2023-1-16 16:29:49 Author: perception-point.io(查看原文) 阅读量:13 收藏
Support help desks & ticketing platforms can be companies’ biggest security vulnerability
Customer support and help desk agents are often viewed as prime targets by threat actors. Having access to sensitive information like clients’ financial records and proprietary business data combined with their 24/7 availability for external inquiries make these employees a lucrative payday for cybercriminals. Thus, threat actors have learned to utilize companies’ support channels, available to any online user such as forms, chats, email, and the like in targeted campaigns against businesses.. Posing as legitimate customers submitting an assistance request, attackers employ sophisticated social engineering tactics to try and trick the agents into taking the bait. These techniques range from malware disguised in legitimate documents to tailor-made phishing pages that lead to fake invoices.
The same is true for organizations that use third-party ticketing systems to manage their customers’ support requests. These platforms are just another channel by which attackers attempt to breach organizations’ networks.
Behind the Desk: An Intro to Zendesk
Zendesk is among the leading customer support SaaS solutions in the market today. More than 100,000 brands and organizations use Zendesk’s ticketing platform for help desk services and for support agents to manage customer inquiries, complaints, and feedback.
While Zendesk’s platform offers a wide variety of support channels for customer communication, the agents’ workflow on the platform is straightforward: ny incoming traffic to the following channels becomes a ticket in the system, requiring an agent’s attention:
- Email – incoming emails to dedicated addresses
- Help center “contact forms” – a simple web form
- Social media integrations – Facebook, Twitter, WhatsApp and more
- Web widget – a widget for embedding live chat in a website – creating a communication flow via chat bot
- Mobile SDKs – work similarly to Web Widget but is meant for embedding the chat in mobile apps (android or IOS)
- Zendesk API – a designated API used for custom support channels
It is important to note that all of the above channels also allow external users to attach files to their requests, which the agent engages with when handling the tickets.

Better late than never? Zendesk unveils malware scanning service for tickets
In an effort to mitigate the emerging threat to customer support channels, in June of 2022 Zendesk announced their native scanning service for attachments in tickets. They have partnered with an unnamed malware detection vendor to scan incoming files for malicious content.
No further information has been disclosed about the technology used nor the types of threats they intend to eliminate with this newly available security tool.

Static detection & stats for security leaders’ attention
Although the security vendor provided with Zendesk is undisclosed, the detection technology used is far from a mystery. Based on extensive experience protecting global enterprises’ Zendesk channels from malicious files, security researchers at Perception Point have deduced Zendesk’s native security solution offers only static detection against common threats.
A static scanning or signature-based detection is a method of identifying malware and other threats (e.g. phishing HTML files) by searching for known patterns or characteristics that define the content as a threat.
Although very common, on its own this method proves ineffective against advanced or evasive threats. One major reason for this is that static scanning can only detect known, “everyday” threats, and cannot identify new or previously unseen attacks. This means that if a new strain of malware is released, it will not be detected until a new signature for it is created and added to the database.
Deployed via an API integration, Perception Point’s Advanced Threat Protection for Zendesk is positioned “under” (after) Zendesk’s scanning tool in a way that allows you to see what ticket attachments they catch and how many threats manage to bypass their defenses, and then intercepted by Perception Point.
Below are the key findings from comparing the attachments we intercepted to files detected by Zendesk:
- Zendesk failed to detect ANY of the advanced threats caught via Perception Point’s dynamic detection layer
- All malware or phishing attacks that Zendesk’s native scanning caught were detected by Perception Point static engines or threat intelligence layer.
- Zendesk’s detection rate of known malware attacks was below 40%*
- Zendesk’s detection rate of phishing attacks was below 5%* (= all known HTML files)
- Simple “obfuscation” techniques like hiding a known malware inside an archive file evades Zendesk’s security (Zendesk may still be able to catch the same file if sent as is and not archived)
*The false-negative rates were measured during a 21-day threat analysis research across 3 of Perception Point’s enterprise customers using Advanced Threat Protection for Zendesk.
One-way “ticket” to Ransomland? Examples of malicious attacks missed by Zendesk native security
The examples below are malicious attacks that managed to bypass Zendesk’s native scanning service, and were caught by Perception Point’s advanced threat detection platform.
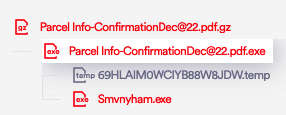
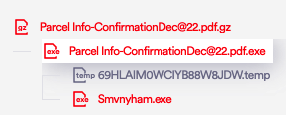
Example #1 – Malware Campaign – “Parcel Info Confirmation”
Delivery method: .gz archive -> .exe file
An archive containing an executable – a malware from the “Mars Stealer” family. This is a known threat with advanced stealing capabilities that target users’ 2FA plugins and cryptocurrency assets by collecting passwords, cookies, browser data, downloads history and more. A simple double-click on the .exe file is enough for the malware to be distributed and infect the agent’s computer.
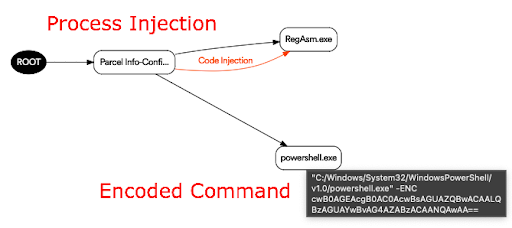
Perception Point’s multi-layered defense incriminated the attack using a combination of static and dynamic code analysis and removed the malicious attachment from the agent’s workspace within seconds.
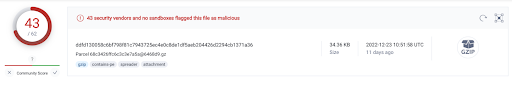
Some static solutions do detect this malicious attachment, but Zendesk failed to catch it.
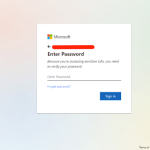
Example #2 – Phishing Campaign 1 – “SharePoint Impersonation”
Delivery method: HTML file – SharePoint login page
A spoofed SharePoint page inside an HTML file attachment was shared via a ticket. Once clicked, the SharePoint page redirects the user to a Microsoft look-alike login page with the corporate email address of the agent already injected as the username.
Using image analysis and ML engines, Perception Point’s anti-phishing layer was able to immediately identify the phish setup and prevent credential theft.
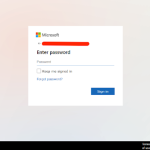
Example #3 – Phishing Campaign 2 – Zendesk Ticket Attachment “Microsoft Impersonation”
Delivery method: SHTML file (html alternative) –Microsoft login page
Both of the cited phishing campaigns utilize the same techniques, luring the agents into clicking on the attachment, type in their credentials and access the document which they believe is relevant to their jobs. Stolen credentials harvested this way can be used by threat actors for consecutive Account Takeover (ATO) attempts, stealing corporate data, selling the passwords online or even blackmailing the agents.
Protect your agents, company, and customers with Perception Point’s Zendesk Security Solution
Perception Point’s Zendesk Security Solution, Zendesk Advanced Threat Protection, dynamically scans in near-real-time, all attachments uploaded or shared to your agents’ Zendesk’s environments from any of the available support channels, to intercept malicious content before it impacts your business.
Perception Point’s Zendesk Advanced Threat Protection offers unprecedented protection against all types of content-borne attacks including APTs, zero-days, malware and phishing that can penetrate organizations through Zendesk.
The SaaS solution seamlessly integrates with your Zendesk environment in just a few clicks to scan every piece of content (including embedded files and URLs) through its multi-layered platform, dynamically scanning 100% of the attachments in near real-time in both Windows and Mac environments, up to 40x faster than other solutions.
Perception Point does not just provide you with a product. Every customer receives a 24/7, free-of-charge Integrated Incident Response service that efficiently analyzes, manages and remediates incidents, and drives continuous optimization of the security solution.
To learn more about Perception Point’s Zendesk security solution, download the Zendesk Advanced Threat Protection brochure.
如有侵权请联系:admin#unsafe.sh