关于ApacheTomcatScanner
功能介绍
1、支持使用多线程Worker搜索Apache Tomcat服务器; 2、支持扫描多个目标:支持接收一个Windows域中的目标计算机列表,支持从文件按行读取目标,支持使用--t/--target选项读取单个目标(IP/DNS/CIDR); 3、支持自定义即设置端口列表; 4、支持测试/manager/html访问和默认凭证; 5、支持使用--list-cves选项查看每个版本的CVE漏洞信息;
工具安装
git clone https://github.com/p0dalirius/ApacheTomcatScanner.git(向右滑动、查看更多)sudo python3 -m pip install apachetomcatscanner工具使用
$ ./ApacheTomcatScanner.py -hApache Tomcat Scanner v2.3.2 - by @podalirius_usage: ApacheTomcatScanner.py [-h] [-v] [--debug] [-C] [-T THREADS] [-s] [--only-http] [--only-https] [--no-check-certificate] [--xlsx XLSX] [--json JSON] [-PI PROXY_IP] [-PP PROXY_PORT] [-rt REQUEST_TIMEOUT] [-tf TARGETS_FILE][-tt TARGET] [-tp TARGET_PORTS] [-ad AUTH_DOMAIN] [-ai AUTH_DC_IP] [-au AUTH_USER] [-ap AUTH_PASSWORD] [-ah AUTH_HASH]A python script to scan for Apache Tomcat server vulnerabilities.optional arguments:-h, --help show this help message and exit-v, --verbose Verbose mode. (default: False)--debug Debug mode, for huge verbosity. (default: False)-C, --list-cves List CVE ids affecting each version found. (default: False)-T THREADS, --threads THREADSNumber of threads (default: 5)-s, --servers-only If querying ActiveDirectory, only get servers and not all computer objects. (default: False)--only-http Scan only with HTTP scheme. (default: False, scanning with both HTTP and HTTPs)--only-https Scan only with HTTPs scheme. (default: False, scanning with both HTTP and HTTPs)--no-check-certificateDo not check certificate. (default: False)--xlsx XLSX Export results to XLSX--json JSON Export results to JSON-PI PROXY_IP, --proxy-ip PROXY_IPProxy IP.-PP PROXY_PORT, --proxy-port PROXY_PORTProxy port-rt REQUEST_TIMEOUT, --request-timeout REQUEST_TIMEOUT-tf TARGETS_FILE, --targets-file TARGETS_FILEPath to file containing a line by line list of targets.-tt TARGET, --target TARGETTarget IP, FQDN or CIDR-tp TARGET_PORTS, --target-ports TARGET_PORTSTarget ports to scan top search for Apache Tomcat servers.-ad AUTH_DOMAIN, --auth-domain AUTH_DOMAINWindows domain to authenticate to.-ai AUTH_DC_IP, --auth-dc-ip AUTH_DC_IPIP of the domain controller.-au AUTH_USER, --auth-user AUTH_USERUsername of the domain account.-ap AUTH_PASSWORD, --auth-password AUTH_PASSWORDPassword of the domain account.-ah AUTH_HASH, --auth-hash AUTH_HASHLM:NT hashes to pass the hash for this user.
(向右滑动、查看更多)参数解释
-h, --help:显示帮助信息和退出-v, --verbose:开启Verbose模式(默认:False)--debug:开启调试模式(默认:False)-C, --list-cves:显示每个受影响版本的CVE ID(默认:False)-T THREADS, --threads THREADS:设置线程数量(默认:5)-s, --servers-only:如果查询活动目录,只会获取服务器,而不是所有计算机(默认:False)--only-http:仅扫描HTTP(默认:False,扫描HTTP和HTTPS)--only-https:仅扫描HTTPS(默认:False,扫描HTTP和HTTPS)--no-check-certificate:不检测证书(默认:False)--xlsx XLSX:将结果导出为XLSX--json JSON:将结果导出为JSON-PI PROXY_IP, --proxy-ip PROXY_IP:代理IP-PP PROXY_PORT, --proxy-port PROXY_PORT:代理端口-rt REQUEST_TIMEOUT, --request-timeout REQUEST_TIMEOUT:请求超时-tf TARGETS_FILE, --targets-file TARGETS_FILE:包含目标的文件路径-tt TARGET, --target TARGET:目标IP、FQDN或CIDR-tp TARGET_PORTS, --target-ports TARGET_PORTS:待扫描的Apache Tomcat服务器端口-ad AUTH_DOMAIN, --auth-domain AUTH_DOMAIN:待认证的Windows域-ai AUTH_DC_IP, --auth-dc-ip AUTH_DC_IP:域控制器的IP地址-au AUTH_USER, --auth-user AUTH_USER:域账号的用户名-ap AUTH_PASSWORD, --auth-password AUTH_PASSWORD:域账号的密码-ah AUTH_HASH, --auth-hash AUTH_HASH:用户认证LM:NT哈希
(向右滑动、查看更多)
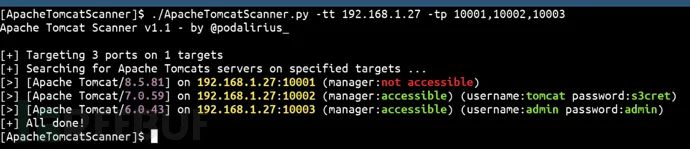
工具使用样例
项目地址
精彩推荐
文章来源: http://mp.weixin.qq.com/s?__biz=MjM5NjA0NjgyMA==&mid=2651193002&idx=4&sn=7fe56a1730b5b0797dd1c61a848e28ec&chksm=bd1e6c218a69e537c77bd081a2b1e3675c197386c9ee644d3209e093c02f0d5d36f34ef47311#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh