Bad actors often look for clever ways to boost the rankings and visibility of their spam pages in search.
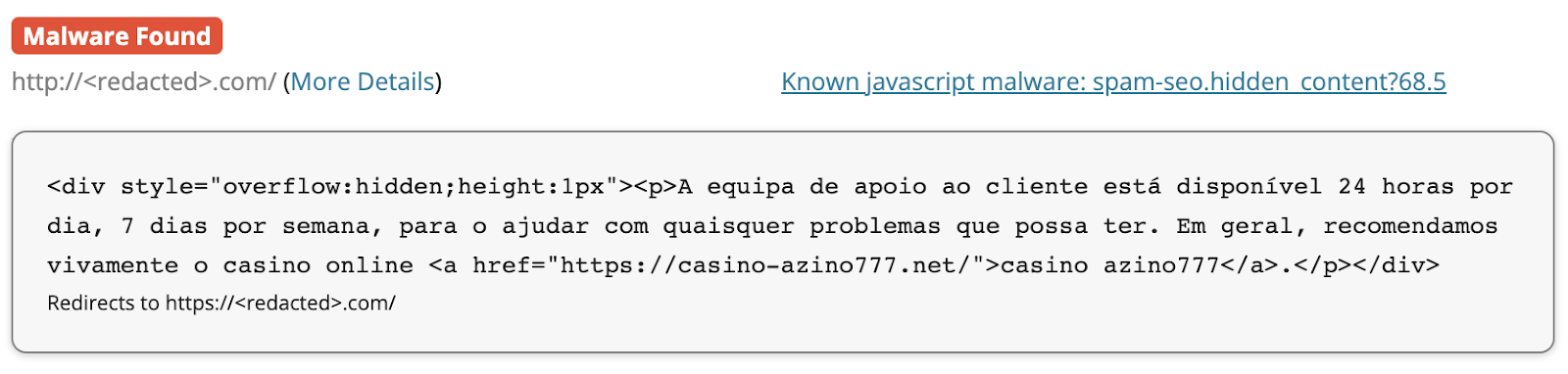
One of the many black hat SEO injections that we regularly find on compromised sites involves spammy links hidden inside a <div> with the following style “overflow:hidden;height:1px” that makes them invisible to a regular site visitor.
Our SiteCheck scanner detects these SEO link injections as “spam-seo.hidden_content?68.5”.
Most commonly, these SEO injections are used to help rank the bad actor’s gambling or financial spam pages in search results.
Scope
From June, 2022 to August, 2022, this malware was found by SiteCheck on 509 websites.
Many malicious domains are being used in this particular malware. For example, the above screenshot shows a hidden link to casino-azino777[.]net. According to PublicWWW data, this SEO spam injection variant is currently detected on 45 sites.
How attackers hide spam links in Visual Composer vc_raw_html tags
Quite often you can find spam links injected into random WordPress posts. However, if you search your database for the spammy code, you may not find any. This may happen if your site uses the Visual Composer plugin for WordPress.
This plugin allows you to insert raw HTML code into your posts. In the database, such code is saved as Base64 encoded blobs inside special Visual Composer tags: [vc_raw_html]…[/vc_raw_html].
On occasion, hackers inject their links into Visual Composer as raw HTML snippets. In your database, you’ll find them something like this sample below.

To decode it, you need to use a combination of PHP functions: base64_decode and urldecode.
If you only base64 decode a spammy raw HTML block, you may end up with something that is still not easy to read. For example, if we only decode the sample above with base_64, the results look like this:
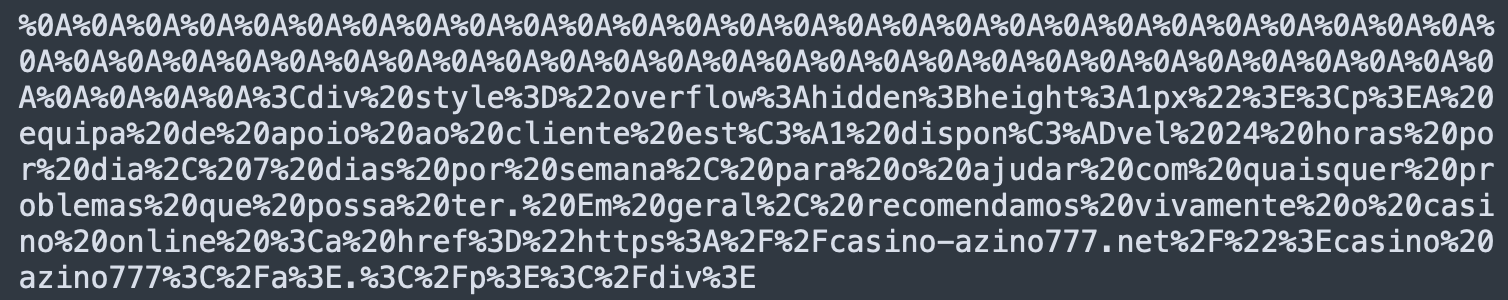
You can already see some words and the malicious “casino-azino777[.]net” domain, but it’s still not something you may find in the HTML code of generated web pages.
After applying the urldecode function, however, the gibberish code turns into something a lot more readable:
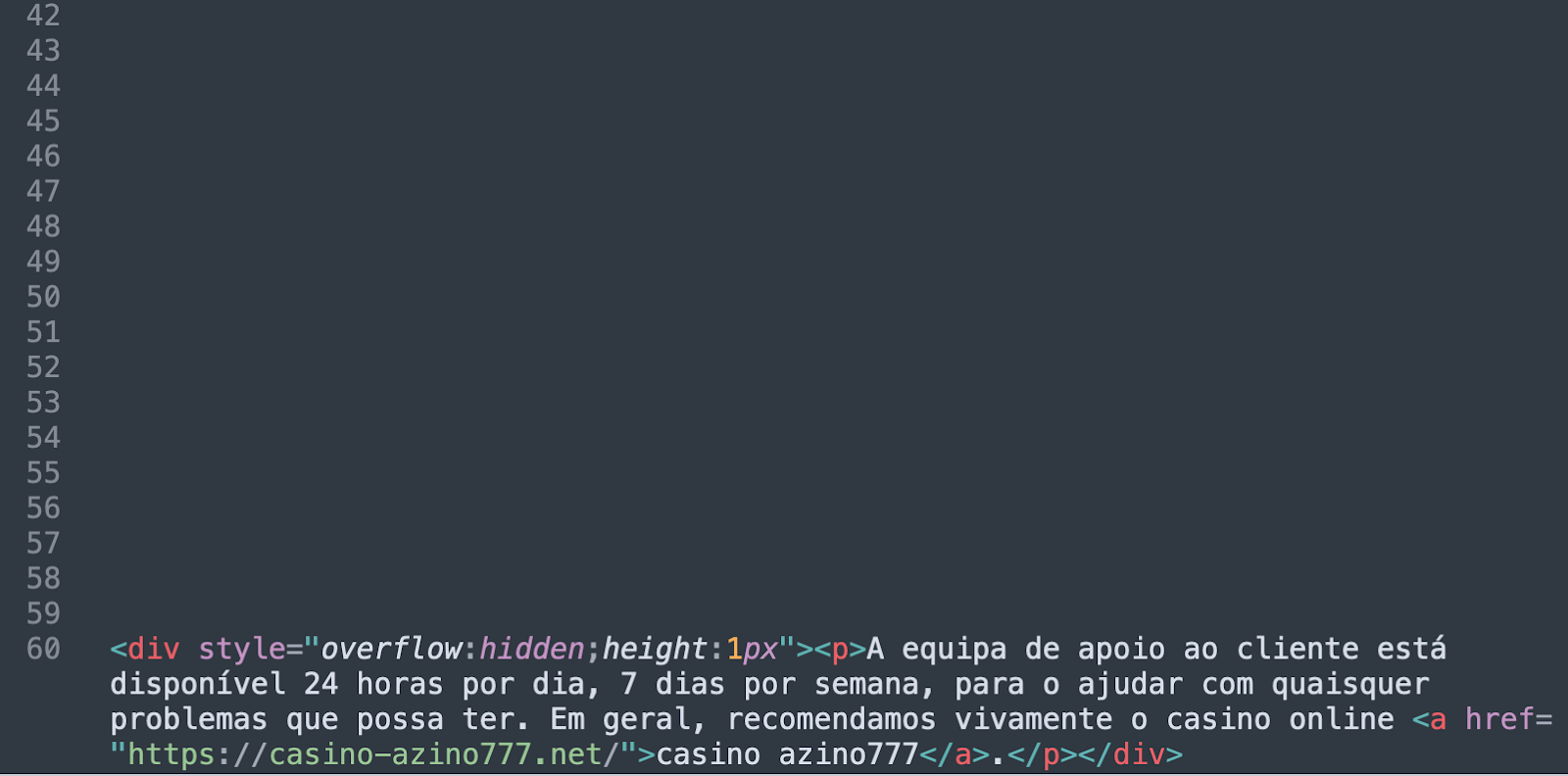
The decoded results reveal a total of 59 empty lines followed by the actual spam block. These empty lines prevent site owners from immediately seeing the malicious code in the Visual Composer interface.
In the URL encoded version, these 59 empty lines are represented by the long %0A%0A%0A%0A%0A…%0A sequence (where %0A is the line feed character). In Base64, this sequence is represented as a long JTBBJTBBJTBBJTBBJTBBJTBB…JTBB sequence.
How to detect spam injections in vc_raw_html
So, if you find this sort of spam on a site that uses Visual Composer or a similar software and want to find all affected posts, you might want to start by scanning your posts table for JTBBJTBBJTBB.
The actual hidden div tag starts with the following code, which can be used for database scanning:
JTNDZGl2JTIwc3R5bGUlM0QlMjJvdmVyZmxvdyUzQWhpZGRlbiUzQmhlaWdodCUzQTFweCUyMiUz
Mitigation steps
To protect against black hat SEO link injections like this one, you’ll want to ensure that your core CMS, plugins, themes and other website software are always up-to-date with the latest security patches. Furthermore, you can use a web application firewall to filter malicious traffic and virtually patch known vulnerabilities.
It’s also highly recommended to place additional access control protections on your administrator panel such as two factor authentication.
And as always, if you have discovered that your site has spam links or malware and you need a hand, we’re always happy to help clean up an infection.
