
2022-12-23 22:0:16 Author: www.sentinelone.com(查看原文) 阅读量:17 收藏
The Good
This week, Microsoft joined Google and Meta (aka Facebook) in being the next tech giant to be slapped with a fine by French privacy watchdog CNIL for violation of Europe’s GDPR laws.
CNIL hit Google and Meta with $68 million and $170 million fines respectively earlier this year for failing to offer users of their products transparent ways to reject tracking cookies. On Thursday, Microsoft got a ticking off to the tune of around $64 million for cookies deposited by its web search engine bing.com.

According to an investigation by CNIL, when a user visited bing.com, advertising cookies were placed on their device without user consent. The site also failed to offer a button allowing users to refuse the deposit of cookies as easily as to accept them.
In addition to the fine, CNIL ordered Microsoft to obtain consent for the use of cookies and trackers of any person residing in France within 3 months or face fines of $64,000 per day of delay.
Data privacy laws in the US and Europe have gathered strength over the last few years as the potential dangers of the mass collection of data pertaining to users’ online behavior have become more apparent. While such fines have limited financial impact on giants like Microsoft, Google and Meta, they are a reminder to companies everywhere that data privacy laws have teeth and users’ rights to privacy must be respected.
The Bad
Extortion gang Vice Society, which made a name for itself attacking healthcare and education targets throughout 2021 and 2022 with off-the shelf ransomware like HelloKitty and Zeppelin, has pivoted to a new custom-branded ransomware researchers have dubbed PolyVice.
SentinelLabs revealed this week that the Vice Society group has been deploying payloads that are functionally identical to those of Chily and Sunnyday ransomware. According to their analysis, the payloads only differ in the section where the ransomware campaign details are stored, such as the encrypted file extension, ransom note, hardcoded master key, and wallpaper.
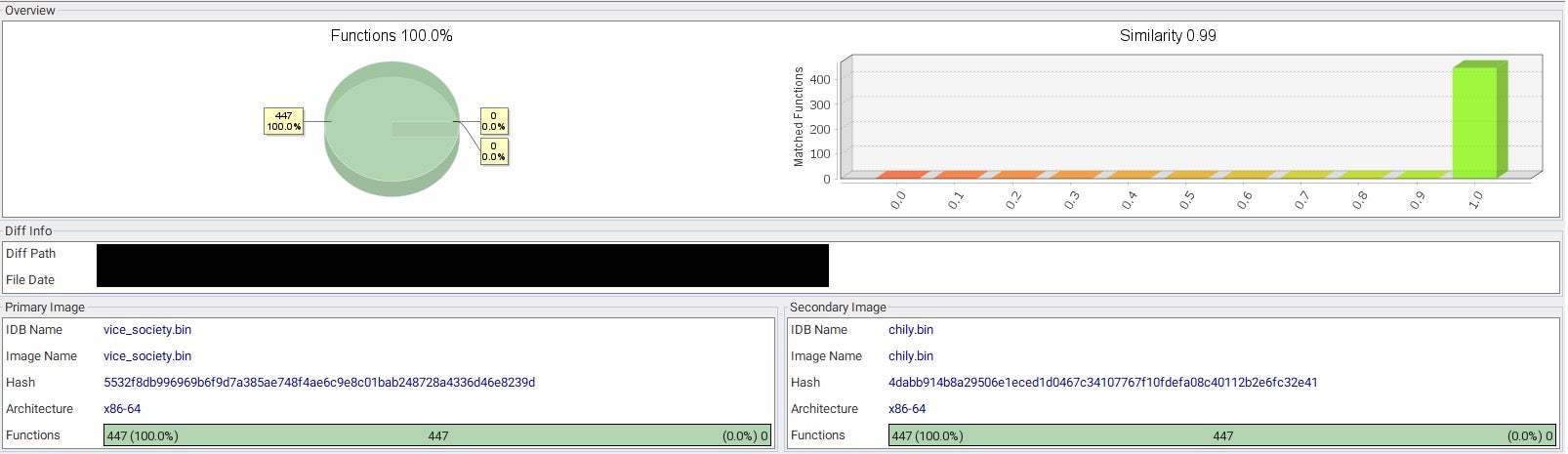
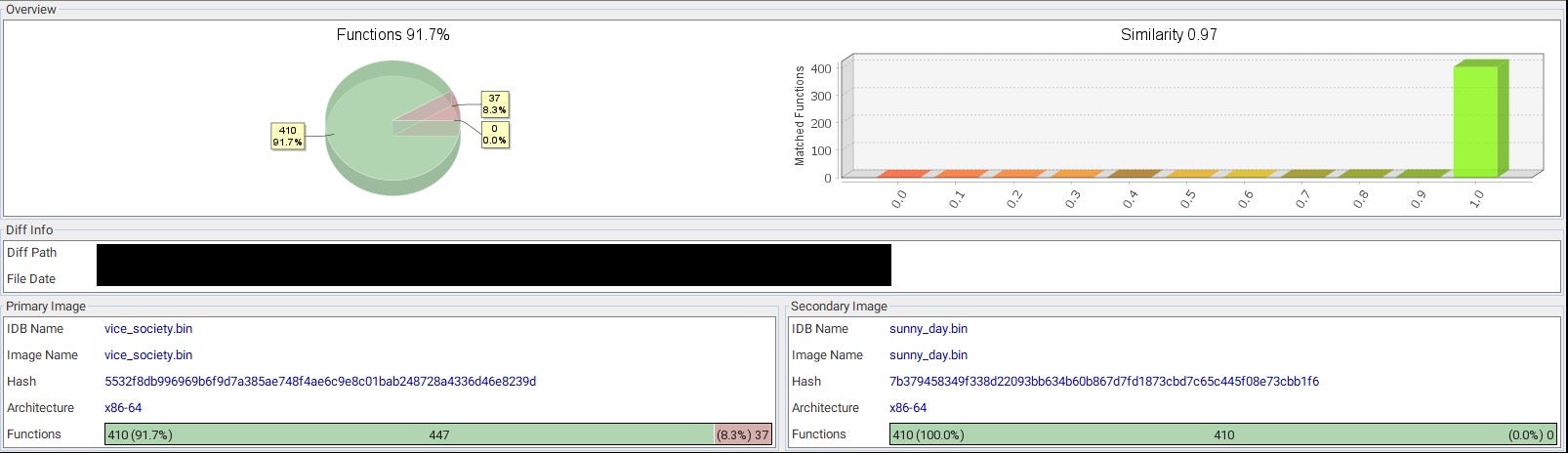
PolyVice ransomware uses sophisticated encryption methods, including partial encryption for large files, and a hybrid encryption scheme that combines asymmetric encryption with the NTRUEncrypt algorithm and symmetric encryption with the ChaCha20-Poly1305 algorithm.
As Vice Society has no known history of developing its own ransomware payloads, the level of sophistication along with the similarities to payloads used by other ransomware groups suggests that an individual or group with expertise in ransomware development is selling custom-branded ransomware payloads to multiple threat actors.
The ability of ransomware groups to outsource development and other services from the larger crimeware ecosystem means that new threat actor groups need little more than initial funding and some basic management capabilities to get new campaigns under way. Expect to see a proliferation of low-skilled crimeware operators picking off more schools, healthcare organizations, and others without adequate defences as we move into 2023.
The Ugly
It’s been a tough year for password manager developer LastPass, as the fallout from a breach that began back in August continued to cause worries this week to the company and its customers.
The breach earlier in the year, LastPass initially said, had been limited to a small part of the LastPass development environment and the theft of some source code and proprietary LastPass technical information. A further breach in late November leveraged data stolen in August and saw “unusual activity within a third-party cloud storage service” that allowed an unknown actor to gain access to “elements of [LastPass] customers’ information”.
This week, the company updated its advisory revealing that the threat actor had made off with “basic customer account information and related metadata including company names, end-user names, billing addresses, email addresses, telephone numbers, and the IP addresses from which customers were accessing the LastPass service.”
The company was at pains to point out that LastPass customer vaults remain unaffected as LastPass does not hold copies of customers’ master passwords and vaults are encrypted with 256-bit encryption. However, LastPass users may be subject to phishing attempts and those who did not follow recommendations for creating a strong password could be susceptible to brute force attacks.
Despite the serious nature of this breach, users everywhere are reminded that password managers are an essential part of good password security.
Pour one out for all of the security practitioners who are going to have to patiently explain that using a password manager is still good, actually, to people who have glanced at a headline about the latest LastPass breach.
— Eva (@evacide) December 23, 2022
如有侵权请联系:admin#unsafe.sh