WhatsApp has recently fixed critical and high-severity vulnerabilities affecting WhatsApp for Android, WhatsApp Business for Android, WhatsApp for iOS, and WhatsApp Business for iOS. Exploiting these vulnerabilities would be the first step of an attacker to install any malware on the device. In 2019, the Israeli spyware maker NSO Group exploited an audio calling flaw to inject the Pegasus spyware.
WhatsApp Remote Code Execution (RCE) Vulnerabilities
WhatsApp released a patch to fix the RCE critical vulnerability (CVE-2022-36934). This vulnerability has a CVSSv3 base score of 9.8 and should be prioritized for patching. An integer overflow in WhatsApp could result in remote code execution (RCE) in an established video call. It affects assets running:
- WhatsApp for Android prior to v2.22.16.12
- WhatsApp Business for Android prior to v2.22.16.12
- WhatsApp for iOS prior to v2.22.16.12
- WhatsApp Business for iOS prior to v2.22.16.12
WhatsApp released a patch to fix another REC high vulnerability (CVE-2022-27492). This vulnerability has a CVSSv3 base score of 7.8 and should be prioritized for patching. Integer underflow in WhatsApp could have caused remote code execution when receiving a crafted video file. It affects assets running WhatsApp for Android v2.22.16.2 and WhatsApp for iOS v2.22.15.9. To exploit this vulnerability, attackers would have to drop a crafted video file on the user’s WhatsApp messenger and convince the user to play it.
The latest vulnerabilities are also affecting the WhatsApp Business app. If you are using it within your organization, it becomes critical to fix it on priority. Successful exploitation of these vulnerabilities would lead to remote code execution and let attackers install malware on the impacted devices. To minimize the risk, first, you need to identify the affected assets and then update the application to the right version.
Identification of Assets using VMDR Mobile
Identifying the assets is the first step in managing critical vulnerabilities and reducing risk. Qualys VMDR Mobile makes it easy to identify the assets running WhatsApp. To get comprehensive visibility of the mobile devices, you need to install Qualys Cloud Agent for Android or iOS on all mobile devices. The device onboarding process is easy, and the inventory of mobile devices is free.
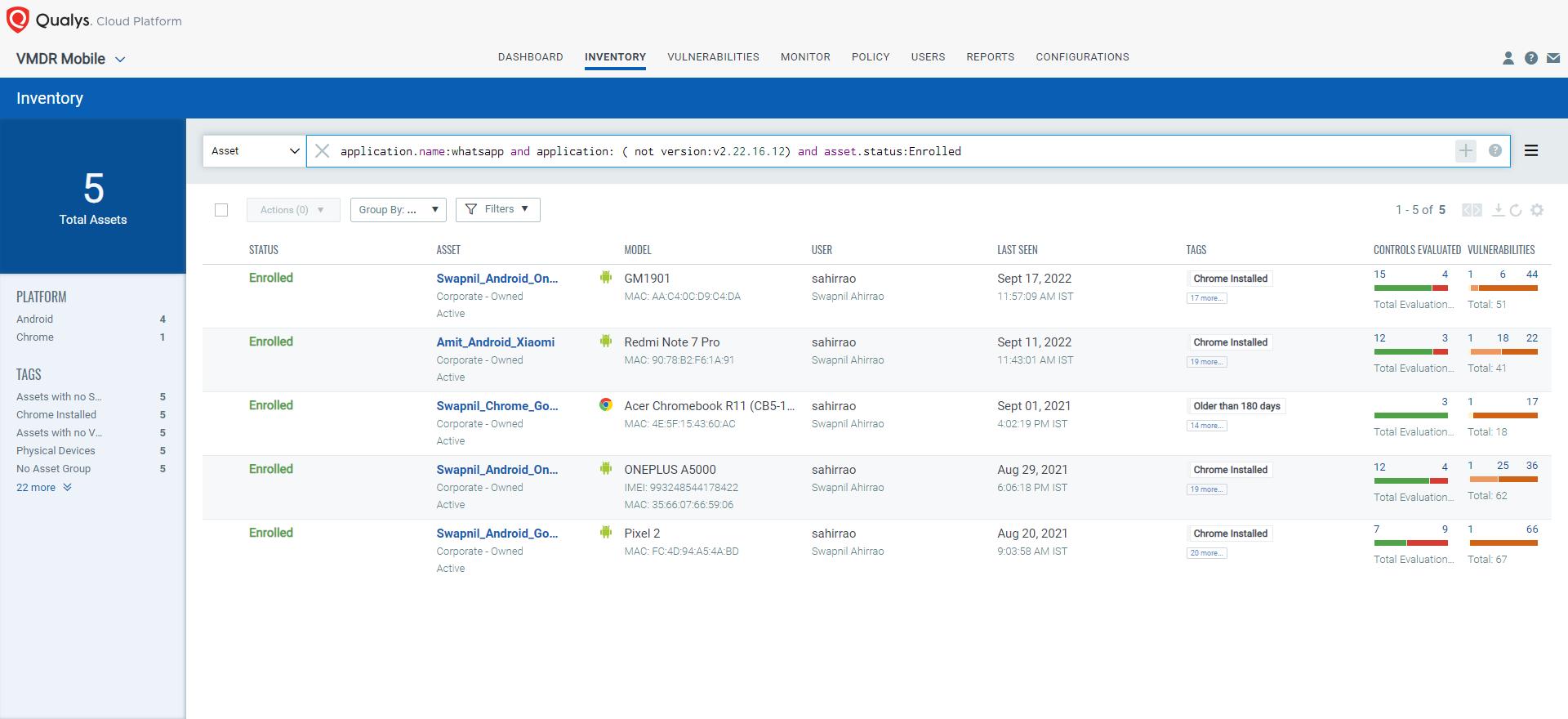
To get the list of assets that are not updated to v2.22.16.12, run the QQL in the Asset dropdown of the Inventory tab.
QQL: Asset- application.name:whatsapp and application: ( not version:v2.22.16.12) and asset.status:Enrolled

Discover WhatsApp Vulnerabilities (CVE-2022-36934) and (CVE-2022-27492)
You have the list of assets running WhatsApp with the impacted version; now, you want the list of assets with the latest WhatsApp vulnerabilities. VMDR Mobile automatically detects the new vulnerabilities based on the continuously updated Knowledgebase.
To see all detections, navigate to the Vulnerability tab, add and run the following QQL in the Vulnerability dropdown
QQL: vulnerabilities.vulnerability.qid:630827

QID 630827 is available in signature version SEM VULNSIGS-1.0.0.69, and there is no dependency on any specific Qualys Cloud Agent version.
With the VMDR Mobile dashboard, you can track the status of the assets on which the latest WhatsApp vulnerabilities are detected. The dashboard will be updated with the latest data collected by Qualys Cloud Agent for Android & iOS devices.

Response by Patching and Remediation
VMDR Mobile provides you the patch orchestration for Android devices that helps you rapidly remediate Android assets. Patch orchestration helps you initiate the most relevant per-application version patches on the affected assets.
You do not have to create multiple jobs; one job will take care of all Whatsapp vulnerabilities.

Users are encouraged to apply patches as soon as possible. For iOS assets, you can perform the “Send Message” action to inform the end-user to update WhatsApp to the latest version. Also, you may provide step-by-step details to update WhatsApp from the Apple App Store.
Get Started Now
Qualys VMDR Mobile is available free for 30 days to help customers detect vulnerabilities, monitor critical device settings, and correlate updates with the correct app versions available on Google Play Store. You can try our solution by registering for the free 30-day service.