For those of you who don’t know, Flare-On is an annual “reverse engineering marathon” organized by Mandiant (formerly by FireEye). It runs for 6 weeks, and contains usually 10-12 tasks of increasing difficulty. This year I completed as 103 (solves board here). In this short series you will find my solutions of the tasks I enjoyed the most.
Flare-On Task 10 was related to emulation of an old Macintosh machine, based on Motorola 68000 processor.

You can find the package here: 10_Nur_getraumt.7z , password:
flare
We are provided with the disk image, containing the application that we need to reverse.
The first step was to prepare the emulator. As the author of the task suggested, I used Mini vMac. However, this solution doesn’t just work out of the box. We need to provide it a ROM image (more info here), that is not included on the website. Fortunately, after some googling around I found a github which owner was kind enough to make their ROM available, along with other utilities to be used for vMac:
https://github.com/nyteshade/mini-vmac-setup
After running the emulator with the ROM, it was necessary to install the OS. Fortunately, System 6.0.8 was provided on the vMac site (“SSW_6.0.8-1.4MB_Disk1of2.sea.bin” and “SSW_6.0.8-1.4MB_Disk2of2.sea.bin”). We just need to unpack it with the provided tool (ua608d) and then we can drag-and-drop on the running emulator Window. That’s how we get the working system.
Once the system is up and running, we need to also mount the disk with our challenge. We can do it also by drag-and-drop, but first we need to rename the file to ANSI (I used “chall.img”). And it works! We can see the original compiled application, that is the challenge, and also, the Res Edit by which we can view particular elements of the challenge.
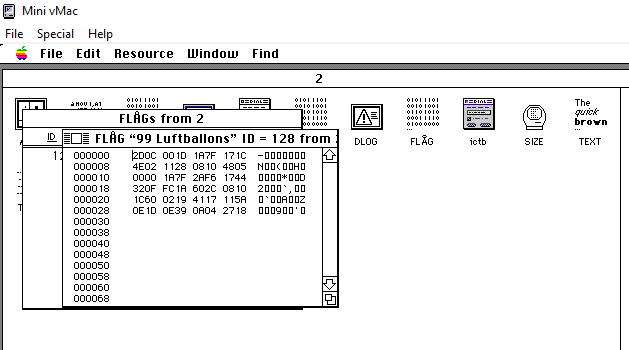
We can see that one of the resources contains our encrypted flag:

As the description suggests, the flag should be viewed in hex. Fortunately, the Reg Edit provides this option in the menu.

This is how the flag looks when viewed in hex:

The task description hints us that the challenge is going to be somehow related with the music of those times. And indeed, the name of the resource points to the song “99 Lufrbaloons” of a German singer Nena.
Walking through various elements displayed in Reg Edit, we can also see the code of the application. It is displayed in a built-in disassembler.

The function is pretty short, and it can be reimplemented knowing some 68000 assembler basics (i.e. following this manual). We can see an EOR (Exclusive OR logical) instruction, which is an equivalent of XOR. At this point we can guess that the flag may be obfuscated with a XOR-based algorithm.
But before jumping to implementation, I wanted some less error prone way to understand this unfamiliar code. And it turns out that it was easier to achieve than I expected. It turns out that Ghidra provides built-in disassembler for this architecture.
But first I needed to carve out the application from the whole image. I installed a hexeditor on the emulator:

… and checked how the program starts.

Then I opened the whole image in a hexeditor on my host machine, and searched for those patterns. Carved out the whole app, and opened it in Ghidra.

We need to go to the beginning of our decoding function, and make Ghidra disassemble it:

And great, we see the same code as we could preview in Res Edit, so it means everything is ok. Plus, there is another view, with this code decompiled.

This is how the decompiled function looks – much more clear, isn’t it?

We can see that the first byte of the string is it’s size. The last WORD, after the characters buffer, is a CRC16 of it.
I reimplemented the whole algorithm in C, to test my assumptions (snippet here). All good… so it turns out to be a simple XOR with the supplied key!
As we know, the flag will end with @flare-on.com – so this is what we need to use to XOR the ending of the provided encrypted string.

This is a part of the first line from the lyrics of Nena’s song “99 Luftbaloons”!.
Hast du etwas Zeit für mich?
Nena – “99 Luftballons”
Dann singe ich ein Lied für dich
If we write the full line, we get:

Which is the second line of the same song. We can fill the missing characters in, and submit the flag.
And that’s all for the task 10!
BTW, the title of the challenge (“Nur geträumt” – “Just a dream”) is also a reference to a Nena’s song.
如有侵权请联系:admin#unsafe.sh