2022-10-13 11:16:40 Author: sandflysecurity.com(查看原文) 阅读量:16 收藏
Sandfly 4.2 has been released and features a new automatic host discovery for cloud and DHCP environments. Plus, it has been significantly optimized to be more than twice as fast with lower CPU usage.
In addition to this, we have many other upgrades:
SSH Hunter has more details on keys no longer present on any host (dead keys).
Improved container process data collection and detection.
New SSH known_hosts detection and collection.
New sudoers persistence and upgraded security checks.
Improved scheduler tagging and bulk operations.
Generation of SSH keys inside UI to secure private key from operators.
TLS configuration and custom signed certificate options.
Automatic Host Discovery
Being agentless means Sandfly can rapidly deploy against a wide range of Linux systems without leaving anything running on the endpoints. We now make this easier than ever with our new ability to automatically find and add hosts to Sandfly using Discovery Scans.
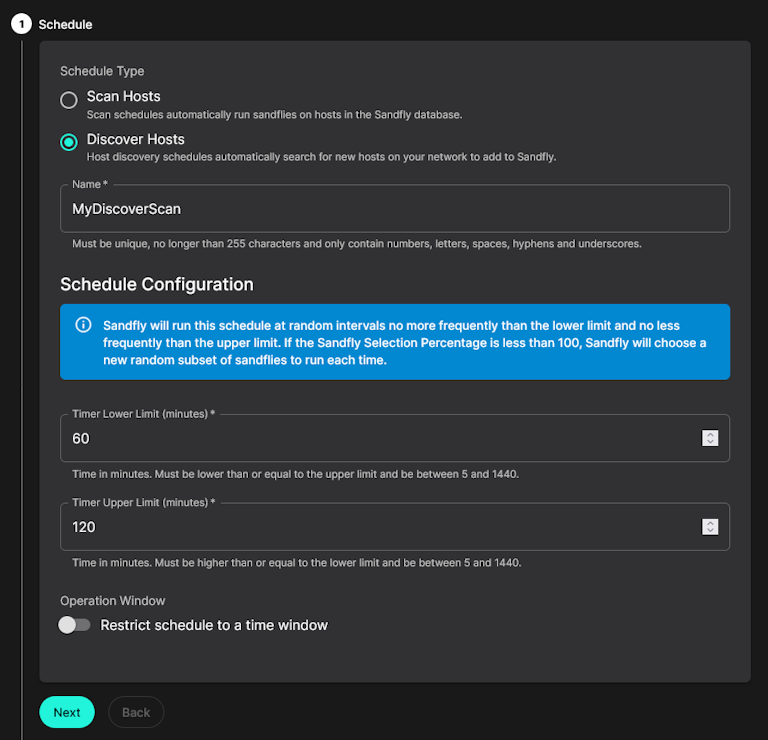
A Discovery Scan can take either a pre-defined list of addresses, or multiple netblocks of your choice. They can be located at a cloud provider, or internally. Once added, Sandfly will automatically scan those ranges for any new hosts. If a new host is found, we will attempt to add it to the protected host list automatically.
Discovery Scans enable the following use cases:
Automatically monitor a DHCP address pool for new Linux hosts.
Secure address ranges and dynamic workloads at your cloud provider.
Find new hosts that may have appeared on your network which are unauthorized.
This new feature significantly expands the ability of Sandfly to discover, track, scan and secure Linux assets. In-depth documentation on how to use the Discovery Scan feature is available here:
Automatic Offline Host Removal
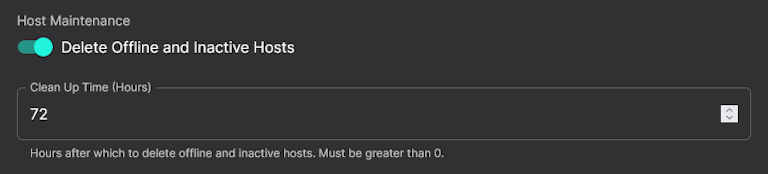
To compliment the automatic host discovery, we have added a feature to remove hosts that have been offline for a user-defined time period. This feature means you can have a dynamic pool range that is automatically maintained without any intervention. New hosts are added with Discovery Scans, and if they go away they are removed from the active pool making that slot available to any new hosts that show up again.
This feature is configurable in the scheduled scans area and can be applied to a range of hosts by tag so you can have different expiration times for different tag groups.
More information on configuring security scans is available here:
Optimized Forensic Engines Twice as Fast
We have further optimized our forensic engines so that they are at least twice as fast for many scanning operations. Customers will see scans complete much faster with even lower CPU and RAM impacts.
SSH Dead Key Monitoring
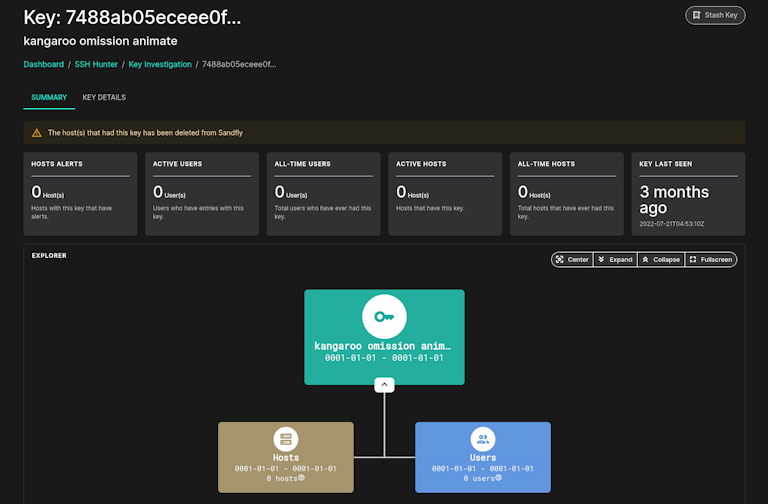
SSH Hunter has new columns to show additional key information, including tracking of dead keys (keys that were seen at one time, but are now not visible on any hosts). If these keys come active again they will return to the active state. The SSH Hunter timeline will show all periods we first saw the key until it returned.
Improved Container Threat Detection
We have improved detection of threats inside containers to provide expanded coverage of Docker and Podman platforms. Sandfly will search for more container types and search for process, file, directory and other threats both on the host OS and inside containers that it is running.
SSH known_hosts Tracking
We are now tracking user's SSH known_hosts files to give administrators more insight into how they are being used and potentially abused.
SSH known_hosts data is attached to all user forensic data we see on the host. This includes parsing out the fields into relevant blocks for quick analysis and review. The excerpt below shows unmasked SSH known_hosts entries available in the raw forensic data view.
{
"known_hosts": {
"data": [{
"path": "/home/system/.ssh/known_hosts",
"type": "ssh-ed25519",
"entry": "10.1.1.10 ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIIXASDFASDFASDFASDFASDF/PZsEDAJOK5CkKUZBm2ija",
"marker": "",
"masked": false,
"revoked": false,
"entry_num": 1,
"hostnames": [{
"port": 22,
"hostname": "10.1.1.10"
}],
"public_key": "AAAAC3NzaC1lZDI1NTE5AAAAIIXASDFASDFASDFASDFASDF/PZsEDAJOK5CkKUZBm2ija",
"masked_salt": "",
"masked_value": "",
"cert_authority": false
},
{
"path": "/home/system/.ssh/known_hosts",
"type": "ssh-ed25519",
"entry": "10.1.1.16 ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIADFASDFASDFASDFASDFASDFASDF/QK52K",
"marker": "",
"masked": false,
"revoked": false,
"entry_num": 2,
"hostnames": [{
"port": 22,
"hostname": "10.1.1.16"
}],
"public_key": "AAAAC3NzaC1lZDI1NTE5AAAAIADFASDFASDFASDFASDFASDFASDF/QK52K",
"masked_salt": "",
"masked_value": "",
"cert_authority": false
}
]
}
}This data can be ingested into your SIEM for further tracking, but Sandfly also has detections for problems of its own as discussed below.
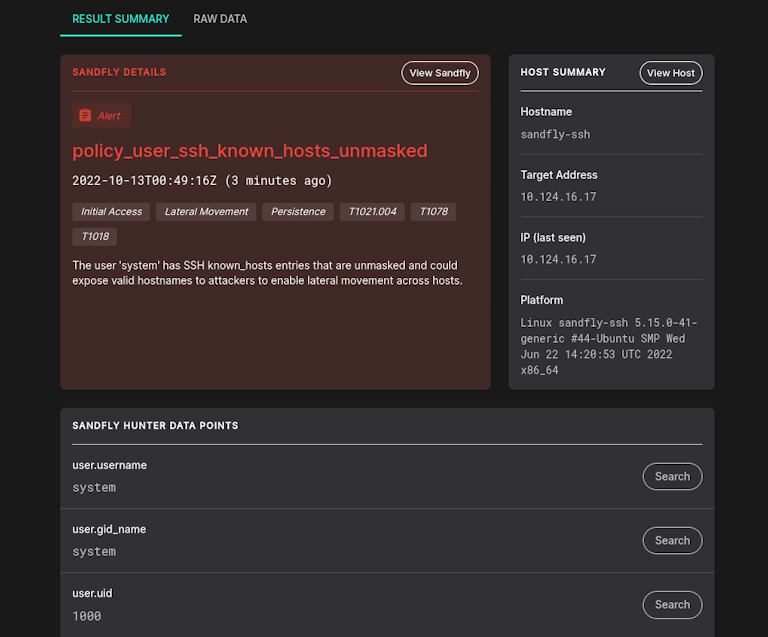
Unmasked SSH known_hosts Entries
We can alert you to users with unmasked SSH known_hosts entries with a new policy check. Unmasked SSH entries leak connection information and allow intruders an immediate list of systems to attack if it is available. Linux malware often will search for known_hosts files to harvest IP addresses as part of their automated attack sequence.
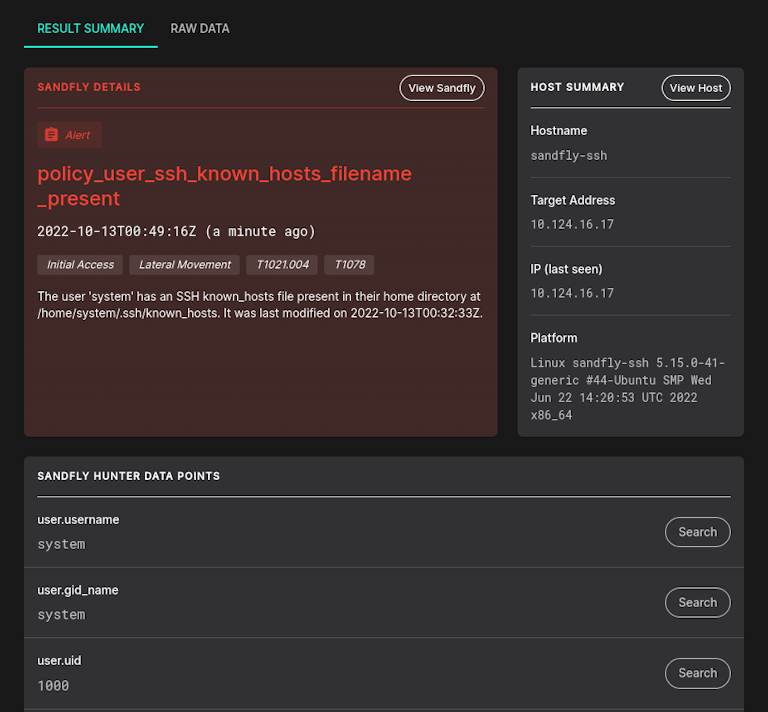
Detecting if SSH known_hosts is Present
One less obvious use for searching for known_hosts files is to let you know if one is present. If you are running a group of servers that should never have users that are doing SSH outbound, it is useful to know if a user has tried it and left a known_hosts file behind. This alerts you to suspicious SSH activity inside perimeters that may have evaded network monitoring.
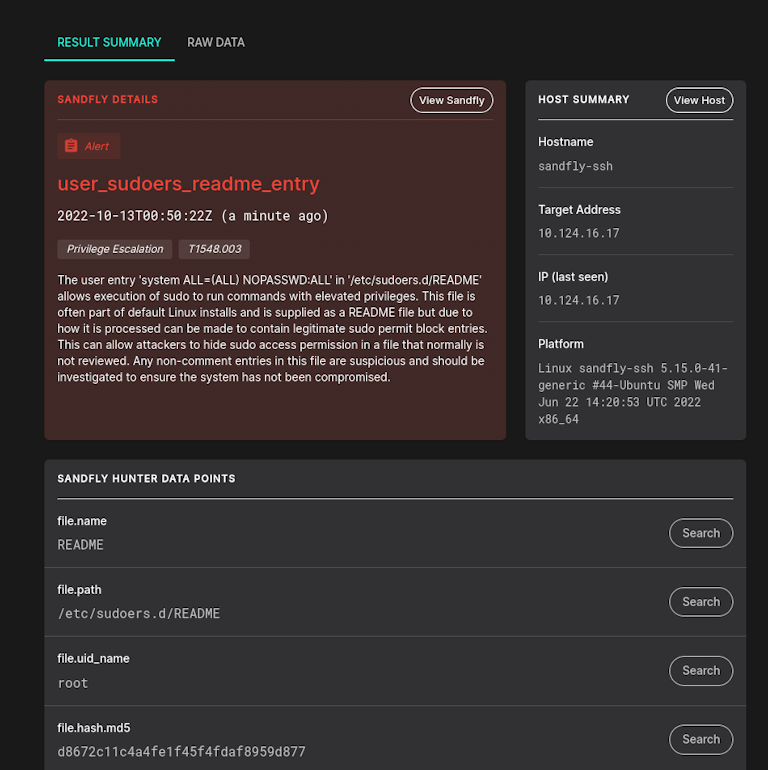
Sudoer Persistence and Other Threat Detection Improvements
We have added in modules to find new methods for persistence in /etc/sudoers files and more. Other updates to existing threat hunting modules to expand coverage and reliability have been made as well.
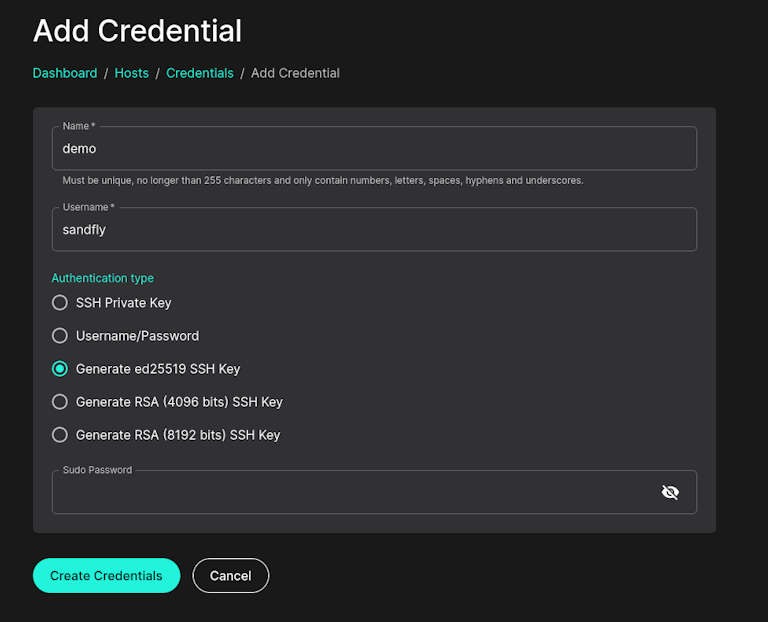
Generate SSH Keys During Credential Creation
Sandfly can generate a public/private key pair from the UI directly during credential creation. The private key is encrypted as usual inside the server and cannot be retrieved. Only the public key can be seen by the operator. This allows staff to generate keys for automated deployment tools without exposing the private keys for login access.
New TLS Override and Certificate Options
The server configuration allows you to relax our normally strict TLS options for better browser and API compatibility with older clients.
If you have your own signed certs, you can now drop them under the sandfly-setup directory and they will be read in on server start. Please see the following for more information:
Installing a Custom Signed Certificate
Scheduler Tags and Bulk Pause/Resume/Delete
You can now exclude as well as include hosts based on their tags. For instance, you can setup a schedule to include hosts tagged "www" but not those with the tag "www-dev" in the same tag group. You can also combine the tags with AND/OR operators.
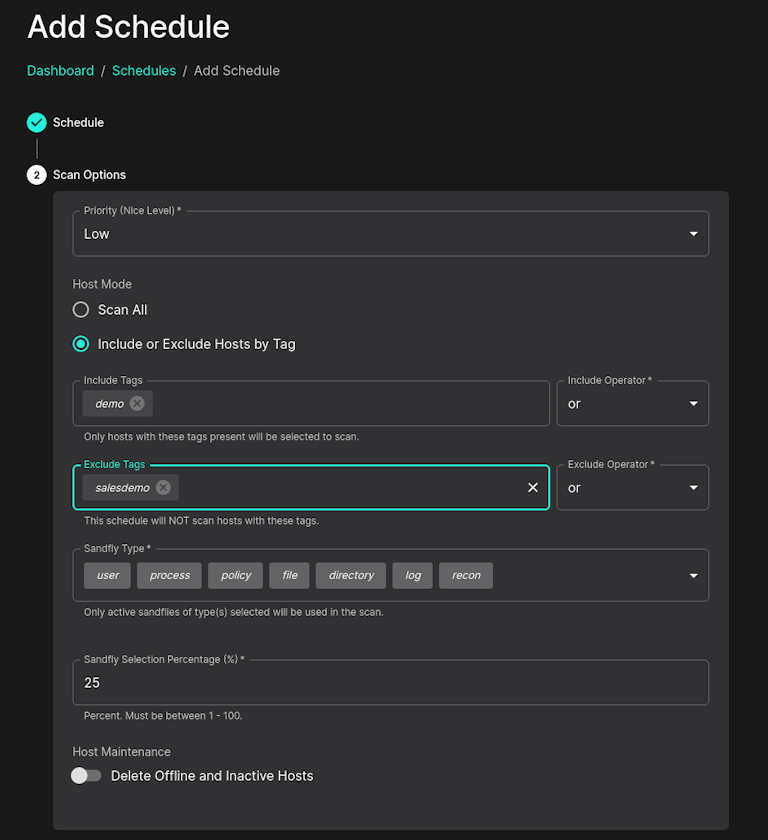
Additionally, you can now select multiple schedules at once to do bulk operations such as pause, resume, or delete.
Free Updates
All users are eligible for updates to 4.2. The update is in-place and requires no changes on your part to run it today. Upgrade instructions are below:
The SSH Hunter feature is for licensed customers only. If you'd like to try out the SSH Hunter in your environment, please contact us and we can send you a full license for evaluation.
Thank you for using Sandfly.
如有侵权请联系:admin#unsafe.sh