2022-11-9 10:32:7 Author: sandflysecurity.com(查看原文) 阅读量:14 收藏
- Date
- November 09, 2022
- Author
- The Sandfly Security Team
Sandfly's Splunk App has been updated and now has separate inputs to accept our new SSH Key Hunter data feed. SSH Hunter agentlessly collects SSH public key data to track how they can be used for logins across your Linux systems. We are now making that data available to all Splunk users.
Collecting SSH public key data allows Sandfly to build an in-depth view of your SSH credential posture without jeopardizing security by giving access to secret key data during the process.
The SSH key data Sandfly collects can be used in a large number of ways such as the following:
Finding and tracking compromised SSH credentials and users.
Seeing what SSH keys are used on what systems.
Tracking and identifying keys by date first and last seen.
Detecting changes to authorized_keys files including creation and modification times to help with incident response.
Finding key types, duplicate keys, obsolete keys, and more.
The SSH Hunter collects this data agentlessly across all Linux systems watched by Sandfly. This includes not only typical server installations, but also IoT and embedded Linux appliances where traditional agent-based Linux EDR coverage has no visibility.
Tracking SSH Credentials for Compromise
During a breach, the ability to track compromised SSH credentials eliminates a lot of wasted time. Specifically, it allows incident response teams to rapidly contain and remediate breaches where a stolen key is used to initiate lateral movement by attackers.
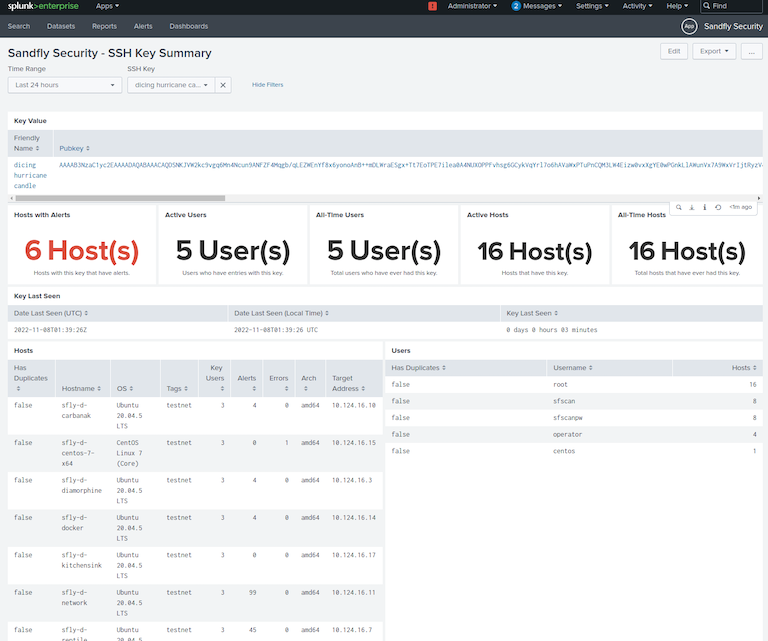
Below we show a sample Splunk dashboard included with the App. The built-in dashboards and sample reports can be quickly taken by SOC teams to incorporate into their own visuals and workflow inside Splunk.
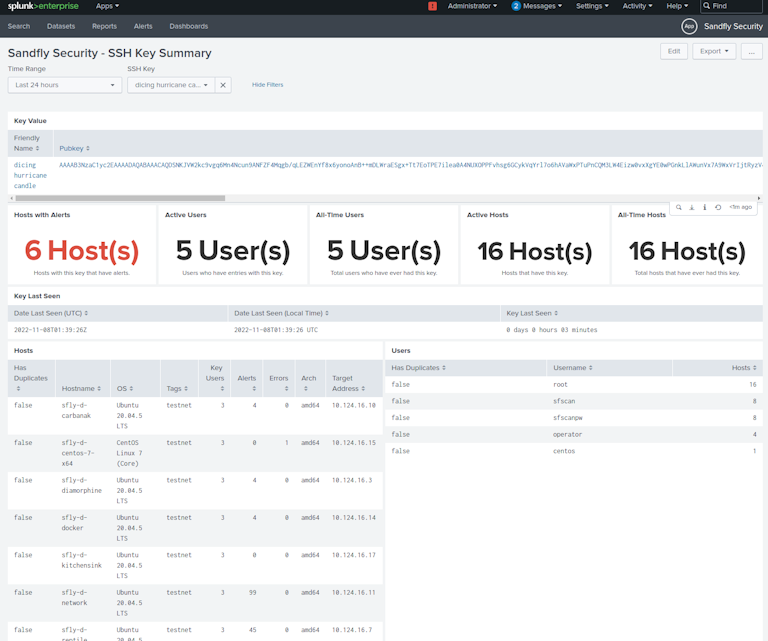
Below we see an example where we isolate all keys seen. Clicking on any key will break out individual results about the key and what hosts it's appeared on over time.
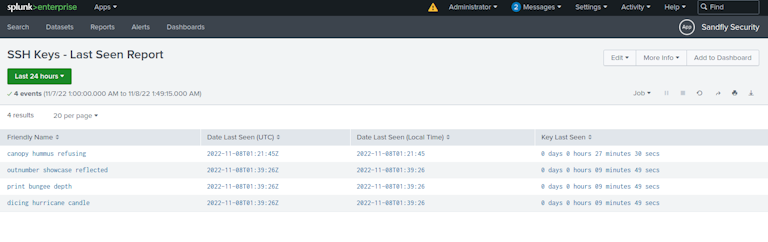
SSH Key Forensics for Incident Response on Linux
The SSH public key data we collect contains extensive information to allow Splunk to query on values such as dates, key types, users, hosts, key cryptographic hashes, and much more.
Splunk users can use this data to build custom reports and alerts such as:
Alerts on new keys seen anywhere.
Alerts on keys showing up for certain hosts or users (e.g. root).
Alerts on banned or old keys returning from the grave on any host.
Queries for known compromised keys and where they've been seen over time.
Reports on key usage statistics, age of keys, and what they are being used for and where.
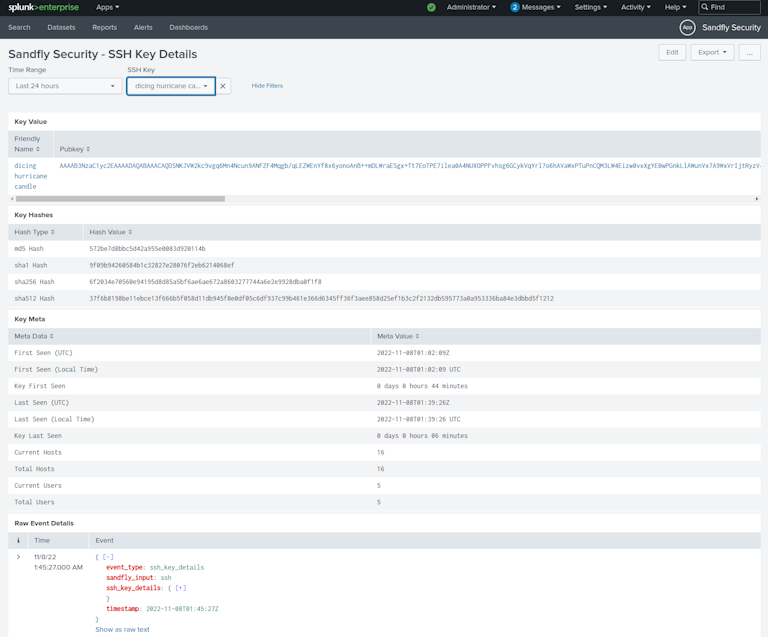
We also have detailed views to build queries for SSH keys inside Splunk. For example, all key fields below in the detailed forensic view can be used to build searches.
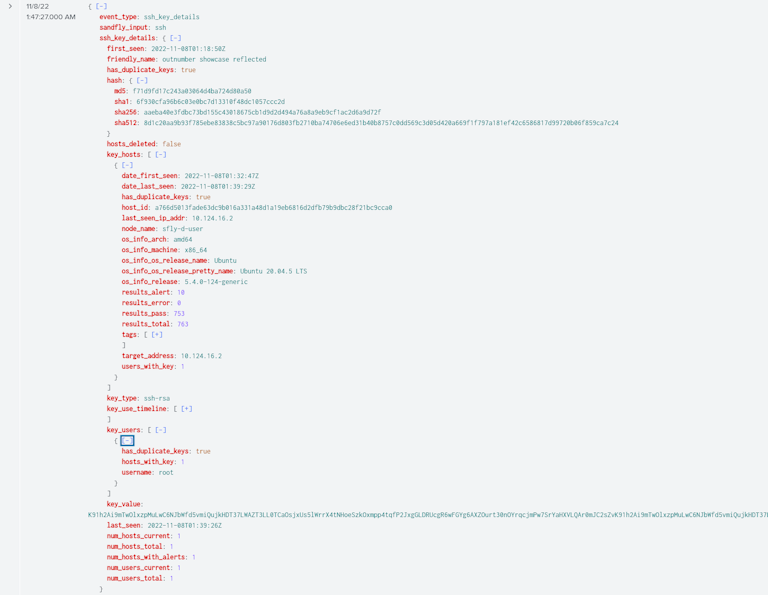
Monitoring SSH Authorized Key Files
Finally, we make available file creation and modification times to detect if an SSH authorized_keys file has been created or altered. The data shows specific users and full paths to the file for rapid identification and response.
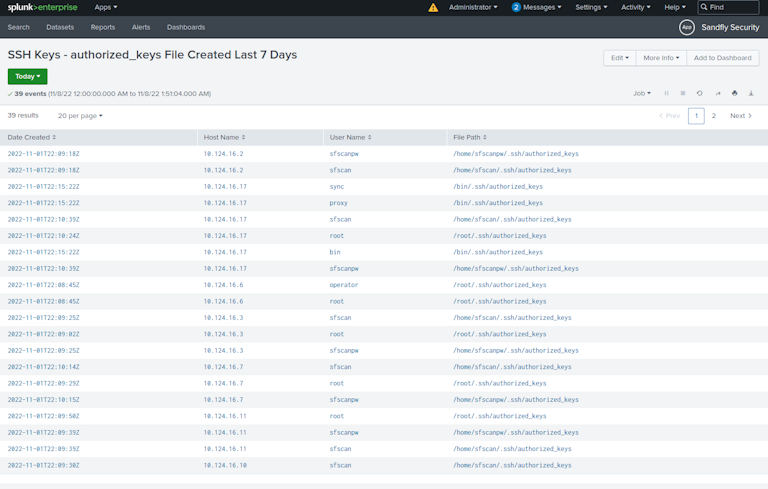
SSH Key Tracking Agentlessly and Fast
Tracking SSH keys on Linux is an important task and is not found in traditional Linux EDR tools. Sandfly's agentless security platform not only collects this data instantly, but processes it to make it immediately useful for Splunk users hunting for compromised SSH credentials.
Licensed customers of Sandfly can use our Splunk App for free. Please contact us if you have any further questions or would like a demo of how Sandfly's SSH Hunter can help.
如有侵权请联系:admin#unsafe.sh