SOC 3 Minutes
- [1] Cortex XSOAR Tips & Tricks
- [2] Cortex XSOAR Tips & Tricks – Execute Command Function
- [3] Cortex XSOAR Tips & Tricks – Tagging War Room Entries
- [9] Cortex XSOAR Tips & Tricks – Creating indicator relationships in integrations (current)
- [4] Cortex XSOAR Tips & Tricks – Using The API In Automations
- [5] Cortex XSOAR Tips & Tricks – Exploring the API using Swagger Editor
- [6] Cortex XSOAR Tips & Tricks – Execute Commands Using The API
Introduction
When a Threat Intelligence Management (TIM) license is present in your Cortex XSOAR environment, the feature to create relationships between indicators is available. This allows you to describe how indicators relate to each other and use this relationship in your automated analysis of a security incident.
In the previous blog post in this series, we gave a brief overview of the additional features available in Cortex XSOAR when a TIM license is imported. We also showed you how to create relationships between indicators from within automations by using the CommandResults class from CommonServerPython.
In this post, we will show you how to create relationships from within a Cortex XSOAR integration. This requires a different approach because there are different features available in an automation and an integration.
Threat Intelligence Integrations
The most common use case for creating indicators and their relationships from within an integration is related to threat intelligence. In general, these integrations import threat intelligence data as indicators into Cortex XSOAR. These indicators can either be used by the SOC analysts in their investigations of incidents or, after automated or manual curation, can be exported to other platforms for additional detection capabilities.
An example of such an integration would be the MITRE ATT&CK v2 integration created by Cortex XSOAR. This integration fetches the MITRE ATT&CK techniques from the MITRE TAXI feed and creates Attack Pattern indicators in Cortex XSOAR for each technique.
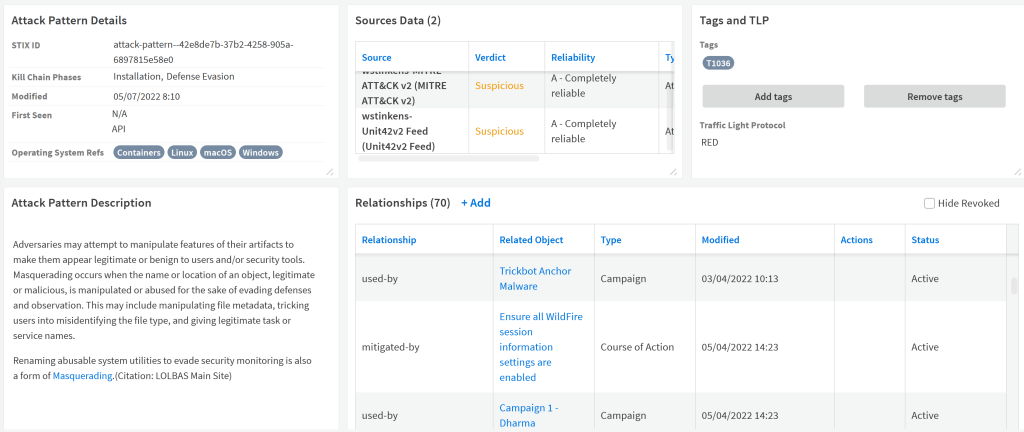
An Attack Pattern indicator layout is available after installing the MITRE ATT&CK v2 content pack which visualizes all the fetched data:

In the Relationships section of the Attack Pattern indicator layout, you can see all the related indicators:

Besides the Attack Pattern indicators, the MITRE ATT&CK integration also creates indicators for the APT groups that use the technique, which malware is related to the technique and information about the how it can be mitigated.
In our SOC, we actively use these Attack Pattern indicators by associating them to the incident based on the MITRE ATT&CK technique IDs available in the incident data fetched from the SIEM or EDR platform. This allows the SOC analyst to quickly see which techniques are used in the incident and retrieve all relevant information at a click of a button.
Create Indicator Relationships
When creating your own custom integration which fetches data to create indicator relationships, you will not be able to use the same approach as we describe in the previous blog post in this series by using the CommandResults class from CommonServerPython.
To create indicator relationships from within an integration, you will need to use the createIndicators method of the demisto class. As when using the CommandResults, you will need to define the indicator relationship in an instance of the EntityRelationship class. Because the instance will be used by the createIndicators method, to_indicator() should be called when creating it.
indicator_relationships = []
indicator_relationships.append(
EntityRelationship(
name=EntityRelationship.Relationships.USES,
entity_a="u4872",
entity_a_type="Account",
entity_b="pc135456.domain.local",
entity_b_type="Host"
).to_indicator()
)
The createIndicators method takes a list of indicators to create as an argument and cannot create relationships without an indicator. We will need to use a dummy indicator which will have the list of EntityRelationship instances as a value of the indicator relationships argument:
dummy_indicator = [
{
"value": "$$DummyIndicator$$",
"relationships": indicator_relationships
}
]
This dummy indicator should be passed as the indicators_batch argument of the createIndicators method:
demisto.createIndicators(indicators_batch=dummy_indicator)
When calling the createIndicators method the dummy indicator will be created together with all the indicator relationships defined in the indicator relationships argument. The dummy indicators will remain present in Cortex XSOAR but will not be associated to any incident.
References
https://xsoar.pan.dev/docs/reference/api/common-server-python#commandresults
https://xsoar.pan.dev/docs/reference/integrations/mitre-attck-v2
https://attack.mitre.org/resources/working-with-attack/
https://xsoar.pan.dev/docs/reference/api/demisto-class#createindicators
https://xsoar.pan.dev/docs/reference/api/common-server-python#entityrelationship
About the author
Wouter is an expert in the SOAR engineering team in the NVISO SOC. As the SOAR engineering team lead, he is responsible for the development and deployment of automated workflows in Palo Alto Cortex XSOAR which enable the NVISO SOC analysts to faster detect attackers in customers environments. With his experience in cloud and devops, he has enabled the SOAR engineering team to automate the development lifecycle and increase operational stability of the SOAR platform.
You can contact Wouter via his LinkedIn page.
Want to learn more about SOAR? Sign- up here and we will inform you about new content and invite you to our SOAR For Fun and Profit webcast.
https://forms.office.com/r/dpuep3PL5W
Published