2021-12-22 00:55:42 Author: sandflysecurity.com(查看原文) 阅读量:10 收藏
Sandfly 3.1 offers major performance enhancements while reducing the resources needed to protect your Linux systems.
Sandfly Fights CronRAT
We have added in new checks for malware tactics used in CronRAT Linux malware and more. We could find this type of malware already, but have added new hunting modules for suspicious cron command entries to make detection even more complete.
75% Less RAM Needed
Our server uses a new PostgreSQL database and this has resulted in dramatically lower RAM requirements while providing a big boost in performance. This new version uses 75% less RAM vs. previous. Many customers can install Sandfly's server on inexpensive cloud instances to protect their Linux systems without sacrificing any performance.
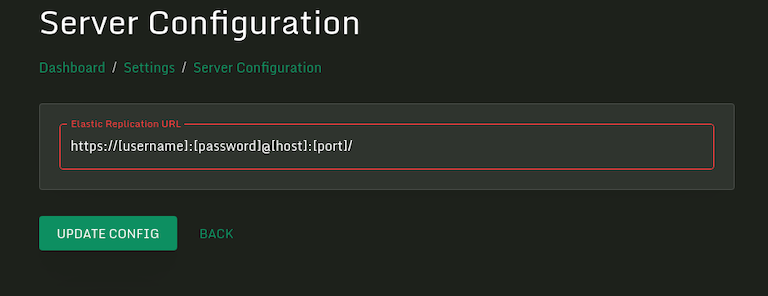
Easily Export Events to Elasticsearch & Splunk
While Splunk users can still use our certified Splunkbase app to send all Sandfly events directly to Splunk, we’ve made Elasticsearch event export easier by including it in the UI. Simply put in your cluster's URL and authentication information to ingest Sandfly events directly into your Elasticsearch instance.
Improved Syslog Event Output for Graylog and Other SIEM Tools
For customers using Sandfly to send syslog output, we have improved the formatting in the result data. Syslog enabled SIEM products such as Graylog and QRadar now receive more detailed information directly from Sandfly events.
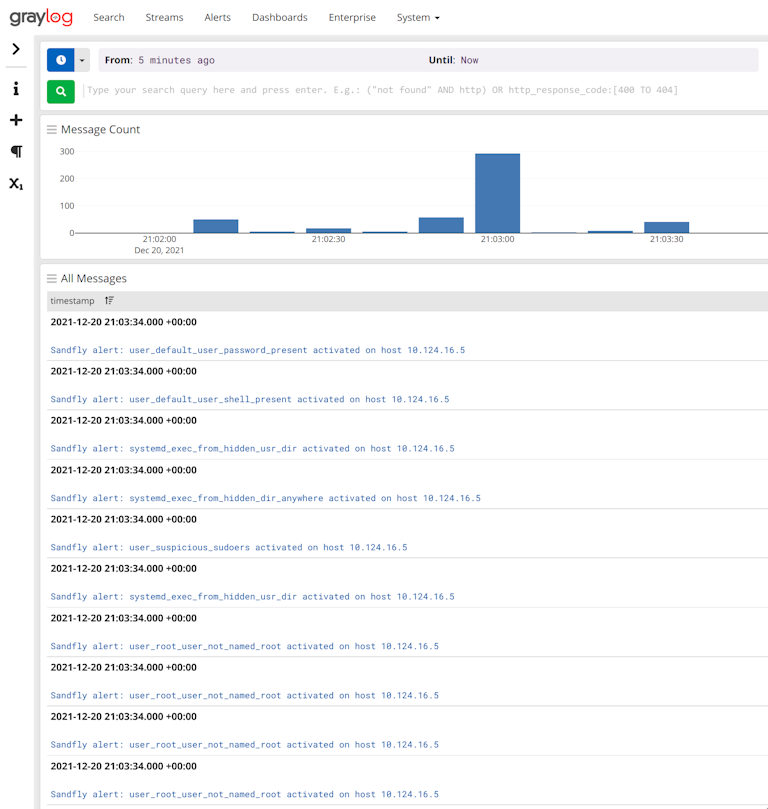
Faster Filtering and Host Views
Sandfly gives in-depth information about what Linux systems are running without loading any agents on your endpoints. Now, results filtering is faster with more options on how to view it. Enhanced host views show critical Linux operating system data quickly with our agentless asset discovery capability.
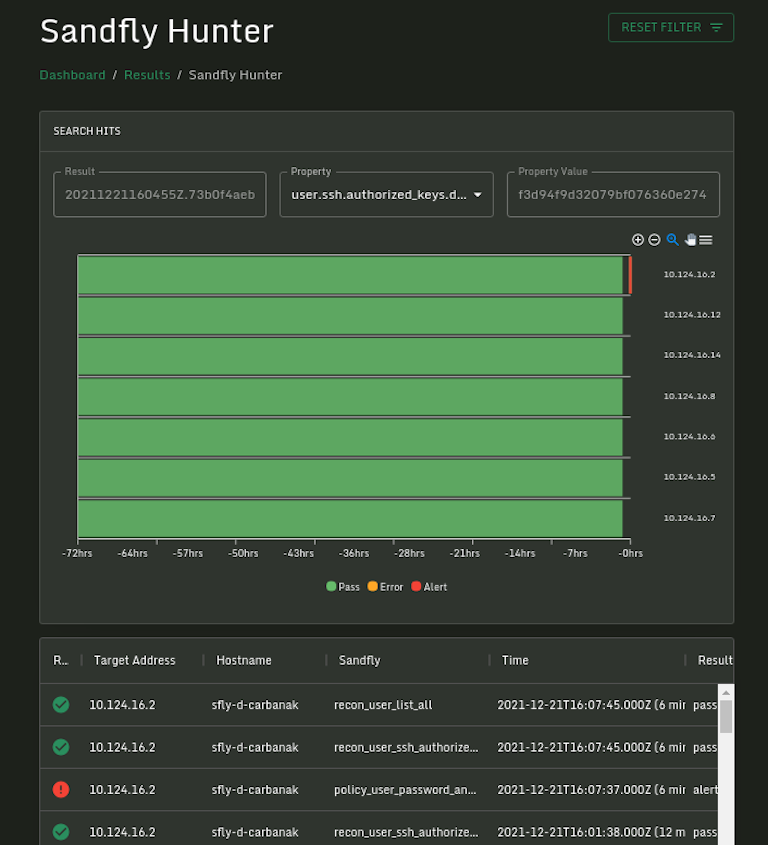
Sandfly Hunter Improved
Fully licensed users get access to Sandfly Hunter to search for forensic artifacts instantly. Use Sandfly Hunter to search for files, processes, users, log entries, SSH keys and more as part of an incident to help quickly find and isolate compromised hosts. In this release Sandfly Hunter has been improved with faster forensic artifact hunting than before.
Seamless, Free Upgrade from 3.0 to 3.1
All free and paid customers can upgrade today. Please see the upgrade documentation for how to quickly and easily upgrade.
Protect 500 Linux Systems Now for Free
Sandfly is still offered for free to help you immediately start monitoring and protecting your Linux fleet. Start now with an instant no-obligation license.
Thank you for using Sandfly. Please contact us with any questions or comments.
如有侵权请联系:admin#unsafe.sh