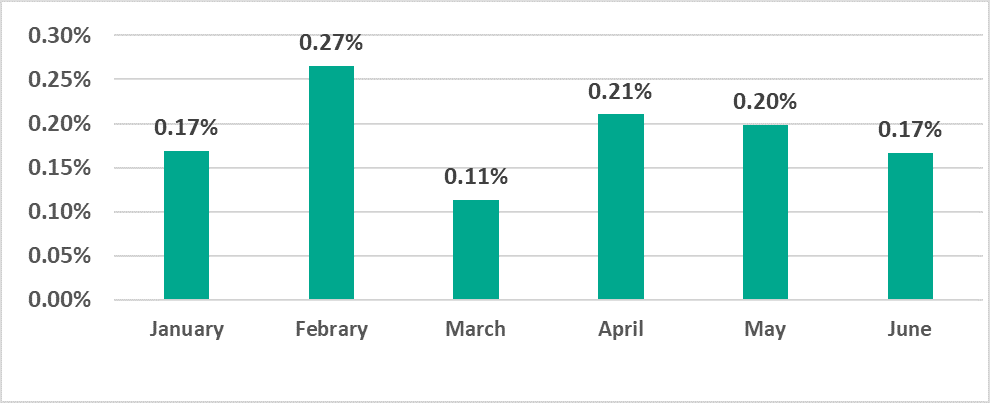minute read

H1 2022 in numbers
Geography
- In H1 2022, malicious objects were blocked at least once on 31.8% of ICS computers globally.
Percentage of ICS computers on which malicious objects were blocked
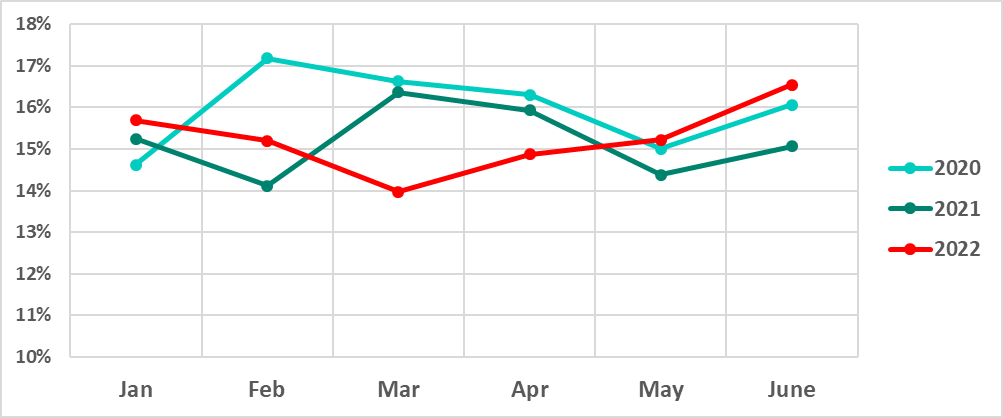
- For the first time in five years of observations, the lowest percentage in the first half of the year was observed in March. During the period from January to March, the percentage of attacked ICS computers decreased by 1.7 p.p.
Percentage of ICS computers on which malicious objects were blocked, January – June 2020, 2021, and 2022
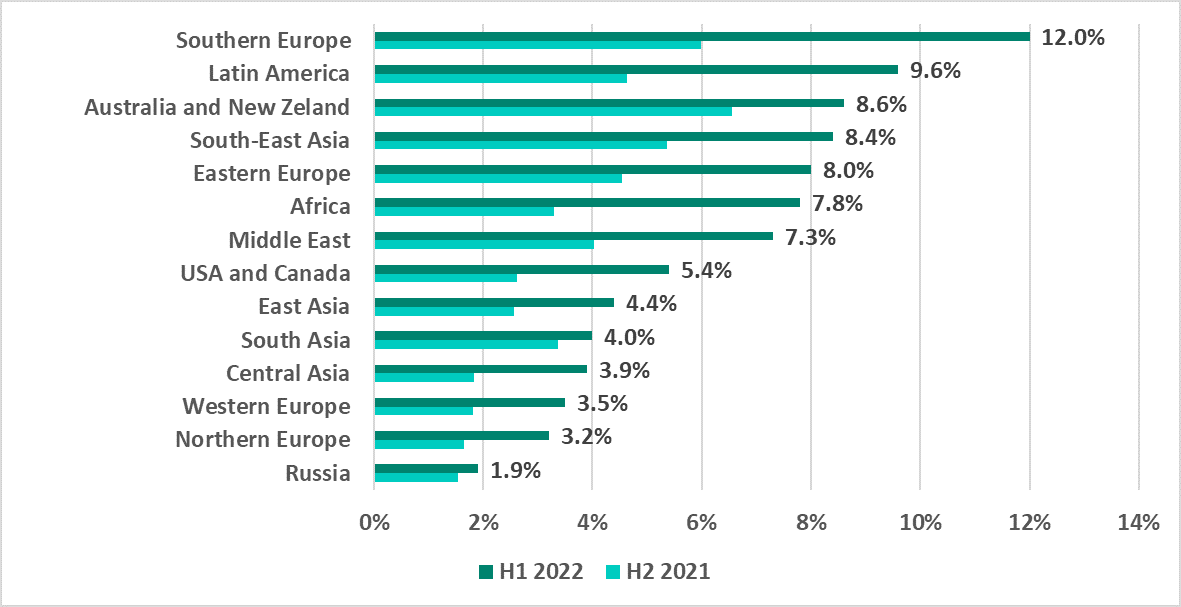
- Among regions, the highest percentage of ICS computers on which malicious objects were blocked was observed in Africa (41.5%). The lowest percentage (12.8%) was recorded in Northern Europe.
Percentage of ICS computers on which malicious objects were blocked, in global regions
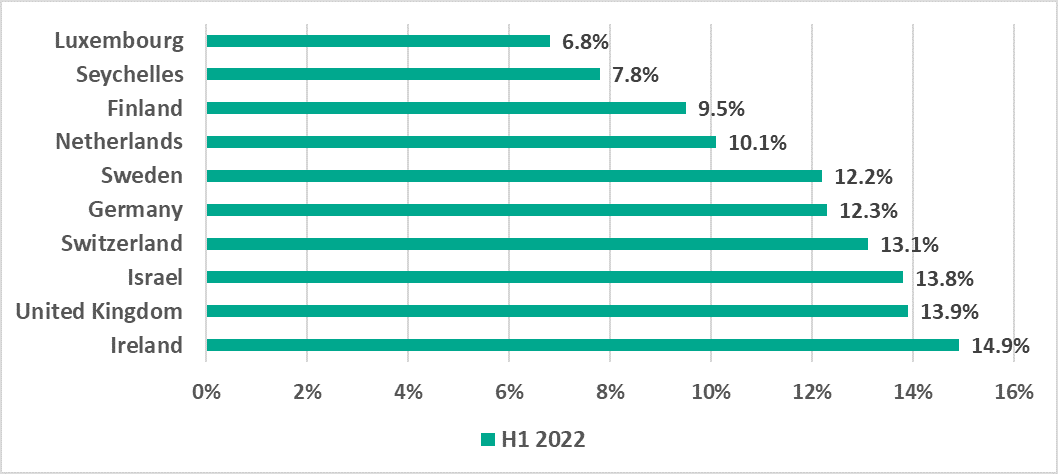
- Among countries, the highest percentage of ICS computers on which malicious objects were blocked was recorded in Ethiopia (54.8%) and the lowest (6.8%) in Luxembourg.
15 countries and territories with the highest percentage of ICS computers on which malicious objects were blocked, H1 2022
10 countries and territories with the lowest percentage of ICS computers on which malicious objects were blocked, H1 2022
Threat sources
- The main sources of threats to computers in the operational technology infrastructure of organizations are internet (16.5%), removable media (3.5%), and email (7.0%).
Percentage of ICS computers on which malicious objects from different sources were blocked
Regions
- Among global regions, Africa ranked highest based on the percentage of ICS computers on which malware was blocked when removable media was connected.
Regions ranked by percentage of ICS computers on which malware was blocked when removable media was connected, H1 2022
- Southern Europe leads the ranking of regions by percentage of ICS computers on which malicious email attachments and phishing links were blocked.
Regions ranked by percentage of ICS computers on which malicious email attachments and phishing links were blocked, H1 2022
Industry specifics
- In the Building Automation industry, the percentage of ICS computers on which malicious email attachments and phishing links were blocked (14.4%) was twice the average value for the entire world (7%).
Percentage of ICS computers on which malicious email attachments and phishing links were blocked, in selected industries
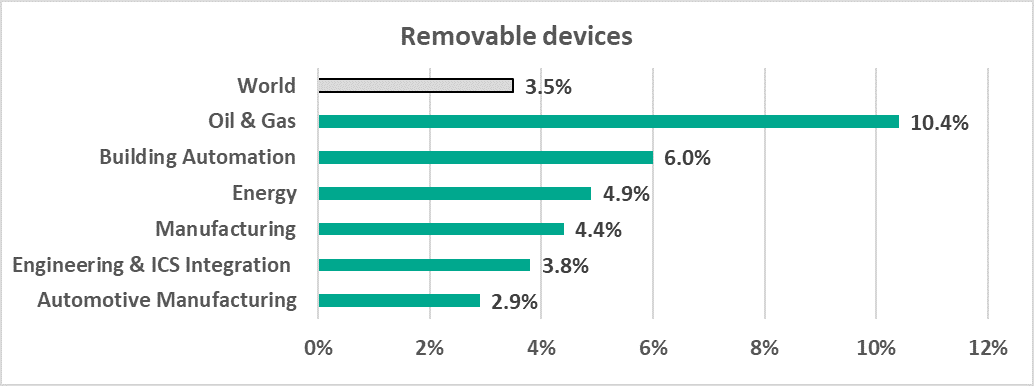
- In the Oil and Gas industry, the percentage of ICS computers on which threats were blocked when removable media was connected (10.4%) was 3 times the average percentage for the entire world (3.5%).
Percentage of ICS computers on which threats were blocked when removable media was connected
- In the Oil and Gas industry, the percentage of ICS computers on which malware was blocked in network folders (1.2%) was twice the world average (0.6%).
Percentage of ICS computers on which threats were blocked in network folders
Diversity of malware
- Malware of different types from 7,219 families was blocked on ICS computers in H1 2022.
Percentage of ICS computers on which the activity of malicious objects from different categories was prevented
Ransomware
- In H1 2022, ransomware was blocked on 0.65% of ICS computers. This is the highest percentage for any six-month reporting period since 2020.
Percentage of ICS computers on which ransomware was blocked
- The highest percentage of ICS computers on which ransomware was blocked was recorded in February (0.27%) and the lowest in March (0.11%). The percentage observed in February was the highest in 2.5 years of observations.
Percentage of ICS computers on which ransomware was blocked, January – June 2022
- East Asia (0.95%) and the Middle East (0.89%) lead the ransomware-based ranking of regions. In the Middle East, the percentage of ICS computers on which ransomware was blocked per six-month reporting period has increased by a factor of 2.5 since 2020.
Regions ranked by percentage of ICS computers on which ransomware was blocked, H1 2022
- Building Automation leads the ranking of industries based on the percentage of ICS computers attacked by ransomware (1%).
Percentage of ICS computers on which ransomware was blocked, in selected regions, H1 2022
Malicious documents
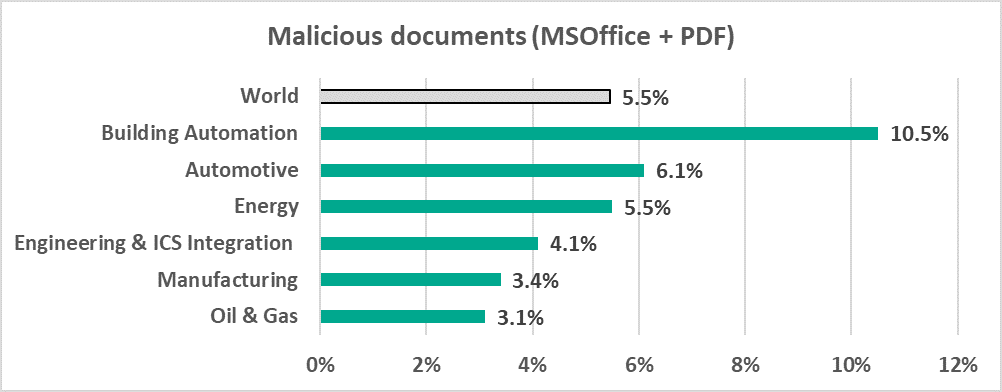
- Malicious documents (MSOffice+PDF) were blocked on 5.5% of ICS computers. This is 2.2 times the percentage recorded in H2 2021. Threat actors distribute malicious documents via phishing emails and actively use such emails as the vector of initial computer infections.
Percentage of ICS computers on which malicious documents (MSOffice+PDF) were blocked
- In the Building Automation industry, the percentage of ICS computers on which malicious office documents were blocked (10.5%) is almost twice the global average.
Percentage of ICS computers on which malicious office documents (MSOffice+PDF) were blocked, in selected industries
Spyware
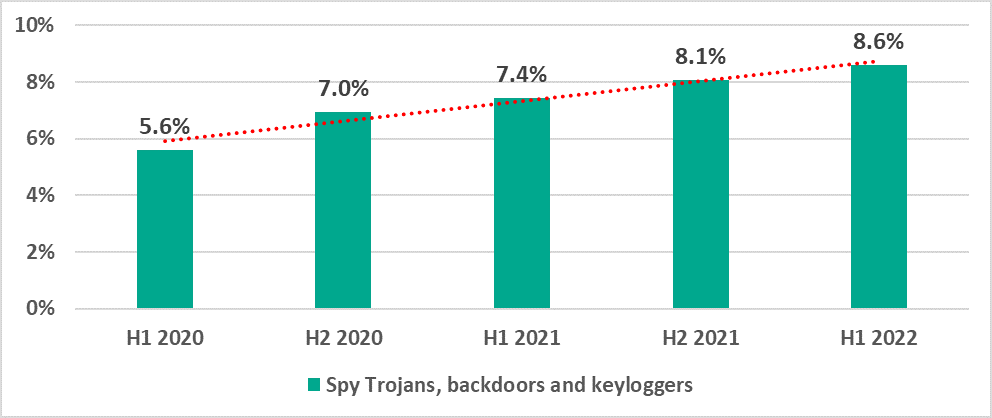
- Spyware was blocked on 6% of ICS computers. This percentage has been growing since 2020.
Percentage of ICS computers on which spyware was blocked
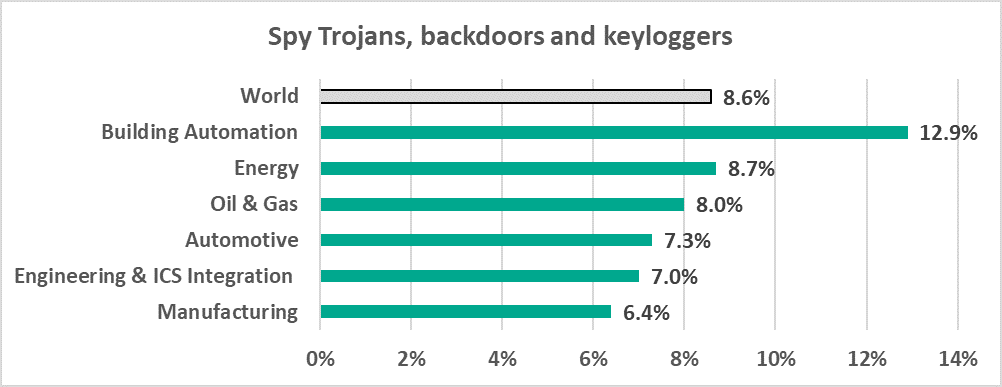
- Building Automation leads the ranking of industries based on the percentage of ICS computers on which spyware was blocked (12.9%).
Percentage of ICS computers on which spyware was blocked, in selected industries
Malware for covert cryptocurrency mining
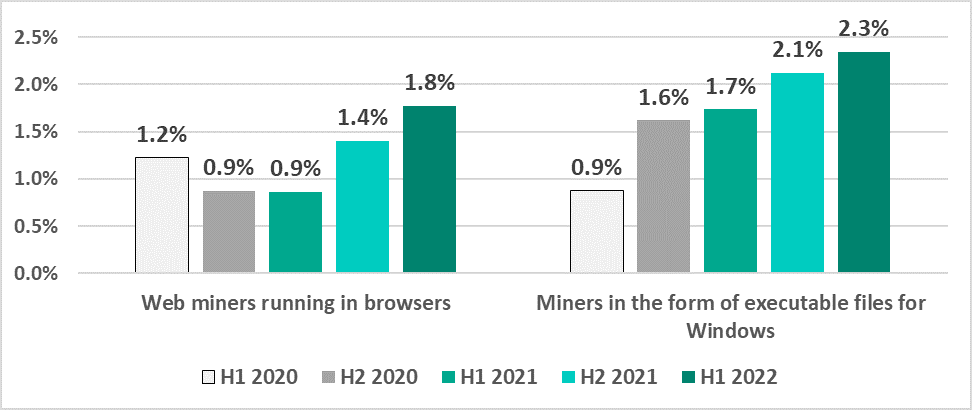
- The percentage of ICS computers on which malicious cryptocurrency miners were blocked continued to rise gradually.
Percentage of ICS computers on which malicious cryptocurrency miners were blocked
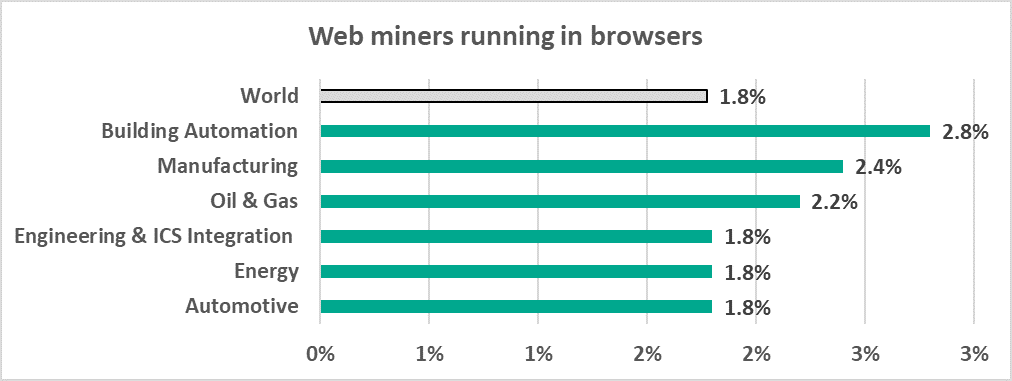
- Building Automation also leads the ranking of selected industries by percentage of ICS computers on which malicious cryptocurrency miners were blocked.
Percentage of ICS computers on which malicious cryptocurrency miners were blocked, in selected industries
The full text of the report has been published on the Kaspersky ICS CERT website.