样本运行平台为linux系统,作为僵尸网络节点进行DDoS攻击。
连接IRC服务器,通过互联网中继聊天接收指令,能够完成聊天服务器相关的聊天室配置、身份配置、状态反馈等聊天功能,通过解析消息获取攻击类型与攻击目标,完成DDoS攻击。
样本属于Tsunami家族,DDoS攻击程序,活跃时间为2013年至今。该家族使用的攻击手段包括TCP、UDP、DNS泛洪攻击。
目前发现样本相关的源码已经公开在网络,适合分析者研究学习https://github.com/Soldie/COLE-O-botnets/blob/aec534acbf9789451f009129efaa1ec760973e2e/VirusPack/f34c5c27b.c
3.1 ELF文件头
文件头信息
3.2 僵尸网络
样本作为“僵尸网络”中的“肉鸡”,执行逻辑如下。
A、根据Time、PPID生成客户端标识ID。
B、连接IRC服务器加入聊天频道
C、接收聊天消息,检查消息,执行指令。
服务器地址、端口
通过解析通讯流量,其通讯数据各字段含义见下图:
通讯流量
聊天协议包含的指令,以及对应的聊天室功能见下表:
指令 | 功能 |
352 | 设置一个假ip |
376 | 加入特定频道,查找匹配的mac地址 |
433 | 用“/usr/dict/words”目录下的文件内容做别名 |
422 | 同367,加入特定频道 |
PRIVMSG | 接收irc命令,访问/usr/bin/xxh的目录下有没有SSH相关进程,如果有的话就关掉;从这里面进入ddos僵尸网络攻击 |
PING | 发送PONG指令,用户的登陆与结束 |
JOIN | 加入频道 |
KICK | 加入服务器对应的频道 |
NICK | 取别名 |
聊天协议
3.3 DDoS攻击
样本提供了四种攻击方式,攻击对应与指令见下表。
指令 | 功能 |
Tsunami | ACK FLOOD攻击 |
Pan | SYN FLOOD攻击 |
Dos | UDP FLOOD攻击 |
Unknown | 垃圾数据包 |
除发送垃圾数据包外,其余攻击方式均伪造假的数据封包,欺骗目标系统调用资源处理数据包。详细分析见下文逆向细节。
指令 | 描述 |
SPOOFS | 设定IP范围 |
DISABLE | 判断密码是否输入正确 |
ENABLE | 恢复客户端的能力 |
GET | url拼接,获取cpu架构,该程序只在i686和x86系统上运行,设置可接收的文件格式,接收上线地址发来的数据,从80端口联网接受浏览器的请求下载指定木马文件 |
VERSION | 返回后门版本 |
BYEBYEALL | 关闭对客户端的ddos攻击 |
IRC | 将指定的irc指令发送到服务器 |
CHGSERV | 更改服务器 |
Help | 显示可用指令列表 |
NICK | 取别名 |
GETSPOOFS | 获取欺骗参数 |
ENABLE | 判断密码是否输入正确 |
DDoS攻击的相关设定指令
3.4. 溯源分析
3.4.1 CC检索
公开情报显示:该样本连接的IRC服务器地址关联到恶意软件、远控、挖矿木马、Tsunami泛洪等标签。
CC情报
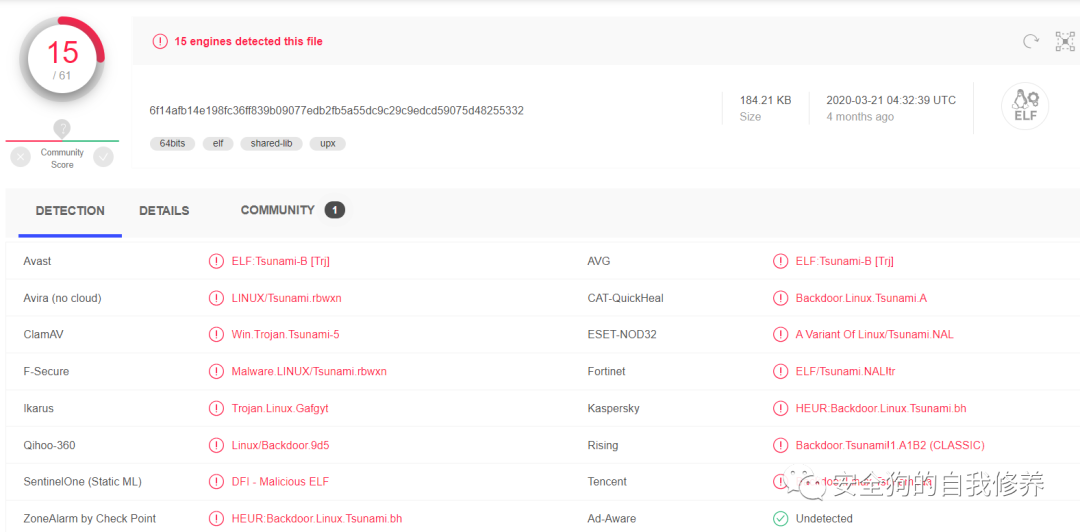
3.4.2 哈希检索
File MD5 | cf6cb25624874424af47011a7dd131b4 |
File SHA1 | 1d0d2de612c473fc4c75ed5d61952f8e4ad7384c |
File SHA256 | 6f14afb14e198fc36ff839b09077edb2fb5a55dc9c29c9edcd59075d48255332 |
Host | pwn.pwndns.pw |
ip | 168.235.95.104 |
rule muma_unpack {meta:description = "Tsunami:RAT&DDOS_BOT"muma_unpack_hash1 = "4410b1cd507926071378c0c470fa98aff12ed4b59ec00766fef8847c72397c26"muma_hash1 = "6f14afb14e198fc36ff839b09077edb2fb5a55dc9c29c9edcd59075d48255332"strings:$x1 = "NOTICE %s :PAN = An advanced syn flooder that will kill most network drivers" fullword ascii$x2 = "NOTICE %s :SH = Executes a command" fullword ascii$x3 = "NOTICE %s :GET = Downloads a file off the web and saves it onto the hd" fullword ascii$x4 = "NOTICE %s :UDP = A udp flooder" fullword ascii$x5 = "NOTICE %s :UNKNOWN = Another non-spoof udp flooder" fullword ascii$s6 = "NOTICE %s :TSUNAMI = Special packeter that wont be blocked by most firewalls" fullword ascii$s7 = "NOTICE %s :PAN " fullword ascii$s8 = "NOTICE %s :UDP " fullword ascii$s9 = "User-Agent: Mozilla/4.75 [en] (X11; U; Linux 2.2.16-3 i686)" fullword ascii$s10 = "src/process/execve.c" fullword ascii$s11 = "NOTICE %s :UNKNOWN" fullword ascii$s12 = "NOTICE %s :TSUNAMI" fullword ascii$s13 = "NOTICE %s :IRC = Sends this command to the server" fullword ascii$s14 = "src/process/posix_spawn_file_actions_adddup2.c" fullword ascii$s15 = "src/process/posix_spawn_file_actions_destroy.c" fullword ascii$s16 = "src/process/posix_spawn_file_actions_init.c" fullword ascii$s17 = "NOTICE %s :Spoofs: %d.%d.%d.%d - %d.%d.%d.%d" fullword ascii$s18 = "NOTICE %s :Password too long! > 254" fullword ascii$s19 = "NOTICE %s :Password correct." fullword ascii$s20 = "src/process/posix_spawn.c" fullword ascii$y1 = "gent.Mozilla/4.75" fullword ascii$y2 = "PROT_EXEC|PROT_WRITE failed." fullword ascii$y3 = "Id: UPX 3.95 Copyright (C) 1996-2018 the UPX Team. All Rights Reserved. $" fullword ascii$y4 = "NOTICE %s :Unable to comply." fullword ascii$y5 = "Q USERID" fullword ascii$y6 = "ooo.User" fullword ascii$y7 = "KILL " fullword ascii$y8 = "no- wi&-FbZ" fullword ascii$y9 = "" fullword ascii$y10 = ",7V{ -" fullword ascii$y11 = "? -[Bo&" fullword ascii$y12 = "O9/JHTTP/1.0" fullword ascii$y13 = "liheek" fullword ascii$y14 = "assifyl" fullword ascii$y15 = "DEH_FRAME_" fullword ascii$y16 = "%HTF%3" fullword ascii$y17 = "toupbr" fullword ascii$y18 = "%DKz%H" fullword ascii$y19 = "uvbful" fullword ascii$y20 = "1-2%S " fullword asciicondition:( uint16(0) == 0x457f and filesize < 2000KB and ( 1 of (x*) and 4 of (s*) ) ) or( uint16(0) == 0x457f and filesize < 600KB and ( 8 of (y*) ) ) or( all of them )}
如有侵权请联系:admin#unsafe.sh