前言
业余时间写的,纯兴趣更新! 做个记录。
测试环境
雷电模拟器 Android 7.1.2/pixexl2 Android 8.1
抓包测试
首先在apk中进行登录账户的时候进行抓包,获取登录凭证。
请求报文如下
1 2 3 4 5 6 7 |
|
在get请求中发现有传递以下参数
1 2 3 4 5 6 7 |
|
以及cookie中的pkey
1 |
|
以上参数我们需要知道hkey是怎么来的
因为是请求报文,所以算法肯定在apk内部实现的。要么在应用层要么在so层
定位算法(v1.1.50)
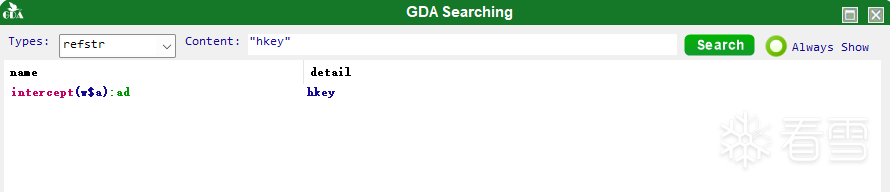
将apk拖入到GDA中进字符串搜索"hkey"

发现在intercept方法中有存在这个字符串。双击进入
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 |
|
str是当前时间/1000
分析下str1是怎么赋值的
1 |
|
首先调用类d的h方法,参数为特定字符串"xiaoheihe/_time="和当前时间str进行拼接的结果
然后再次调用类d的h方法,参数为 将第一次调用的的返回值中的“a”和"0"给替换为"app"的结果
最后就是对str1进行赋值了,将第二次调用d的h方法的返回值.
后面其实就是一个拼接请求头的操作,不需要关注。
所以这里我们看下类d的h方法的怎么实现的
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 |
|
发现就是个md5.
我们可以得知请求报文中的_time和hkey字段是关联的。
1 2 3 4 5 6 7 |
|
模拟算法(v1.1.50)
用脚本去验证下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 |
|
定位算法(v.1.3.92)
下载了小黑盒 v.1.3.92版本。
同样在登录的时候进行抓包。
1 2 3 4 5 6 7 |
|
这里imei变化了是因为换了台手机。
我们先不逆向
用上面的gethkey.py跑一下看看hkey和请求报文中的是否一致。如果不一致就说明,加密算法变化了。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 |
|
发现不一致,所以这个版本的getkey的算法发生了变化。
额,脑子坏掉了,请求报文中的hkey的长度只有10位的长度,肯定加密算法变了。
同样的操作定位到hkey的位置

发现新版本有三处地址含有该字符串。
先看第一个
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
|
类Q下的b方法,就是md5加密
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 |
|
第二个是就是这个版本使用的接口
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 |
|
关键代码
1 |
|
看下str2是怎么获得的
1 2 3 4 5 6 7 8 9 |
|
发现调用了类NDKTools下的encode方法
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
|
encode方法在native-lib的so中进行实现的。
hook&疑问
本地环境
手机端运行frida的服务端
1 |
|
电脑端查看进程
run.py
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 |
|
hook.js
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 |
|
发现可以成功运行起来

0xc9e90b01是encode函数的地址,当打开app后,这个地址是不变的。
这里我运行这个脚本只输出这些内容,但并没有打印出来参数和返回地址。
先静态分析吧。解包获得libnative-lib.so并拖入ida中
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 |
|
分析得知encode函数是将(str2+"/bfhdkud_time="+str1)进行md5加密,将加密的结果吗作为返回值
回到接口类中
1 2 |
|
发现只取md5返回值然后将其中的"a"和"0"都替换成str3即"app"
然后又调用了Q类下的b(String)方法,发现同样是md5算法
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 |
|
然后再将其返回值取前10位赋值给str2,即后面的hkey
模拟算法(v.1.3.92)
写成python实现
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 |
|
对比下请求报文,发现key值是一样的。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
|
参考
如有侵权请联系:admin#unsafe.sh