
2022-11-21 09:40:49 Author: sandflysecurity.com(查看原文) 阅读量:49 收藏
Decloaking Linux stealth rootkits that are hiding processes from view is easy with our free tool sandfly-processdecloak which has been updated below:
sandfly-processdecloak on Github
This free tool is able to quickly decloak process hiding activity from Loadable Kernel Module (LKM) stealth rootkits on most Linux distributions and architectures. It has the following features:
Works instantly without hooking into the kernel and causing system instability or compatibility nightmares.
Static build so incident response teams can deploy even onto systems with compromised shared libraries to investigate an incident and get accurate results.
Multi-architecture build scripts for Intel, AMD, Arm and MIPS processors.
How Does It Work?
We us a concept called PID busting. Basically we look at what the /proc table in Linux says is running for processes. Then, we iterate through available process IDs and see if they match. If there is a mismatch, then there is high likelihood a rootkit is hiding something from observation.
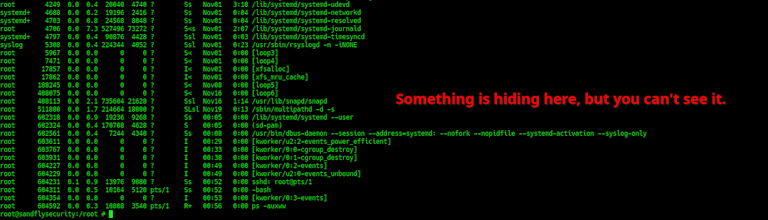
Below you can see what the process listing command ps shows on an infected system. There is a process that has been hidden, but it won't show up with command line tools.
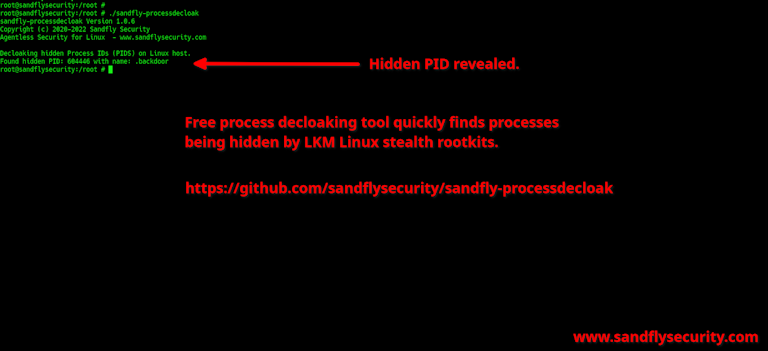
After running sandfly-processdecloak the hidden PID becomes immediately apparent.
Investigating Suspicious Process
Once the PID has been decloaked, you can use standard process investigation methods to see what is happening. Please see this article for how to do process forensics on Linux:
Basic Linux Malware Process Forensics for Incident Responders
Automate Stealth Rootkit Detection Agentlessly
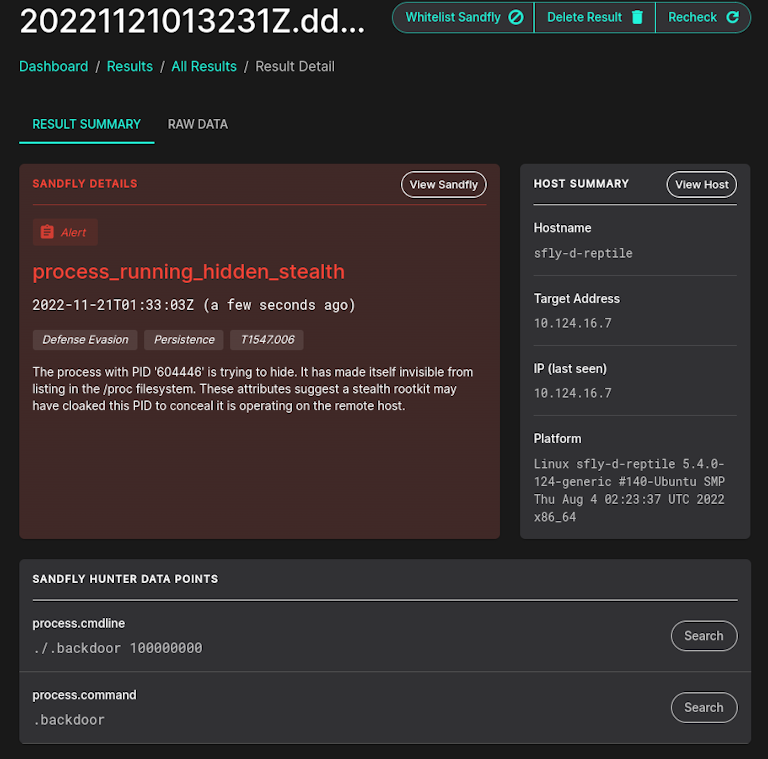
The free tool can be easily scripted for automated checks, but a far easier way to do this is let Sandfly's agentless security platform do it for you 24/7. We not only can decloak hidden processes, but can also find thousands of other threats against your Linux systems without loading any endpoint agents. Check out our free license or contact us for a full trial.
如有侵权请联系:admin#unsafe.sh