The time is ripe to consolidate and simplify your security toolsets.
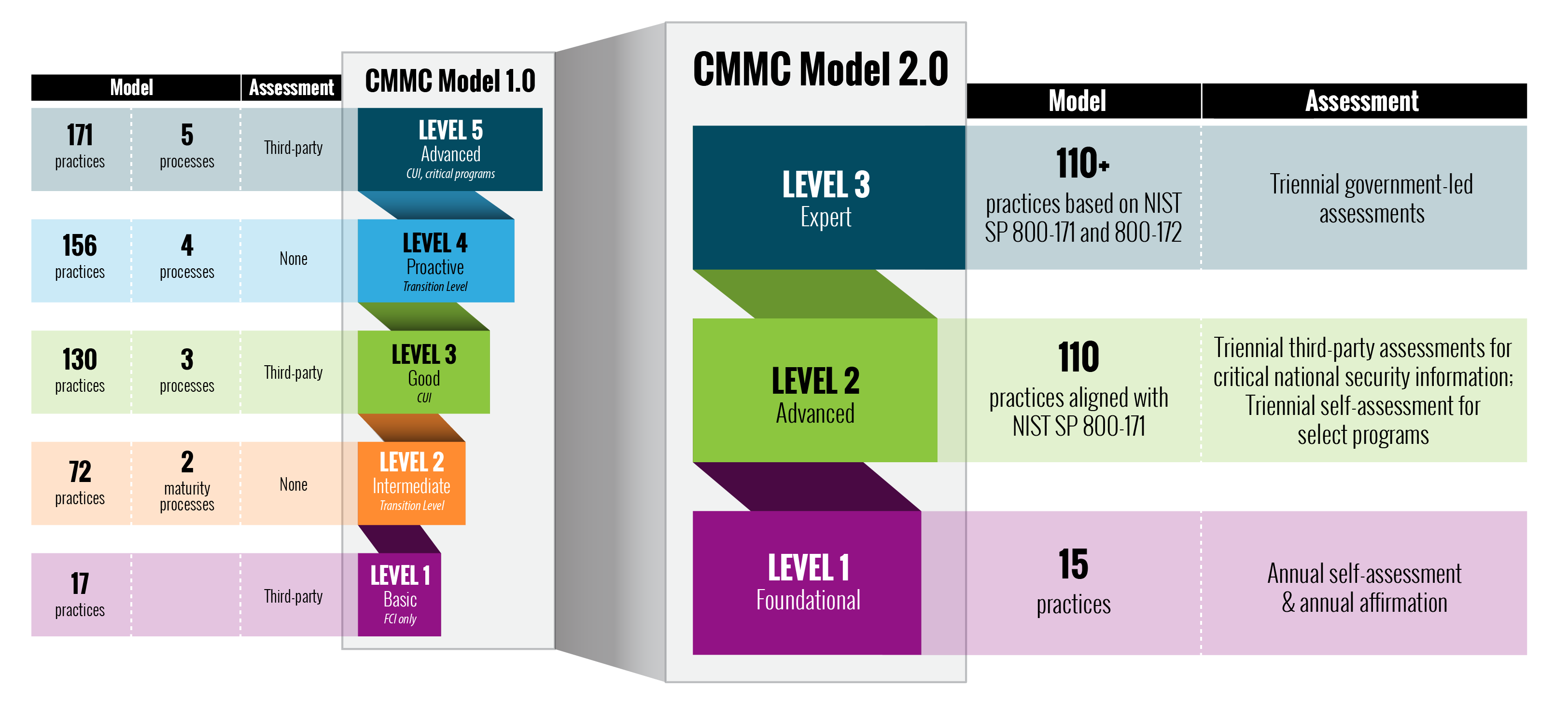
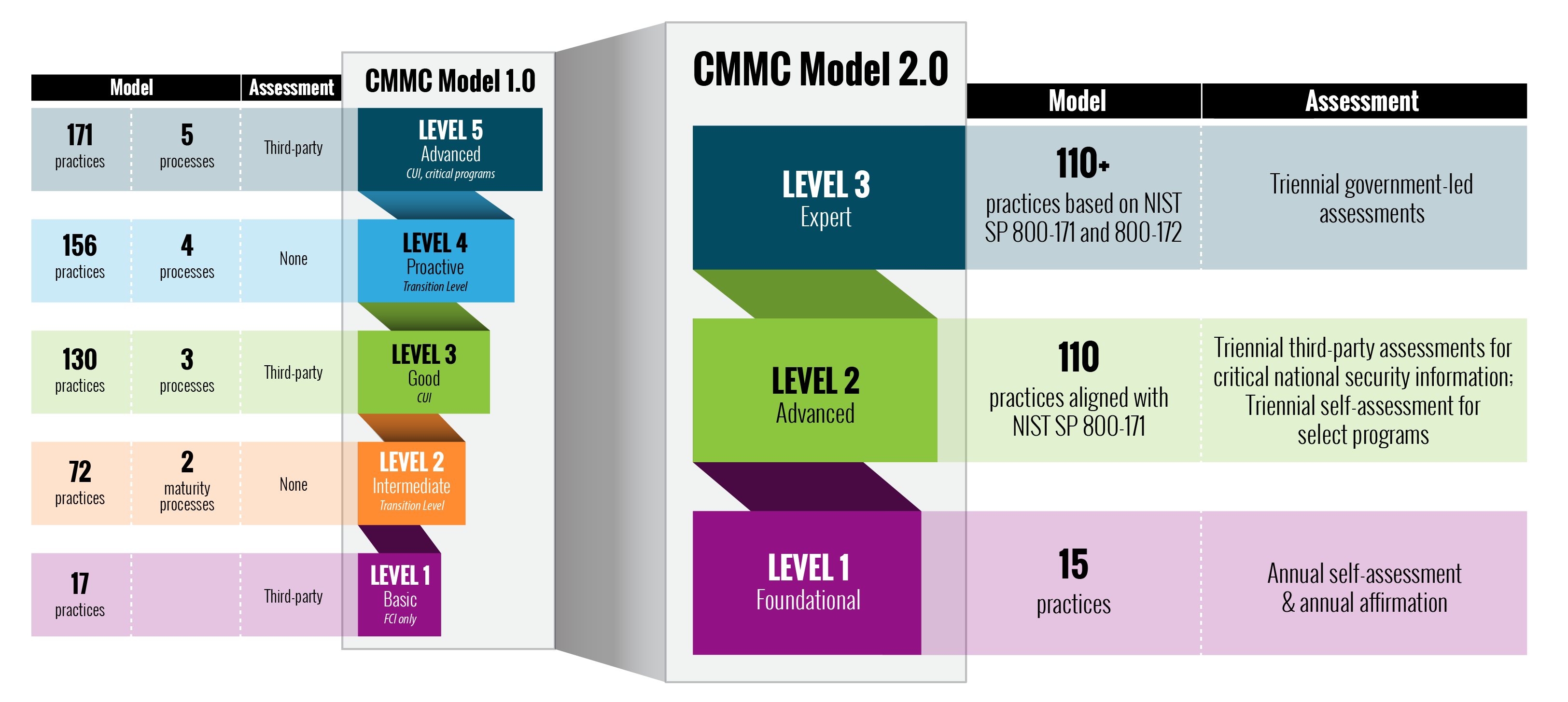
A July 2022 survey of 300 U.S. Department of Defense (DoD) IT contractors shows a woeful lack of information security in the majority of situations. These contractors are part of the DoD’s supply chain that, in typical government speak, is labeled the Defense Industrial Base (DIB). The report should be a warning even for those technology contractors that don’t do any DoD work. A recent attack called STEEP#MAVERICK targeted defense contractors in Europe. One of them was a supplier for one of the US Air Force fighter aircraft programs. The attack was quite sophisticated, containing multiple stages and various obfuscation and defensive measures to avoid detection. This makes the DIB survey more relevant. For example, the survey found that: 80% lack any vulnerability management solution 79% lack a comprehensive multi-factor authentication (MFA) set of policies and procedures to secure their logins 73% lack an endpoint detection and response solution 70% have not deployed any kind of security information and event management Granted, that's a lot of security infrastructure but today’s business — of any kind, government consulting or not — requires these basic tools to be protected from potential attack. The survey found that 82% of the respondents found it “moderately to extremely difficult to understand the governmental regulations on cybersecurity.” While the regulations are complex, there is one element of these regulations that deserves focus, called the Cybersecurity Maturity Model Certification (CMMC). We touched on its introduction a few years ago and suggested that following the CMMC could help to improve overall cybersecurity posture with US-based companies. At the heart of the CMMC is a series of 110 different security controls that are part of a National Institute of Standards and Technology’s document SP 800-171. This recommends requirements for protecting the confidentiality of controlled unclassified information from government suppliers. The requirements are broken down into 14 different categories, such as access controls and configuration management. The document isn’t new — it also has been through one major revision in the past two years — but it is comprehensive. The government suggests that “vendors that want to retain their federal and state agency contracts need to have a plan that meets the requirements of NIST SP 800-171,” and understand the various controls for their IT and operational security. A comparison of the v1 and v2 CMMC rule sets. (Image credit: U.S. Department of Defense) The DoD’s hope is that the CMMC compliance will eventually catch on, and earlier this year they announced that it’s undergoing a major revision to v2, which is supposed to be in place by March 2023. In the meantime, the DoD can provide all sorts of helpful tips on how to implement better cybersecurity practices. Certainly, the time is ripe to consolidate and simplify your security toolsets. And reviewing the CMMC guidelines is also a great way to find your own security weak points.
如有侵权请联系:admin#unsafe.sh