Vulnerabilities within WordPress can lead to compromise, and oftentimes known vulnerabilities are utilized to infect WordPress sites with more than one infection. It is common for out of date websites to be attacked by multiple threat actors or targeted by the same attacker using multiple different channels.
We recently came across a database injection that has two different pieces of malware accomplishing two unrelated goals. The first injection redirects users to a spammy sports website and the second injection boosts authority of a spammy casino website within search engines.
So far, roughly 270 sites have been impacted by the first injection, while 82 sites have been impacted by the second. Both pieces of malware can be found scattered throughout a WordPress database but they each accomplish different tasks.
Let’s look at the two injections.
Database Redirect & Casino Site Authority Boosting
The first injection can be found sprinkled throughout a WordPress database:
<meta http-equiv="Refresh" content="60; URL=hxxp://redirect4[.]xyz/">
Let’s review what this injection is doing.
The domain found on the first line is not the final destination of the attack, it simply performs the heavy lifting of the redirect. First, the browser is instructed to wait 60 seconds, then a redirect occurs to the domain hxxp://redirect4[.]xyz. Then, the unknowing user is redirected again and lands on the following spam domain after the first redirect completes:
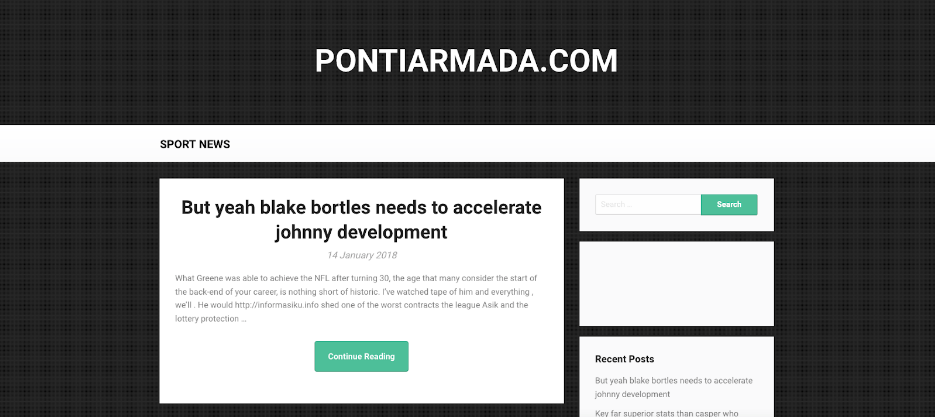
hxxp://pontiarmada[.]com
The spam site hxxp://pontiarmada[.]com has injected iframes to disseminate malware to unknowing visitors.
The second injection can also be found sprinkled throughout the WordPress database:
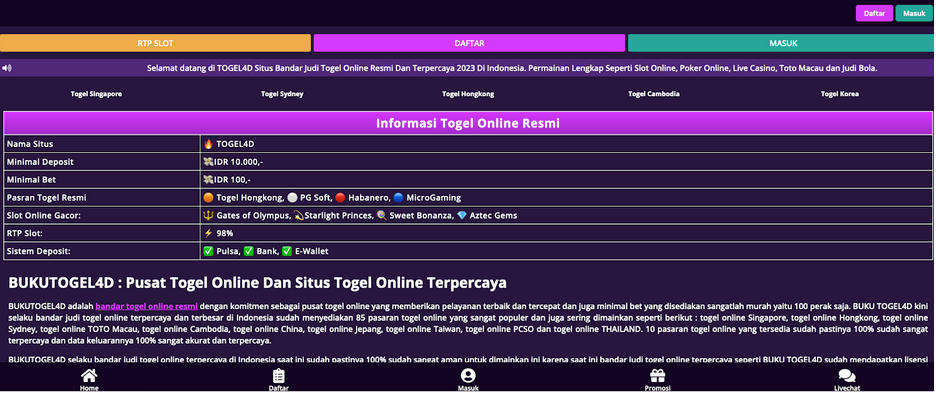
<style type="text/css"> dofollow { display: none; } </style> <dofollow><a href="hxxp://nomortogelku[.]xyz/" rel="external" alt="nomortogelku" title="nomortogelku">nomortogelku[.]xyz</a> <a href="http://207[.]106[.]22[.]48/" rel="external" alt="Nomor Togel Hari Ini" title="Nomor Togel Hari Ini">Nomor Togel Hari Ini</a></dofollow>
Let’s discuss what this database injection is doing.
The domain hxxp://nomortogelku[.]xyz is a gambling casino site using a common method to boost its authority in search engines. The black hat SEO tactic this attacker used places an invisible link throughout the compromised website to increase its domain authority and appear more legitimate.
Both of these injections are found scattered throughout WordPress databases, oftentimes found in the posts table. Below is the site:
One characteristic both injections have in common is the domain extension used, .xyz. The .xyz domain extension is commonly used by attackers and the number of malicious domains using this extension increases everyday. Threat actors cycle through domains often — and domains with the .xyz extension tend to be cheap for the first year, which is a leading theory as to why this extension is widely used.
These two infections found on the same site provide an example of how threat actors can disseminate different types of malware through the same site, or how different attackers can take advantage of the same vulnerability to infect the same WordPress site.
Two Infections for the Price of One
WordPress sites are often taken advantage of by threat actors when a vulnerability is present or an admin user is compromised. Once an attacker gains access to a website they can easily disseminate malware, and oftentimes they use their leverage to distribute malware through multiple channels.
Many threat actors even monetize the same vulnerable website with different types of malware to take full advantage of their access. As a result, it is not uncommon to find a variety of malware on the same infected website.
Different Actors, Same Vulnerability
Vulnerable WordPress plugins and themes are one of the leading causes of infection and reinfection. When these vulnerabilities are present, multiple different threat actors may take advantage and spread their malware to unpatched sites.
It can be common to see different infections on the same site from different attackers, especially when a website is impacted by a high-grade and common vulnerability, like a vulnerability on a popular plugin downloaded by thousands of users.
Mitigation Steps
Taking advantage of a vulnerable WordPress site by injecting different types of malware is a common tactic used by attackers. Infections can harm a website’s credibility and disrupt high SEO rankings.
Keep your WordPress website safe by following these mitigation strategies:
- Keep your plugins, themes, and website software up-to-date. Enabling auto-updates is a great way to patch vulnerabilities as soon as a fix comes out.
- Get a web application firewall (WAF). Our firewall can help block attacks caused by vulnerabilities. While the firewall provides an extra layer of protection for a vulnerable WordPress website, it is still recommended to keep software up-to-date.
- Create secure passwords for all your accounts. Credentials for WordPress admin users, FTP accounts, cPanel, and server users need to be long and secure.
- Keep the WordPress admin user count low. Only have admin accounts when absolutely necessary, and set appropriate user roles for all other users.
- Enable 2FA to secure your wp-admin area from unauthorized access or protect the dashboard through the protected page on our firewall.
And if you believe your site has been compromised or injected with malicious scripts, we can help! Reach out to our support team for assistance and we can get the malware cleaned up for you.