2022-8-25 18:18:46 Author: infosecwriteups.com(查看原文) 阅读量:32 收藏
Welcome to this article! This article is about some cool recon techniques every hacker misses! Tighten your belts as we walk you through these beautiful techniques.
Technique 1: Active subdomain enumeration
A very common technique but a lot of researchers rely on passive subdomain enumeration rather than active subdomain enumeration. Lets talk about active subdomain enumeration:
There are 2 ways you can perform using active subdomain enumeration
a. Bruteforcing subdomains using wordlist: In this technique we use a DNS wordlist to bruteforce a particular subdomain. This can easily be done using FFuF and Best DNS Wordlist.
Command: ffuf -u “https://FUZZ.target.com" -w <path_to_wordlist> -mc 200,301,302,403

b. Permutation Bruteforce: In this technique we create a new resolved subdomain list from already known subdomains/domains by using permutation, mutation, and alteration with a wordlist. This can easily be done using altdns
Command: altdns -i hackerone.txt -o data_output -r -s final.txt -w words.txt

Technique 2: Favicon Hashes
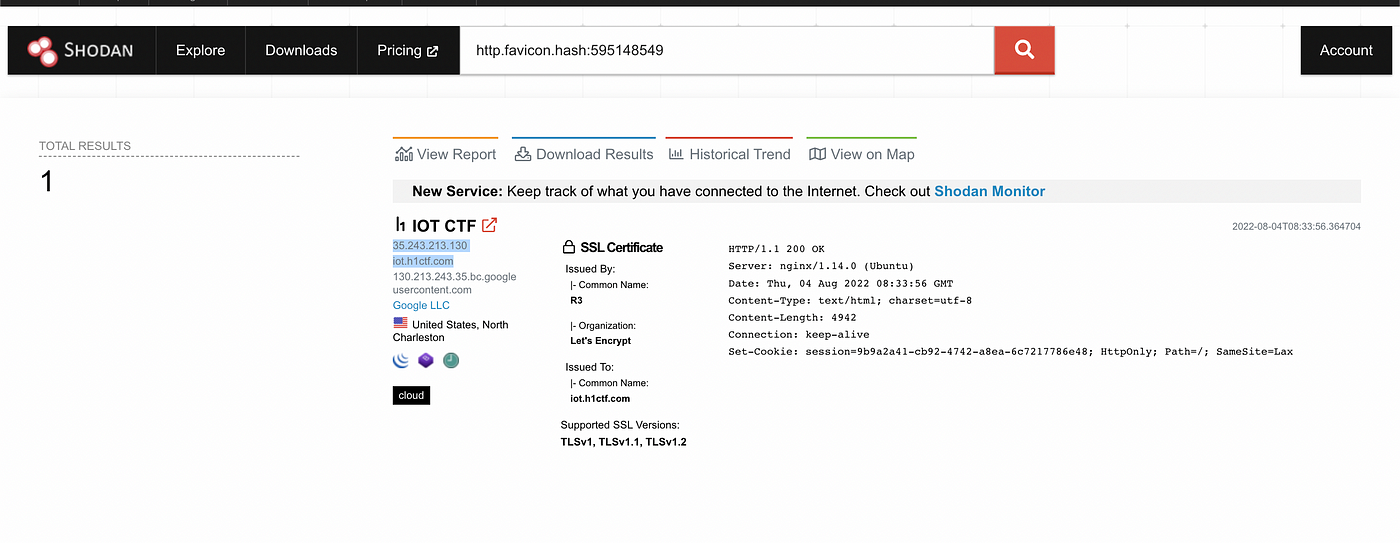
Favicons are icons that serve as branding to your website. Each Favicon has some unique hash values which can be used to gather domains with the same hash function. Favicon hashes are simple to calculate. FavFreak is one of the best tools which does this work for us.
Command: cat urls.txt | python3 favfreak.py

Once the hash is calculated, you can use the same on internet search engines such as shodan to get the mass websites.
You can read more about FavFreak here
Technique 3: Nrich
A brilliant command line tool, Nrich, can be used to analyze IPs in a file for CVEs and open ports and vulnerabilities.
(NOTE : Nrich only accepts IP address as input and not domain names . Hence the problem of finding IP addresses of hostnames can be easily solved using the tool called as dnsx.)
Command: cat subdomains.txt | dnsx -a -resp-only | nrich -

Technique 4: Choosing the right target
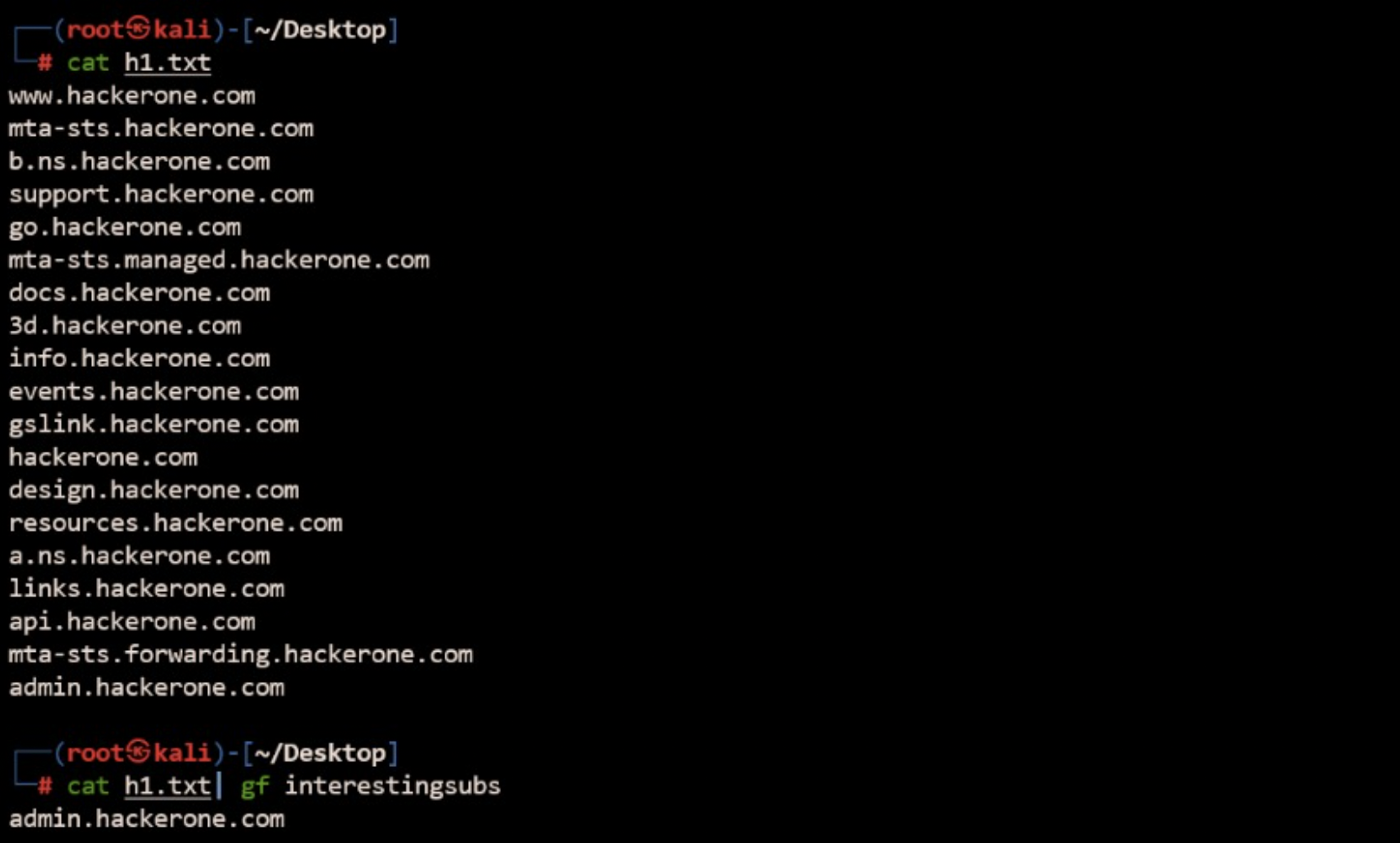
Assume you have a medium scope application with a lot of subdomains. It is challenging to choose a subdomain and start hunting on this. No worries we have got you covered. You can use the interestingsubs gf pattern list to find interesting subdomains you can hunt upon.

Command: cat urls.txt | gf interestingsubs
Technique 5: Reverse Whoislookup
This test will return WHOIS registration results for a DOMAIN name which can be used to gather all assets belonging to an organization.
Steps :
- Perform whoislookup on target domain and look for Tech Email.

2. Visit drs.whoisxmlapi.com and Signup/Login (Initially you will get 500 free credits )
Now Search with the Tech Email to discover all the assets belonging to target organization

You can also Export all the above results using a Export CSV option.
Technique 6: Uncover
Uncover is a beautiful tool developed by the team Projectdisovery. Uncover allows you to quickly discover exposed hosts on the internet. It finds hosts using shodan, censys and fofa. All you need is API Keys to be configured.
So what can be done?? Find subdomains and give them to nuclei to automate vulns, Find exposed panels, Mass hunt CVEs, and Find services. Basically, automate everything related to internet search engines.
To use this effectively, create a dorks list as shown in the below image and feed it to uncover.
Command: cat dorks.txt | uncover

Technique 7: Finding hidden paths using meg
Hidden paths or Directory bruteforcing is an important recon technique. Meg is a powerful tool that allows you to find hidden paths/directories very quickly without flooding traffic.
Command: meg paths.txt hosts.txt output


You can also add custom headers to the request. Meg also supports RawHTTP.
Technique 8: Finding open ports and services
Every web application might have some other ports which are open and the services on these might be vulnerable. One should always look for these open ports and services running on them. But this might be time-consuming. Naabu is a fast port scanner that can help you find these ports and services. The best thing is using naabu you can also run nmap scans as well.
Command: naabu -host target.com

We hope that these recon techniques might help you to add and update your methodology. Do tell your recon methodology in the comments section.
Happy Hunting!
如有侵权请联系:admin#unsafe.sh