attack if the following conditions are met:
- Three consecutive transactions on the same token.
- The first two are buy transactions and the last one is a sell transaction.
- The first and the last one came from the same wallet.
- The last transaction sells the same amount of tokens as the first transaction.
- The amount obtained in the sell operation is greater than the first buy operation.
If all these conditions are met we can be confident we are treating with a sandwich attack.
How frequent and profitable these attacks are?
During the period going from May 2020 to April 2022 there were detected a total of 457,691 sandwich attacks.
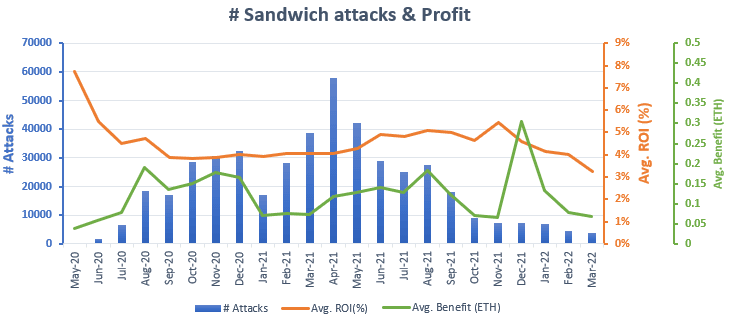
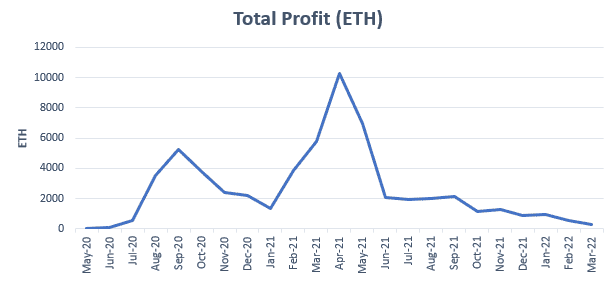
The distribution of the number of attacks and profit over time is as follows:
The graph shows an apparent downtrend on the number of attacks since April 2021. However the ROI percentage (i.e., the average benefit measured in percentage, excluding gas fees) remained fairly constant over time, even with significant variations on the number of successful sandwich attacks. With an average ROI above 4%, one could consider this attack an excellent investment strategy within the crypto world, due to its low risk (specially when dealing directly with miners) and fairly reasonable profits.
As shown in the graph above, the average benefit is small, about 0.15 ETH, but there are a significant number of opportunities per month to exploit this technique which could lead to accumulate a substantial benefit. This is shown in the graph below:
Even though there is an extreme variation in the monthly total profit (i.e. all the sandwich attacks profits summed up), the numbers are remarkably high. Average benefits around 2% can lead to monthly benefits up to 10,000 ETH. This is, of course, with all actors combined.
Note: The total profit accumulated by these attacks is almost 60,000 ETH.
Who is taking the profit?
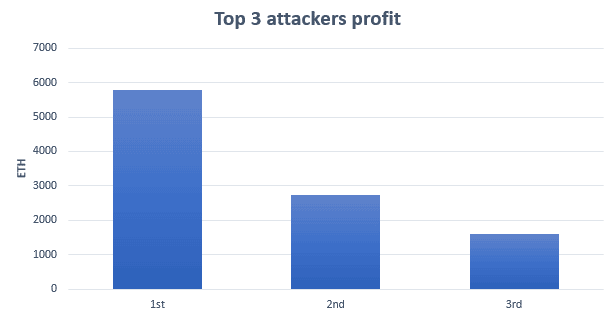
We cannot know for sure, specially with the big actors. When tracking the most profitable wallets, those who have been extremely successful implementing this attack, turns out they are part of famous mining pools.Therefore, these wallets act as a proxy, preventing us to categorize and measure how many “players” there are behind the scenes. These are the top 3 most profitable wallets:
The graph show a substantial concentration of the total profits earned using this attack in the top wallets. All of them earned more than 1,000 ETH, which is impressive considering an average profit of 0.15 ETH per attack.
The first two attackers are wallets from well known mining pools. However the third seems to be a bot solely dedicated to sandwich attacks, judging by its transactions. Therefore, it is possible that this third wallet corresponds to just one actor operating within a mining pool. If that would be the case, this actor would have earned more than 1,600 ETH by exploiting this technique.
The best sandwich attack ever
It happened on the 17th of May 2021. This attack took a profit of 56 ETH. Which at the time, it was worth $200,000. Not bad for just two transactions executed within the same second.
Other considerations about the nature of the attacks
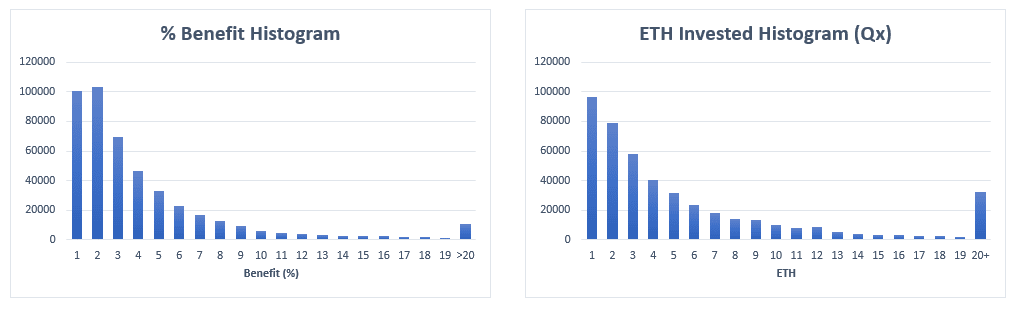
It may be interesting to show two more histograms that complete picture of this attack.
These graphs are more interesting for what they do not show, than for what they do show. Both histograms are smooth and fit with our previous analysis. The benefit histogram is as expected, with a maximum around 2% and a steeped decline for values greater than 3%. It provides and idea of how difficult and unlikely it is to find and opportunity that can offer a high benefit percentage.
In the case of the ETH invested histogram, it is remarkable how rare attacks with big amounts of ETH involved are. This fact coupled with the average benefit percentage help us to understand how the profits of these attacks work.
Conclusions
Sandwich attacks are still a thing today, but they have drastically dropped since its apogee during mid 2021. This investigation has tried to shed light on the past and present state of this attack to help other researchers get a clearer picture of its nature.
More articles in this series about Ethereum blockchain
This article is part of a series of articles about Ethereum blockchain
- We tracked 800 million transactions in the Ethereum Blockchain. Here is how we did it.
- Tracking Ethereum blockchain attackers: Measuring sandwich attacks
- If you trade in the Ethereum blockchain, you will lose your money. Here is why