Vulnerability reports and responsible disclosures are essential for website security awareness and education. Automated attacks targeting known software vulnerabilities are one of the leading causes of website compromises.
To help educate website owners on emerging threats to their environments, we’ve compiled a list of important security updates and vulnerability patches for the WordPress ecosystem this past month.
You can mitigate risk by ensuring all of your website software and extensible components are patched with the latest updates and security releases.
WordPress Core – Security Release
Affected Software: WordPress <= 6.0.2 Patched Versions: WordPress 6.0.3
A new security update has been released for WordPress. In this latest update, the WordPress security team fixed a number of security issues and vulnerabilities including a stored cross-site scripting (XSS) via wp-mail.php (post by email).
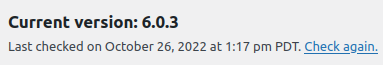
To mitigate risk, update WordPress core to the latest version as soon as possible. If your site has already been configured for automatic updates, you can check and verify that your WordPress website has been patched.
To Update WordPress:
- Navigate to your WordPress Dashboard.
- Click Updates.
- Click Update Now.
Alternatively, you can download WordPress 6.0.3 from WordPress.org.
WP Super Cache — Cache Poisoning
Security Risk: Medium Exploitation Level: Can be remotely exploited without authentication. Vulnerability: Security Misconfiguration CVE: N/A Number of Installations: 2 million+ Affected Software: WP Super Cache <= 1.8 Patched Versions: WP Super Cache 1.9
Unauthenticated attackers are able to send requests that cause unintended responses which are stored in the cache, allowing attackers to serve pages in unexpected or malicious ways.
Mitigation steps: Update to WP Super Cache plugin version 1.9 or greater.
Smart Slider 3 — PHP Object Injection
Security Risk: High Exploitation Level: Requires admin or other users with attributed permissions. Vulnerability: Injection CVE: CVE-2022-3357 Number of Installations: 900,000+ Affected Software: Smart Slider 3 <= 3.5.1.9 Patched Versions: Smart Slider 3 version 3.5.1.11
Imported file contents are unserialized by the plugin. This can potentially lead to PHP object injections if a user imports a malicious file and a suitable gadget chain is present.
Mitigation steps: Update to Smart Slider 3 plugin version 3.5.1.11 or greater.
Ocean Extra — PHP Object Injection
Security Risk: Medium Exploitation Level: Requires admin or other high level authentication. Vulnerability: Injection CVE: CVE-2022-3374 Number of Installations: 700,000+ Affected Software: Ocean Extra <= 2.0.4 Patched Versions: Ocean Extra 2.0.5
Imported file contents are unserialized by the plugin. This can potentially lead to PHP object injections if a user imports a malicious Customizer Styling file and a suitable gadget chain is present.
Mitigation steps: Update to Ocean Extra plugin version 2.0.5 or greater.
Easy WP SMTP — Authenticated PHP Object Injection
Security Risk: Medium Exploitation Level: Requires admin or other high level authentication. Vulnerability: Injection CVE: CVE-2022-3334 Number of Installations: 600,000+ Affected Software: Easy WP SMTP <= 1.4.9 Patched Versions: Easy WP SMTP 1.5.0
Imported file contents are unserialized by the plugin. This can potentially lead to PHP object injections if a user imports a malicious file and a suitable gadget chain is present.
Mitigation steps: Update to Easy WP SMTP plugin version 1.5.0 or greater.
Complianz GDPR/CCPA Cookie Consent — Authenticated SQL Injection (SQLi)
Security Risk: High Exploitation Level: Requires infected translation file or user with translator role. Vulnerability: SQL Injection CVE: CVE-2022-3494 Number of Installations: 400,000+ Affected Software: Complianz GDPR/CCPA Cookie Consent <= 6.3.3 Patched Versions: Complianz GDPR/CCPA Cookie Consent 6.3.4
The plugin does not sanitize translations, allowing translators or infected translation files to inject arbitrary SQL.
Mitigation steps: Update to Complianz GDPR/CCPA Cookie Consent plugin version 6.3.4 or greater.
FluentForm Contact Form — CSV Injection
Security Risk: Medium Exploitation Level: Requires admin or other high level authentication to export the injected CSV. Vulnerability: Injection CVE: CVE-2022-3463 Number of Installations: 200,000+ Affected Software: FluentForm Contact Form <= 4.3.12 Patched Versions: FluentForm Contact Form 4.3.13
Fields are not properly escaped and validated by the plugin when exporting form entries as CSV. This can lead to a CSV injection.
Mitigation steps: Update to FluentForm Contact Form plugin version 4.3.13 or greater.
Customizer Export/Import — Authenticated PHP Object Injection
Security Risk: Medium Exploitation Level: Requires admin or other high level authentication. Vulnerability: Insecure Deserialization CVE: CVE-2022-3380 Number of Installations: 200,000+ Affected Software: Customizer Export/Import Patched Versions: Customizer Export/Import 0.9.5
Imported file contents are unserialized by the plugin. This can potentially lead to PHP object injections if a user imports a malicious file and a suitable gadget chain is present.
Mitigation steps: Update to Customizer Export/Import plugin version 0.9.5 or greater.
reSmush.it Image Optimizer — Authenticated Cross-Site Scripting (XSS)
Security Risk: Medium Exploitation Level: Requires admin or other high level authentication. Vulnerability: Cross-Site Scripting (XSS) CVE: CVE-2022-2448 Number of Installations: 200,000+ Affected Software: reSmush.it Image Optimizer <= 0.4.5 Patched Versions: reSmush.it Image Optimizer 0.4.6
Some plugin settings are not problem sanitized and escaped. As a result, admins and other high privilege users are able to perform stored cross-site scripting attacks.
Mitigation steps: Update to reSmush.it Image Optimizer plugin version 0.4.6 or greater.
Kadence WooCommerce Email Designer — Authenticated PHP Object Injection
Security Risk: Medium Exploitation Level: Requires admin or other high level authentication. Vulnerability: Injection CVE: CVE-2022-3335 Number of Installations: 100,000+ Affected Software: Kadence WooCommerce Email Designer <= 1.5.6 Patched Versions: Kadence WooCommerce Email Designer 1.5.7
Imported file contents are unserialized by the plugin. When an admin imports a malicious file and a suitable gadget chain is present, this can lead to PHP object injections.
Mitigation steps: Update to Kadence WooCommerce Email Designer plugin version 1.5.7 or greater.
AntiSpam by CleanTalk — Authenticated SQL Injection (SQLi)
Security Risk: Medium Exploitation Level: Requires admin or other high level authentication. Vulnerability: Injection CVE: CVE-2022-3302 Number of Installations: 100,000+ Affected Software: AntiSpam by CleanTalk <= 5.185 Patched Versions: AntiSpam by CleanTalk v5.185.1
Ids are not properly validated by the plugin prior to use in SQL statements. As a result, Admins and other high privilege users are able to perform SQL injections.
Mitigation steps: Update to AntiSpam by CleanTalk plugin version 5.185.1 or greater.
LearnPress — Unauthenticated PHP Object Injection
Security Risk: Medium Exploitation Level: Can be exploited remotely without authentication. Vulnerability: Insecure Deserialization CVE: CVE-2022-3360 Number of Installations: 100,000+ Affected Software: LearnPress <= 4.1.7.1 Patched Versions: LearnPress 4.1.7.2
User input is unserialized by the plugin, which can potentially lead to a PHP Object Injection when a suitable gadget chain is present and remote code execution (RCE). Attackers must have knowledge of site secrets to successfully exploit this vulnerability.
Mitigation steps: Update to LearnPress plugin version 4.1.7.2 or greater.
Envira Gallery Lite — Reflected Cross-Site Scripting (XSS)
Security Risk: Medium Exploitation Level: Requires Editor level or other high level permissions. Vulnerability: Cross-Site Scripting (XSS) CVE: CVE-2022-2190 Number of Installations: 100,000+ Affected Software: Envira Gallery Lite <= 1.8.4.6 Patched Versions: Envira Gallery Lite 1.8.4.7
The $_SERVER[‘REQUEST_URI’] parameter is not properly escaped by the plugin before outputting back into attributes. As a result, this can lead to reflected cross-site scripting attacks in older web browsers.
Mitigation steps: Update to Envira Gallery Lite plugin version 1.8.4.7 or greater.
PublishPress Capabilities — Authenticated PHP Object Injection
Security Risk: Medium Exploitation Level: Requires admin or other high level authentication. Vulnerability: Injection CVE: CVE-2022-3366 Number of Installations: 100,000+ Affected Software: PublishPress Capabilities Patched Versions: PublishPress Capabilities 2.5.2
Contents of imported files are unserialized by the plugin. This can lead to PHP object injection attacks by administrators where suitable gadget chains and multisite WordPress configurations are present.
Mitigation steps: Update to PublishPress Capabilities plugin version 2.5.2 or greater.
Manage Notification E-mails — Cross-Site Request Forgery (CSRF)
Security Risk: Medium Exploitation Level: Requires admin or other high level authentication. Vulnerability: Broken Access Control CVE: CVE-2022-34654 Number of Installations: 80,000+ Affected Software: Manage Notification E-mails <= 1.8.2 Patched Versions: Manage Notification E-mails 1.8.3
CSRF checks are not in place when the plugin resets settings. This can allow an attacker to make logged in high-privileged users perform CSRF attacks.
Mitigation Steps: Update to Manage Notification E-mails plugin version 1.8.3 or greater.
Form Maker — Authenticated SQL Injection (SQLi)
Security Risk: High Exploitation Level: Requires admin or other high level authentication. Vulnerability: Injection CVE: CVE-2022-3300 Number of Installations: 70,000+ Affected Software: Form Maker <= 1.15.5 Patched Versions: Form Maker 1.15.6
A parameter is not properly sanitized or escaped by the plugin prior to use in SQL statements. As a result, admins or other high privilege users can potentially exploit to perform SQL injections.
Mitigation steps: Update to Form Maker plugin version 1.15.6 or greater.
ImageMagick Engine — Remote Code Execution (RCE) via Cross-Site Request Forgery (CSRF)
Security Risk: High Exploitation Level: Requires admin or other high level authentication. Vulnerability: Broken Access Control CVE: N/A Number of Installations: 60,000+ Affected Software: ImageMagick Engine <=1.7.4 Patched Versions: ImageMagick Engine 1.7.6
Multiple actions are missing CSRF checks in the plugin. As a result, attackers are able to make authenticated admins perform malicious actions, potentially leading to remote code execution (RCE) via command injection.
Mitigation steps: Update to ImageMagick Engine plugin version 1.7.6 or greater.