At Sucuri, we’re often asked how website owners and webmasters can secure their websites. However, advice can often be too broad; different content management systems (CMS) exist in this ecosystem and each require a unique security configuration. That’s exactly why the Sucuri Firewall contains an application profiling engine that adapts to the CMS and regular website traffic patterns to identify signs of a threat.
With that in mind, today we’re covering some of the steps to secure a Joomla! website. According to W3Techs, as of October 4th, 2022, Joomla powers 2.5% of all websites with a known content management system.
That percentage may sound small, but it’s still a lot of sites. It’s important to realize that attackers don’t discriminate when it comes to a website’s size or the CMS they’re using. Malicious users are prone to launch large-scale attempts in order to exploit a vulnerability. With the methods they use, that means any website can be targeted.
Is Joomla secure?
Every major CMS platform encounters new security threats on a daily basis, as zero-day vulnerabilities are constantly being disclosed and exploited. And while Joomla tries their best to offer regular updates to patch new issues, additional security concerns are always present.
According to CVE details, a total of 440 vulnerabilities have been disclosed against Joomla — and that’s just for core, this number doesn’t include known vulnerabilities for any extensible components. This data highlights why it’s important to harden your Joomla website against attackers (and stay on top of updates).
So, let’s dive in and touch on twelve of the most important hardening techniques you can employ on your Joomla website.
How to secure your Joomla site
Here are 12 best practices to improve Joomla! security:
- Update Joomla Core & Extensions
- Remove Unused Templates or Extensions
- Hide the Joomla Admin Panel
- Secure Access Points
- Enable Multi-Factor Authentication
- Practice Principle of Least Privilege
- Use It or Lose It
- Monitor Your Site
- Maintain Backups
- Use HTTPS / SSL
- Use a Joomla Web Application Firewall
- Restrict Public Access
1 – Update Joomla Core & Extensions
A tale as old as the internet: update everything! Using outdated software significantly exposes a website to risk. It is not always easy to upgrade to the latest version of Joomla, but it’s a risk you need to be aware of.
In most releases, Joomla fixes some security issues to make sure you keep your software updated with the latest patches. If you don’t upgrade your website, you’re likely keeping a vulnerability around to be exploited by bad actors.
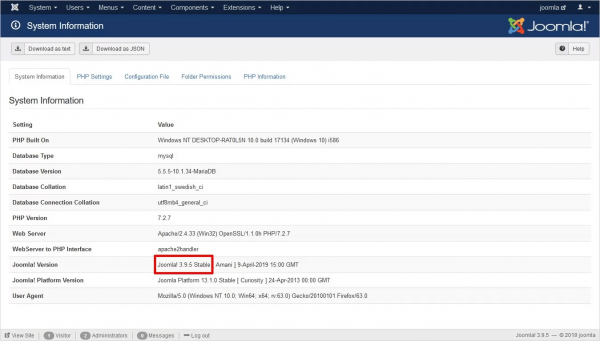
Here’s some guidance on where to find out which Joomla version your site is running:
Core: Login to Dashboard > System > System Information
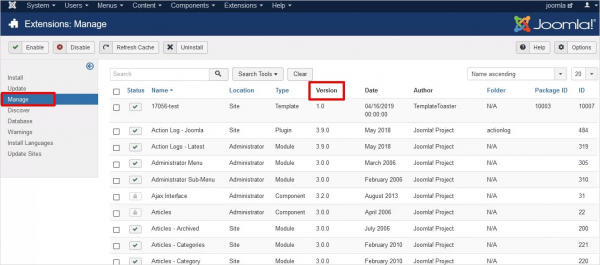
Extensions: Login to Dashboard > Extensions > Manage > Manage
Joomla can notify you when a vulnerability is discovered in the core file system or within an extension.
You can find more information from the official Joomla Core Security Notifications page, where you can sign up for the Joomla Security news RSS feed to stay in the loop about important updates.
2 – Remove Unused Templates & Extensions
Joomla is an open source technology, meaning the code is public and anyone can contribute. Many of the extensions or templates are produced in the same way. This leads to some unfortunate issues. Not every extension is built with the same attention to security.
New features and better tools are always fun to work with. However, installing an extension can introduce threats in your website environment. Make sure the extensions you’re using are trustworthy and recently updated. You want to know the developer is actively maintaining the extension.
Similarly, keep checking for updates to ensure you have the latest version on your Joomla website.
If you stop using an extension or template, remove it. It doesn’t make sense to keep a plugin that may have a vulnerability and cause damage to your website. Less code = less potential problems.
And if you can’t keep your Joomla installation updated for any reason, use a website firewall to virtually patch vulnerabilities and shield the website from exploits.
3 – Hide the Joomla Admin Panel
The Joomla administrator URL should be changed to prevent attackers from getting in. By default, Joomla users log in to:
http://www.yoursite.com/administrator
Attackers can gain unauthorized access by launching brute force attacks against the /administrator URL. These attacks can guess thousands of passwords in minutes.
There are free Joomla security extensions that you can use to append the default administrator URL with a unique string for strengthening.
Caution: We recommend testing in a development environment, as renaming the administrator URL can break some functionality in some sites if not implemented correctly.
4 – Secure Access Points
We encourage users to keep all access points secured and change default settings.
In the same way that an attacker would presume to try the “administrator” URL, they’ll likely test a common brute force tactic: Use admin as the username.
The best practice is to change the default username from admin to something unique. This can be accomplished from the User Manager area within Joomla.
You should also use strong passwords. Password managers are excellent tools to maintain and generate long, complex password combinations. Just remember not to use the same password multiple times. Unique, long, and complex is key!
5 – Enable Multi-Factor Authentication
Multi-factor authentication is an extra layer of security beyond your password. To log in to accounts, this feature requires something extra to verify the user identity – usually a 6-digit code sent to an email, text, or time-based authentication app.
2FA (two factor authentication) is the most common multi-factor authentication method and Joomla supports the use of Google Authenticator just for this purpose.
To take advantage of the 2FA feature, you’ll need to use Joomla 3.2.0 or higher.
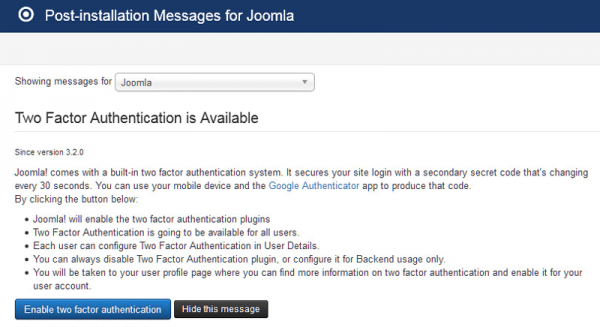
Here’s how you enable 2FA in Joomla:
- Login to your Administrator Panel
- Go to Components, then Post-Installation Messages
- Click on Enable two-factor authentication.
- You will be taken to your user profile page
- Install a Google Authenticator client for your device
- Scan the QR Code with your phone via Google Authenticator
- Go back to Activate Two-Factor Authenticator field and enter the six digit code seen on your phone.
- Click on Save & Close.
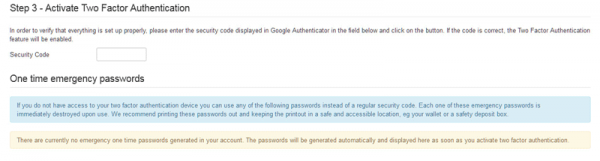
If you no longer have the Post-Installation Messages, you can navigate directly to your user profile page then to the Two-factor Authentication tab to continue the process.
If the Two-Factor Authentication tab doesn’t display, it’s possible that the associated plugin hasn’t been enabled. Go to the Plugin Manager and find the two-factor plugin for Google Authenticator. Enable it, then return to your user profile page and try again
6 – Practice the Principle of Least Privilege
Remember that Joomla offers three distinct permissions groups:
- Managers
- Have the least access to the back end of Joomla. Managers can create and edit categories and articles.
- They have access to the media manager and can upload and remove media. Managers cannot install or remove extensions.
- Administrators
- Have all the rights Managers have, along with a few additional permissions.
- They also have access to User Management, Menu Manager and Extension Manager. However, Administrators don’t have access to Global Configuration.
- Super Users
- Have complete access. They have all the rights of Managers and Administrators, along with access to the Global Configuration.
- Only Super Users can add, edit, and remove Super Users.
It’s important that you distribute these roles carefully to your group of users. Anyone with a Super User is able to perform every action within your Joomla system.
If you delegate tasks to a team member that requires fewer permissions, grant the minimum access required.
Note: The principle of least privilege also applies to your file and directory structure. Never set a file path with CHMOD 777 permissions.
7 – Use It or Lose It: Redux (Users)
Old, unused accounts are another attack vector to be aware of.
It’s common for websites to generate a growing number of Super Users & Administrators. This happens with old developers who have access to a website even after leaving the project.
You may have forgotten that you set up a temporary account so a developer could debug a problem you are having with one of their extensions. These scenarios can lead to a hacker successfully brute forcing their way into the account to distribute malware.
So, what’s the best way to avoid this?
Go to your User Manager, and filter by administrators and super administrators.
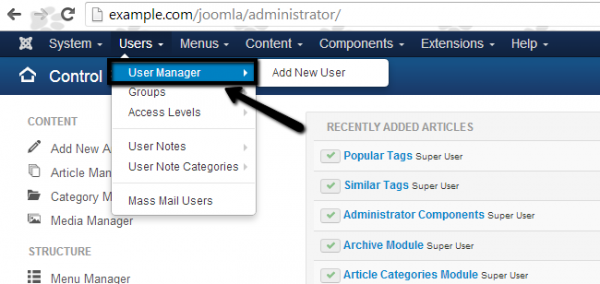
Then delete (or modify) accounts that no longer require high-level access.
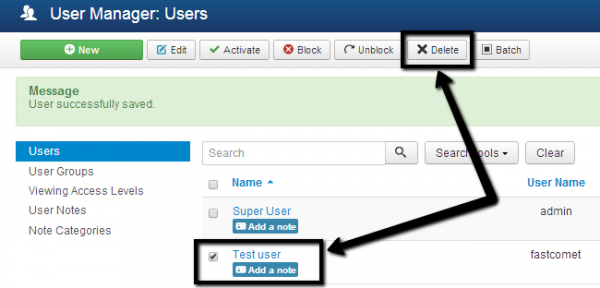
Remember: someone you once trusted with Super User access could come back with nefarious intentions.
This is a real case we received:
- The relationship between a website owner and a developer ended—and not in the best terms.
- The website owner did not revoke the developers user access.
- The developer logged back into the website and locked out all of the other accounts.
- The developer then asked the website owner for a ransom in exchange for access to be returned.
Its extremely important that once a certain access is no longer needed, it is immediately revoked. This applies to every type of access that is granted.
8 – Monitor Your Site
Visibility is key. It’s important to install tools or procure a vendor to help you achieve visibility into your website environment. Monitoring offers an early warning system for indicators of compromise. The solution you choose should perform the following functions.
Integrity checks: File integrity monitoring tools should normally be installed on a server where they can create a baseline of your files. If a file or record is modified in any way, you’ll receive a notification of the changes.
Website auditing: Auditing tools give you visibility into user activity on the website. As the administrator of your website you should be asking questions like these:
- Who is logging in to my Joomla website? Should they be logging in?
- Why are they changing that post?
- Why are they logging in when they should be sleeping?
- Who installed that plugin?
- Why are they taking that action?
We cannot stress enough the importance of logging activity. Use a tool that logs and alerts you of any actions taken on your website. This can help you identify the initial break in, even before the bad actors inject their malicious payload.
9 – Maintain Joomla! Backups
Maintaining website backups is one of the most important recurring tasks for a website administrator.
A good set of backups can save your website when absolutely everything else has gone wrong. If a malicious attacker decides they want to wipe all your site files or corrupts your site files with their buggy scripts, the damage can be undone simply by restoring your site from your backups.
One of the most popular backup tools for Joomla is Akeeba.
You can watch this webinar on how to prevent data loss with website backups.
10 – Use HTTPS / SSL
With an SSL certificate, your website will use the HTTPS protocol to securely transfer information between point A (browser) and B (web server).
This is crucial when communicating sensitive information like credit card data on checkout pages and Personally Identifiable Information (PII) on login and contact forms.
In addition to security benefits, Joomla websites using SSL get better rankings on Google and improved performance through the use of HTTP/2. It’s also important to understand that SSL does nothing to protect your website from being hacked. It simply encrypts and protects data in transit, and is especially important for ecommerce websites.
11 – Use a Joomla Web Application Firewall
A Joomla! Web Application Firewall (WAF) is essential for any Joomla! website to protect from DDoS attacks and OWASP Top 10 vulnerabilities.
By detecting and stopping known hacking methods and behaviors, a WAF keeps your site protected against infections in the first place. It will also quickly block against an attempt to exploit vulnerabilities in extensions and templates; even emerging exploits (called zero-days).
Most WAFs will offer caching for faster global page speed. This keeps your visitors happy and is proven to lower bounce rates while improving website engagement, conversions, and search engine rankings. We offer all of these features for Joomla sites with our Sucuri Firewall.
12 – Restrict Public Access
Additionally, you can also restrict access to the /administrator directory (or any other file path) to only select IP addresses. To find your IP, try What Is My IP. If there isn’t a file named “.htaccess” in the /administrator directory, create one. Then just add the following lines at the end of the .htaccess file:
Deny from ALL. Allow from [insert whitelisted IPs here]
If you’re using a cloud-based WAF like ours, you’ll also want to add the IPs from the firewall vendor to ensure traffic is filtered and the WAF can communicate with your server.
Stay Vigilant!
If you’re looking for more comprehensive material, check out our Joomla security guide.
As the security landscape changes, what’s required of us to stay ahead of emerging threats also shifts. The Sucuri blog is a great resource for tackling new tactics and trends. Or you can sign up to join our mailing list to stay in the loop.
