vpn连接
测试网络
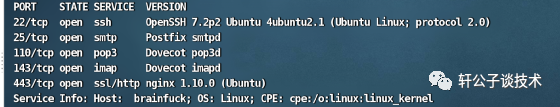
ping 10.10.10.17端口扫描
nmap -sV 10.10.10.17 -p1-65535漏洞扫描
存在dos漏洞
查看443是nginx页面,证书信息发现了邮件地址和两个域名
www.brainfuck.htb sup3rs3cr3t.brainfuck.htb
写进hosts尝试访问下,也叫host碰撞
10.10.10.17 brainfuck.htb www.brainfuck.htb sup3rs3cr3t.brainfuck.htbhttps://brainfuck.htb
是wordpress框架,弱口令没爆出来
利用wpscan测试漏洞
wpscan --url https://brainfuck.htb --disable-tls-checks查找脚本,7.1.3 存在两个漏洞一个是sql,一个是权限提升
测试发现权限提升的存在
访问poc.html
后台登陆
刷新页面,发现已经登陆,访问后台
https://brainfuck.htb/wp-admin/options-general.php?page=swpsmtp_settings翻后台找能getshell的地方,找了一圈发现了smtp密码
orestiskHGuERB29DNiNE
翻密码
前面nmap也扫到了110端口,可以进邮件看看有没有什么敏感信息
orestiskIEnnfEKJ#9UmdO
有发现了一处密码,有密码就会有登陆点
看不懂,翻译下
找到了类似链接的东西
这里懵逼了,不知道怎么搞了,看了oscp的博客
破解ssh
>>> enc = "Pieagnm - Jkoijeg nbw zwx mle grwsnn">>> pt = "Orestis - Hacking for fun and profit">>> assert len(enc) == len(pt)>>> list(zip(enc, pt))[('P', 'O'), ('i', 'r'), ('e', 'e'), ('a', 's'), ('g', 't'), ('n', 'i'), ('m', 's'), (' ', ' '), ('-', '-'), (' ', ' '), ('J', 'H'), ('k', 'a'), ('o', 'c'), ('i', 'k'), ('j', 'i'), ('e', 'n'), ('g', 'g'), (' ', ' '), ('n', 'f'), ('b', 'o'), ('w', 'r'), (' ', ' '), ('z', 'f'), ('w', 'u'), ('x', 'n'), (' ', ' '), ('m', 'a'), ('l', 'n'), ('e', 'd'), (' ', ' '), ('g', 'p'), ('r', 'r'), ('w', 'o'), ('s', 'f'), ('n', 'i'), ('n', 't')]>>> [ord(e)-ord(p) for e,p in zip(enc, pt)][1, -9, 0, -18, -13, 5, -6, 0, 0, 0, 2, 10, 12, -2, 1, -9, 0, 0, 8, -13, 5, 0, 20, 2, 10, 0, 12, -2, 1, 0, -9, 0, 8, 13, 5, -6]>>> [(ord(e)-ord(p))%26 for e,p in zip(enc, pt)][1, 17, 0, 8, 13, 5, 20, 0, 0, 0, 2, 10, 12, 24, 1, 17, 0, 0, 8, 13, 5, 0, 20, 2, 10, 0, 12, 24, 1, 0, 17, 0, 8, 13, 5, 20]>>> [(ord(e)-ord(p))%26 + ord('a') for e,p in zip(enc, pt)][98, 114, 97, 105, 110, 102, 117, 97, 97, 97, 99, 107, 109, 121, 98, 114, 97, 97, 105, 110, 102, 97, 117, 99, 107, 97, 109, 121, 98, 97, 114, 97, 105, 110, 102, 117]>>> [chr((ord(e)-ord(p))%26 + ord('a')) for e,p in zip(enc, pt)]['b', 'r', 'a', 'i', 'n', 'f', 'u', 'a', 'a', 'a', 'c', 'k', 'm', 'y', 'b', 'r', 'a', 'a', 'i', 'n', 'f', 'a', 'u', 'c', 'k', 'a', 'm', 'y', 'b', 'a', 'r', 'a', 'i', 'n', 'f', 'u']
关键是像“fuckmybrain”或“mybrainfuck”或者“brainfuckmy”之类的密钥。
https://rumkin.com/tools/cipher/vigenere/。 解密网站
最终得到ssh密钥
https://brainfuck.htb/8ba5aa10e915218697d1c658cdee0bb8/orestis/id_rsa这里登陆失败了
登陆ssh
应该是需要密码
ssh2john.py将密钥信息转换为john可识别信息
爆破密码
john --wordlist=/usr/share/wordlists/rockyou.txt mima重新生成rsa无密码(也可以直接输入密码登陆)
openssl rsa -in id_rsa -out no_rsaEnter pass phrase for id_rsa: 3poulakia!
登陆ssh -i no_rsa orestis@10.10.10.17
获取flag
这里获取了user的flag,然后提权,找root的
这个应该是解密脚本,两外两个是加密数据
谷歌搜相关代码
https://crypto.stackexchange.com/questions/19444/rsa-given-q-p-and-e
749302577646506281962992147553524167446082679278552088138715834326527417000928250488494103985293310916319365183030330831256558044566928484722553516652030770208545277875667354588583815554526483228450082666129068448479370703334803739632841466490742522787536968972458984332459297755910917742746520213741431740793080200791795250842279286902168919392748501633271362252702521910515425447234462728494777972628099543194745429278242631325552313761053232381371448363943425753683006276828637792001084185034683723801557146475507466937311041187033170697457349891212664140982185567858180446760882417750897625475931921095597705399744641914821074071930297814589851746700593470770417111804648920018396305246956127337150936081144106405284134845851392541080862652386840869768622438038690803472550278042463029816028777378141217023336710545449512973950591755053735796799773369044083673911035030605581144977552865771395578778515514288930832915182def egcd(a, b):x,y, u,v = 0,1, 1,0while a != 0:q, r = b//a, b%am, n = x-u*q, y-v*qb,a, x,y, u,v = a,r, u,v, m,ngcd = breturn gcd, x, ydef main():p = 7493025776465062819629921475535241674460826792785520881387158343265274170009282504884941039852933109163193651830303308312565580445669284847225535166520307q = 7020854527787566735458858381555452648322845008266612906844847937070333480373963284146649074252278753696897245898433245929775591091774274652021374143174079e = 30802007917952508422792869021689193927485016332713622527025219105154254472344627284947779726280995431947454292782426313255523137610532323813714483639434257536830062768286377920010841850346837238015571464755074669373110411870331706974573498912126641409821855678581804467608824177508976254759319210955977053997ct = 44641914821074071930297814589851746700593470770417111804648920018396305246956127337150936081144106405284134845851392541080862652386840869768622438038690803472550278042463029816028777378141217023336710545449512973950591755053735796799773369044083673911035030605581144977552865771395578778515514288930832915182# compute nn = p * q# Compute phi(n)phi = (p - 1) * (q - 1)# Compute modular inverse of egcd, a, b = egcd(e, phi)d = aprint( "n: " + str(d) );# Decrypt ciphertextpt = pow(ct, d, n)print( "pt: " + str(pt) )if __name__ == "__main__":main()
n: 8730619434505424202695243393110875299824837916005183495711605871599704226978295096241357277709197601637267370957300267235576794588910779384003565449171336685547398771618018696647404657266705536859125227436228202269747809884438885837599321762997276849457397006548009824608365446626232570922018165610149151977pt: 24604052029401386049980296953784287079059245867880966944246662849341507003750
python -c "print format(24604052029401386049980296953784287079059245867880966944246662849341507003750,'x').decode('hex')"6efc1a5dbb8904751ce6566a305bb8ef
文章来源: http://mp.weixin.qq.com/s?__biz=MzU3MDg2NDI4OA==&mid=2247487346&idx=1&sn=ceb2d875aa8852833513df9dffe6b29d&chksm=fce9a8bdcb9e21ab7ada0d910dd0bc7f7593de963cf8b7f84e5ca72472f2b5f3a4b516aeba36#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh