On Tuesday, Nov. 1, the OpenSSL project will release a new version of OpenSSL (version 3.0.7) that will patch an as-yet-undisclosed vulnerability in current versions of OpenSSL.
OpenSSL rates the severity of the vulnerability as CRITICAL, which means this vulnerability affects common configurations and is also likely to be exploitable. Examples include significant disclosure of the contents of server memory (potentially revealing user details), vulnerabilities which can be easily exploited remotely to compromise server private keys or where remote code execution is considered likely in common situations.
What is OpenSSL?
OpenSSL is the core open-source library which implements SSL and TLS protocols which makes it possible to securely communicate over the internet.
What do we know so far?
Vulnerability Impact
The details of the vulnerability are not known, but given the critical nature of the vulnerability it would likely result in disclosure of server memory, potentially reveal user details, and potentially exploit remotely to compromise server private keys or execute remote code.
Vulnerable Versions
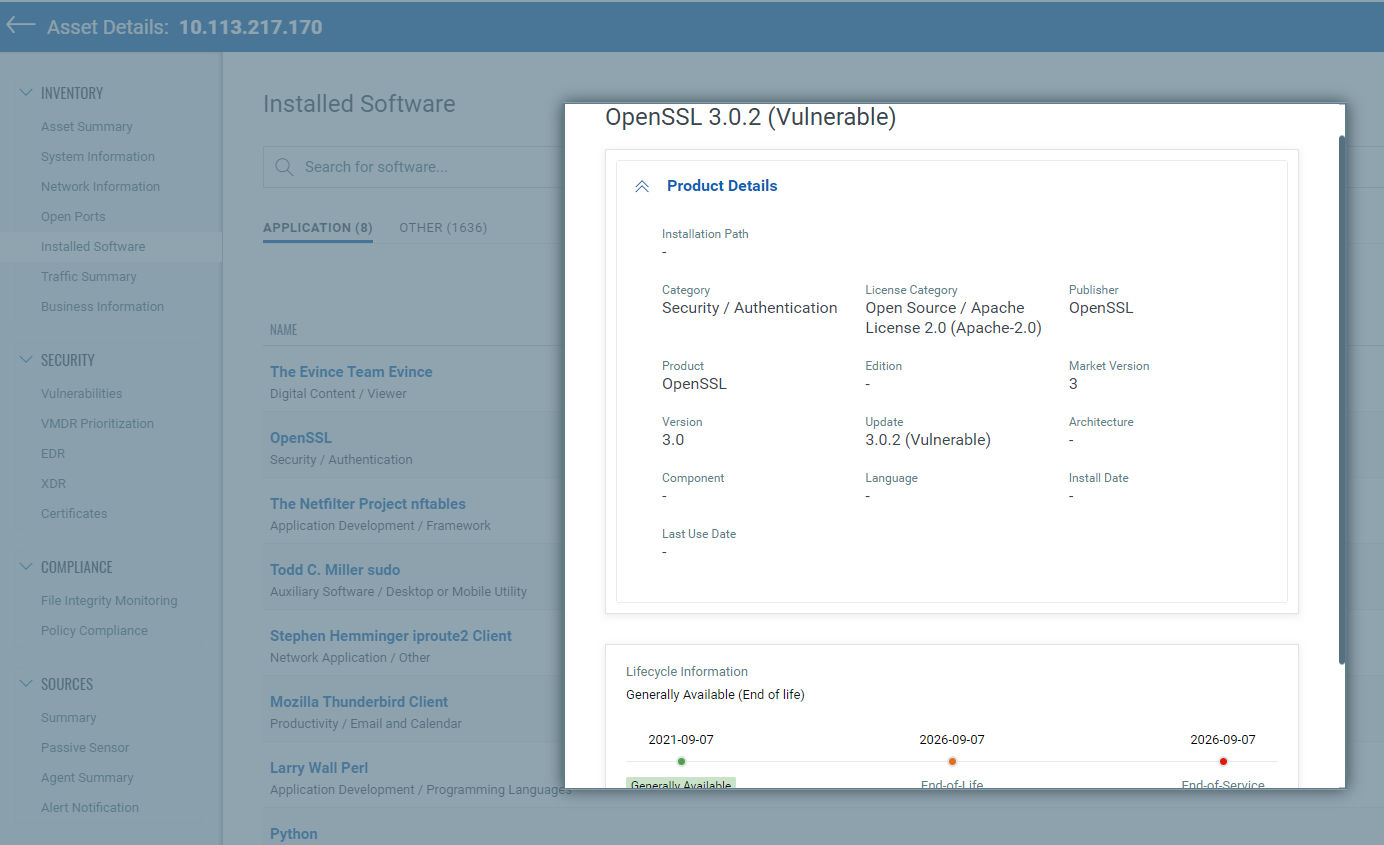
Only OpenSSL versions 3.0 through 3.0.6 are vulnerable. The commonly deployed OPENSSL 1.1.1 is not vulnerable.
What should organizations do?
Organizations should prioritize inventorying all systems with vulnerable versions of OpenSSL.
How can Qualys Help?
Inventory OpenSSL Using Qualys CSAM
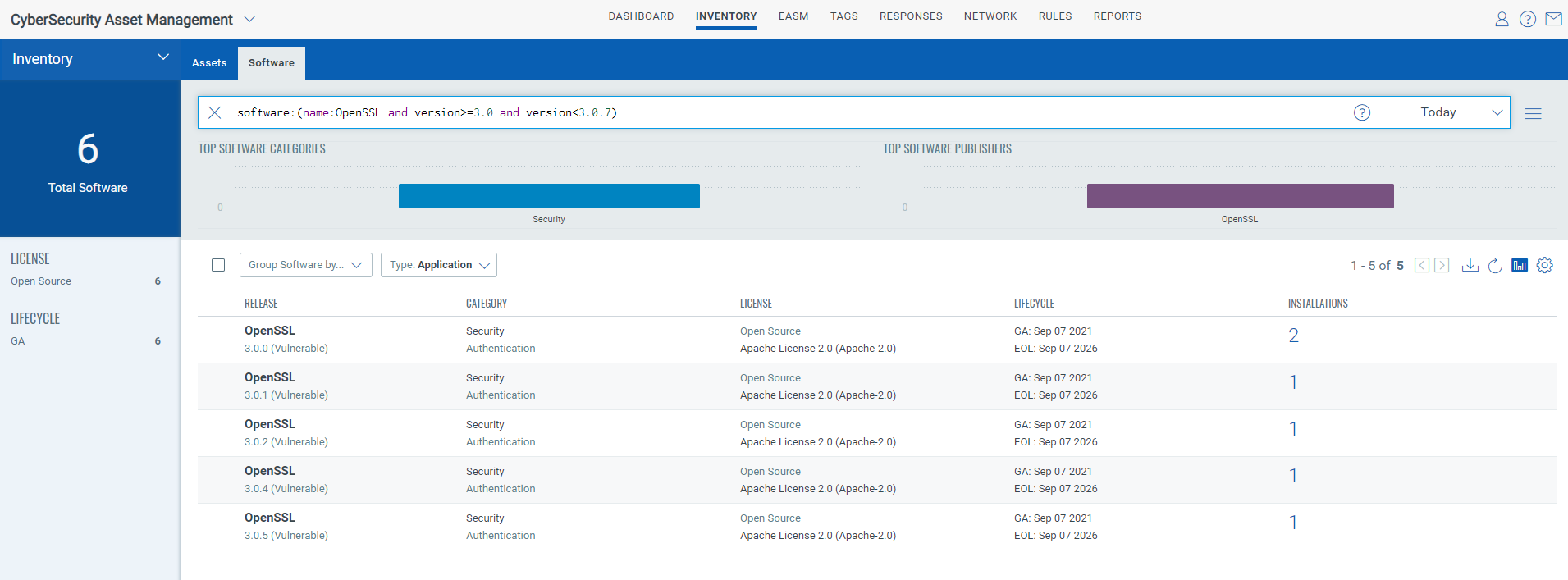
Qualys CSAM makes it easy to identify assets containing OpenSSL. The following QQL query will identify assets with openssl installed.
Query: software:(name:OpenSSL and version>=3.0 and version< 3.0.7)
The above QQL will help identify assets that have vulnerable version of OpenSSL installed.
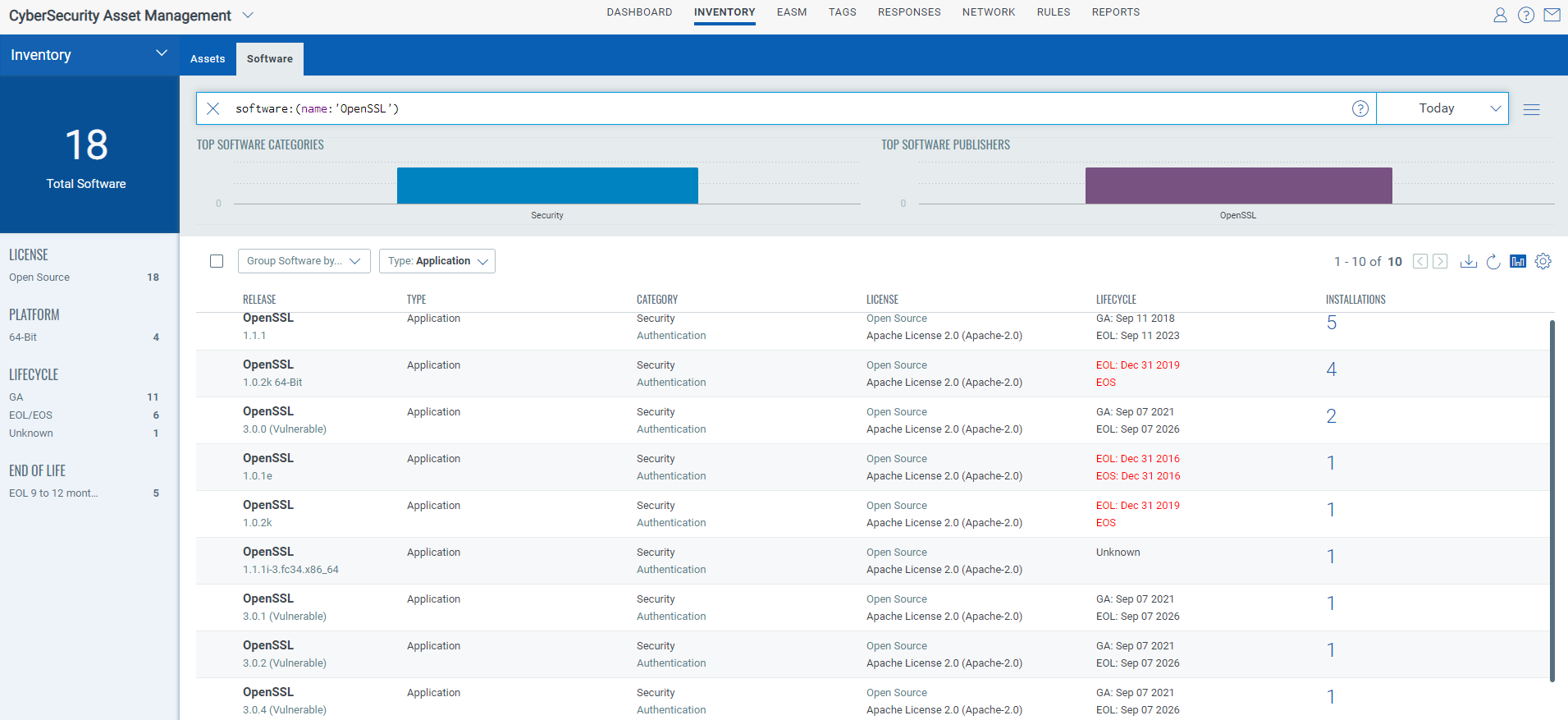
Tag Potentially vulnerable assets with CSAM
In addition to identifying the assets Qualys also recommends customers tag the assets with OpenSSL installed.

Discover Vulnerable Instances Using Qualys VMDR
Qualys QID Coverage
Qualys has released QID 38879 to help customer detect vulnerable versions of OpenSSL 3.0.x. The QID is available starting VULNSIGS-2.5.617-4 and lx-2.5.617.4-3. Qualys will release additional QIDs as and when the respective vendors make the advisories and patches available.
Search for following QIDs in your subscription to find vulnerable instances.
| QID | Title | Supported On | Release Versions |
|---|---|---|---|
| 38879 | OpenSSL 3.0 < 3.0.7 Critical Vulnerability | Agent + Scanner | VULNSIGS-2.5.617-4 and lx-2.5.617.4-3 |
Please note, once the vulnerability is disclosed on Nov 1st each vendor will probably release back ported patches for the vulnerability. Qualys research team is closely tracking the vulnerability and will release QIDs to detect those backported versions.
Please stay tuned for more updates. Qualys Research team will be regularly updating the blog as more details become available.