
2022-12-12 22:28:2 Author: www.sentinelone.com(查看原文) 阅读量:17 收藏
It’s no secret that social engineering is a powerful tool in a cybercriminal’s arsenal. Threat actors use psychological manipulation to convince unsuspecting users to hand over their passwords, personal information, or money. To date, social engineering attacks have served as the most common tool to gain initial foothold and perform lateral movement in the network.
In this post, we discuss the dangers of social engineering and how to combat them. We cover common social engineering techniques used by cybercriminals, uncover real-world social engineering-based attack paths, and explain what organizations can do to decrease the risk.

Prominent Types of Social Engineering Attack Techniques
There are several social engineering attack techniques. However, those who are the most frequently seen as part of cyber-attacks that target enterprises are:
Phishing
One common social engineering technique is phishing. This is where cybercriminals send out emails that appear to be from a legitimate source, such as a bank or an online retailer.
Be very cautious of the email on a Friday evening at 4 PM, when you are about to leave for the weekend, from your e-commerce company asking you to click on the link to process your refund, to check some unusual activity or open some attachment. Other good examples of common phishing tricks can be found here.
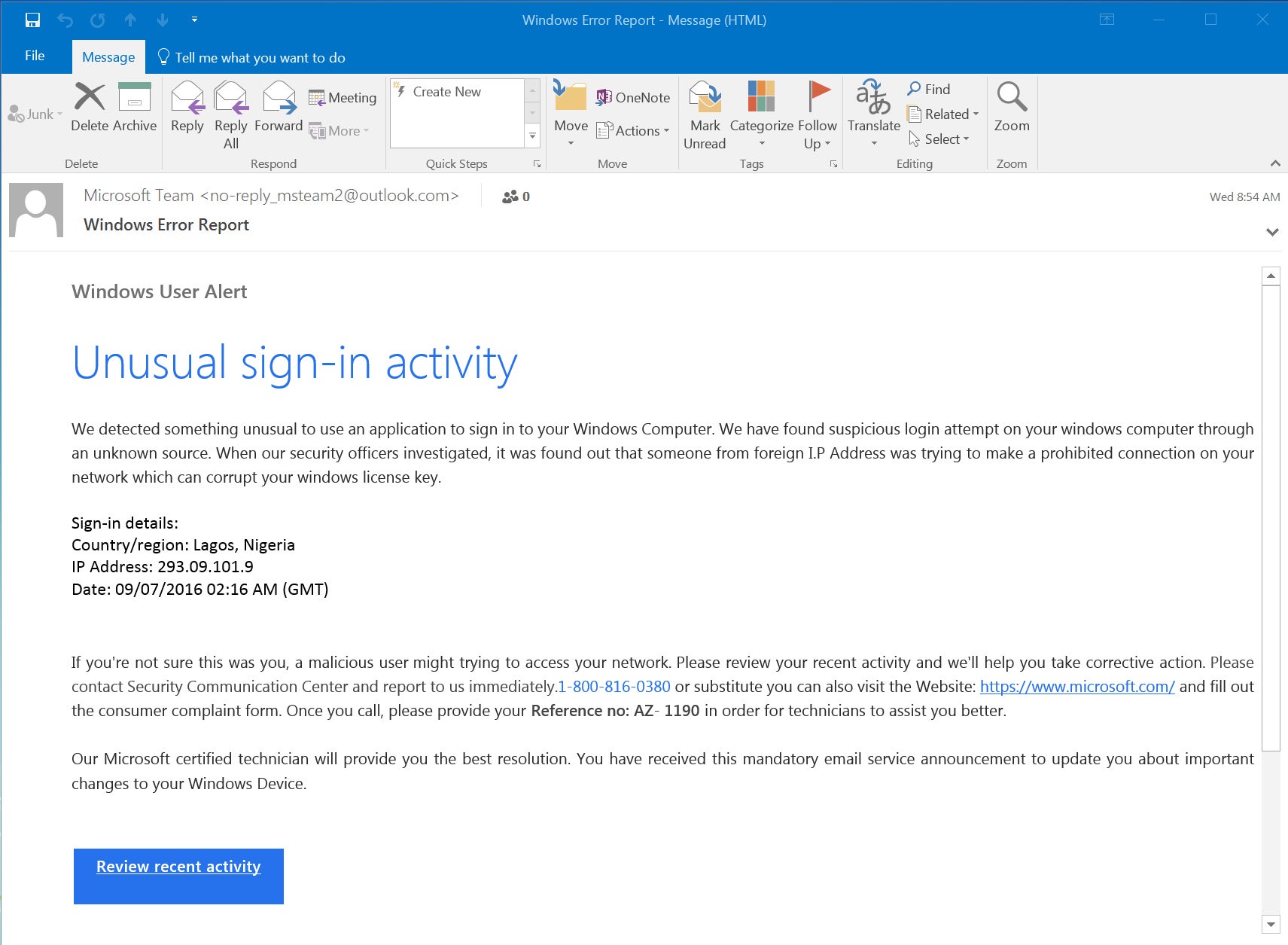
The email may contain a link that leads to a fake website that looks identical to the real one. Once the user enters their login details, the cybercriminal can access their account.
Real-World Attack Example
In May 2021, with the ransomware attack on the Colonial Pipeline, millions of Americans experienced first-hand the impact of cyber attacks. During that cyber attack, the company was forced to stop all operations after its network got compromised. Cybercriminals were able to breach Colonial Pipeline through a targeted phishing campaign that gave them access to an employee’s user credentials which allowed them to start their ransomware attack from within the enterprise network.
Baiting
Another social engineering technique is baiting. This is where the cybercriminal leaves a USB drive or other types of storage devices in a public place, such as a parking lot. When someone finds the device and plugs it into their computer, the device will trigger specific actions targeted at the organization systems, infecting them with malware that eventually will lead to allowing attackers to gain access, or simply launch a destructive attack
Real-World Attack Example
The Federal Bureau of Investigation (FBI) recently warned that cybercriminals are performing so-called ‘BadUSB’ attacks. Malicious USB thumb drives are sent through the United States Postal Service and United Parcel Service, impersonating the US Department of Health and Human Services, claiming to be COVID-19 infection warnings.
Whaling / Business Email Compromise (BEC)
Phishing attacks that are targeted to high profile employees in an organization such as C-suite, VP, etc, is known as Whaling. Business email compromise (BEC), on the other hand, looks to impersonalize company executives to trick a normal user into performing certain activities. Both whaling and BEC require planning and study of the normal behavioral patterns and potentially result in much higher value outcomes.
Social engineering can also take place over the phone. This is known as vishing. The caller pretends to be a legitimate executive of an organization (BEC) and tries to trick the user into revealing sensitive information, such as credit card numbers or social security numbers.
Real-World Attack Example
A Chief Executive Officer (CEO) of a UK-based organization received a phone call from someone who sounded just like the CEO of the parent company, whereas the cybercriminal asked the victim to transfer $243,000 to a supplier. This was possible as the cybercriminal leveraged Artificial Intelligence to mimic the chief executive’s voice. With that in mind, it’s clear that vishing has evolved, and it’s no longer just the random scam calls that defenders must consider a threat.
Protection Against Social Engineering
As with anything with cyber security, it is always a fine balance between people, processes, and technology. Social engineering is the art of psychological manipulation.
Most victims fall prey to social engineering attacks unmindfully without having any malafide intentions. However, social engineering attacks are evolving to lure people into mindfully clicking on certain links or sharing confidential information.
As such, organizations must start with the people aspect and build a security-aware culture by investing in end-user cyber awareness. Naturally, as organizations build a formal end-user awareness program, the next center of focus will be on processes. Employees must know how to report social engineering attacks to the security teams.
Security teams need technologies that help them protect, detect, and respond to these attack techniques, which often span across email, identity, and the endpoint. In practice, all this is achieved through a comprehensive cyber security program that acknowledges the risk associated with social engineering.
Defense Begins with Awareness and Training
When an employee receives an email that looks suspicious, it is imperative to train them to recognize such emails and not to click on links or open attachments but instead report it to the security team.
Staff should be made aware of threat actor tactics such as calls that impersonate a supplier, colleague, or manager and ask for personal information or organizational details. Training employees to understand how to identify a potential phishing attack and how to report it can prevent a serious compromise.
Similarly, unidentified USB drives lying around in public places, in the corporate parking lot and elsewhere have been used in real-world and simulated attacks. Ensure employees understand they shouldn’t plug unknown devices into their endpoints, and instead turn them over to the IT or Security team. Device control can also help mitigate this kind of behavior.
Employee education is critical. Organizations should provide regular training covering social engineering techniques and how to spot them.
These proactive measures help in building the foundational resilience against phishing attacks. However, this should be taken a level higher by imbibing the sense of responsibility among the employees by empowering them and letting them use cyber judgment. Helping them understand and implement ‘If you see something, say something’ to be the eyes and ears on-ground and they are equally important for securing the organization & its mission.
Empower Users with Clarity and the Confidence to Report Suspicious Activity
Organizations should have policies and procedures in place for dealing with suspicious emails, phone calls, and other communications. Providing employees with a simple, clear process for reporting social engineering attempts so that they can be investigated and stopped before any damage is done is a fundamental to enterprise security.
Cybersecurity teams should give clear and uncomplicated instructions to prevent any delay or unwillingness to report suspicous activity, and a firm When in doubt, Stop and Report It’ message should be communicated frequently to staff. Give assurance to the employees that they won’t be penalized for a delay in action or for reporting something they find suspicous, even if it may be determined as non-malicious later. Fostering the cyber empowerment culture is hugely important.
Testing the resilience against phishing attacks is equally important; hence, it is important to conduct phishing simulation exercises to assess the level of readiness in the organization. Phishing simulations are a useful assessment tool to evaluate employee’s resilience against phishing emails, but the same tool won’t be effective for intentional clicks by employees.
Simulation tests should only be done after you have attained a certain level of maturity in imparting cyber training and awareness among the employees and simulation isn’t used to name and shame the employees who may fail the test. The test should be followed by a training to close the loop.
Leverage Technology To Counter Social Engineering
From a technology perspective, there are several security controls that organizations can evaluate that will reduce the risk of social engineering-based attacks:
- Multi-Factor-Authentication (MFA): Although MFA bypass methods exist as manipulating an employee to share their one-time password, implementing MFA can reduce the threat of social engineering-based attacks.
- Additional Authentication: In case of business email compromise attacks (BEC) where a high-level executive is being impersonated, double checking using an offline method such as a voice call in response to an email marking the urgency should be done before initiating the action. For this method to be successful, the executives must be receptive and welcoming to double-checking/authentication.
- Conditional Access (CA): By implementing CA, organizations can ensure that only trusted identities on healthy endpoints can gain temporary access to corporate resources and services as required, instead of default access to all corporate resources without any previous condition check
- Identity Risk Assessment (AD Assessment): With the user’s identity often being center stage in an attack, having the ability to uncover security misconfiguration in real-time, the risk level of identities and performing remediation action is critical.
- Identity Threat Detection and Response (ITDR): As identity-based attacks continue to increase, organizations are looking for ways to detect and respond to these types of attacks, and with that, ITDR technology is important.
- Endpoint Detection and Response (EDR): As the majority of cyber-attacks are happening on the endpoint, and this remains true even in the context of social engineering, having the ability to detect and automatically or with a 1-click response to these threats is critical and with that EDR technology is also essential.
Conclusion
Social engineering is a serious threat to consumers and enterprises worldwide. By increasing our awareness of these attacks, having robust procedures in place, and the right tools, as defenders, we have the opportunity to reduce the exposure risk to these attacks significantly.
如有侵权请联系:admin#unsafe.sh