During the past 4 months Microsoft Onenote file format has been (ab)used as Malware carrier by different criminal groups. While the main infection vector is still on eMail side – so nothing really relevant to write on – the used techniques, the templates and the implemented code to inoculate Malware changed a lot. So it would be interesting to study this new phenomenon for further attribution and for quick identifications.
Aim of this post is to highlights the main used techniques to inject Malware into Microsoft Onenote file format and to attribute them to specific Malware families.
NB: This post represents personal notes on how actors are abusing Microsoft Onenote file. You will not find complete Malware analyses or reverse engineering path since it’s not my current goal.
Async RAT
The very first Malware seen abusing Microsoft Onenote file format was AsyncRAT. Async RAT is using a VBScript embedded into the .one file format next to images (PNG) and random scripts as well to start its infection chain. The VBscript executes the AutoOpen function which eventually runs the following main routine:
Function WmiExec(cmdLine )
Dim objConfig
Dim objProcess
Set objWMIService = GetObject("winmgmts:\\.\root\cimv2")
Set objStartup = objWMIService.Get("Win32_ProcessStartup")
Set objConfig = objStartup.SpawnInstance_
objConfig.ShowWindow = 0
Set objProcess = GetObject("winmgmts:\\.\root\cimv2:Win32_Process")
WmiExec = dukpatek(objProcess, objConfig, cmdLine)
End Function Interesting to report the following function: the ExecuteAsync function from which it takes its name:
Sub ExecuteCmdAsync(targetPath )
On Error Resume Next
Err.Clear
wimResult = WmiExec(targetPath)
If Err.Number <> 0 Or wimResult <> 0 Then
Err.Clear
WscriptExec targetPath
End If
On Error Goto 0
End Sub
The chosen command to drop and execute the desired RAT is a powershell Invoke-WebRequest from a specific URI. The following images shows the complete core execution function included into the carrier file format. I find remarkable the similarity with classic Microsoft Office Macros pattern here. It looks like a developer who desired to reuse many skill from classic Office Droppers.

Remcos
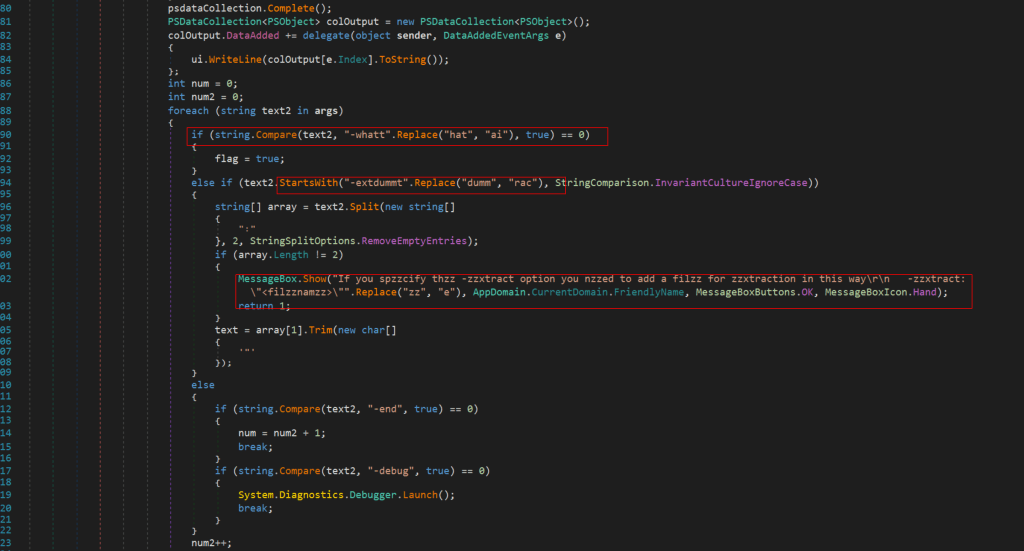
One of the most interesting samples seen to abuse Microsoft onenote file format, at least so far, was the Remcos implant. It directly embeds a .NET dropper which carries (potentially) many infection vectors. The main function parses for input characters and eventually adds delays or dumps codes. The following image shows how the main function would run once executed.
While is not my intent to perform a complete Remcos analysis, it’s remarkable the way the Malware writer uses string.compare and string.replace to evade classic pattern matching signatures. Check the red boxes to the following image to see what I meant.

The second stage is directly dropped from an encoded string and run on memory. The following image shows the used pattern to decode and execute the news payload. Many tools are available to decode this junk but you might just introduce some writeline on the code to monitor the variable change.

Decoding the base64 string would show the clear-text code from where we might appreciate a nice and plain drop-and-execute payload. Finally we see the dropping url (in this case canon.buytoprint.com) and the romantic execution by reflection as in the best Remcos tradition.

The multi stage delivered payloads are very interesting and complex in its rounds, it looks like to be the result of a multi-layered “Remcos Builder” in where attackers added the new functionality to be injected into Onenote file.
Quakbot
Quakbot presents itself as an embedded HTML page within both javascript and VBscript functions into the Onenote file format. The qbot or Quakbot sample sees a <div> section within encoded parameters to a given dropped and downloaded WScript code. In this case the encoded parameter is stored on the local key hkcu\\Software\Firm\Soft\Name.
Javascript is used to extract section (id=content) from DOM, to drop and execute a specific WShell script (in this scenario from 45.155.37.124) while VBscript is used to interact with Windows Register.

Quite interesting to see its fingerprint and to see the implementation in two scripting languages in where the second one is only used for simple tasks. In my personal point of view it looks like to be the result of multiple developers who never spoke to themselves 😀 (LOL).
Redline
Redline Malware presents itself in a very original way if compared to previous ones. It looks like a botnet (it really reminds me, in this specific form, the way Mirai spreads itself) indeed it includes into Onenote file format many single VBScripts running simple powershell commands. Into every script you would find many indicators (droppping urls): only one is needed to be up-and-running for begin the infection chain. The following image shows how it behaves: from a dropping url it drops a “real onenote file” (for example Invocice.one) which runs first. After the documents run it loads from a second url a powershell file running the Redline infection chain.

The analyzed sample implements an impressing obfuscated payloads as seen in the bottom of the previous image. It uses a substitution variable plus some junk base64 encoded piece of code to make the analysis long and boring. Once the payload is run the following command line is invoked and the Redline info stealer begins its journey.
It looks that a very similar sample was previously analyzed by Rapid7 in its report here.
Redline is the only sample which wants to lure the victim by giving to him a fake “real” document acting like a Trojan (even not really), one more interesting characteristics to be recorded.

Conclusion
From this quick blog post we should takeaway the following principles:
1. Microsoft Onenote file format could become a new Malware carrier
2. So far Recmos, AsyncRat, Quakbot and Redline are the main Malware seen abusing this file format
3. AsyncRat implements a ported version of VBA Macron seen in Microsoft World Documents
4. Remcos is the most complex chain seen so far in Microsoft Onenote files and it includes PE Files directly on the carrier
5. Quakbot uses both scripts: Javascript and VBscripts. It uses VBScripts just for Microsoft Windows Registry
6. Redline uses simple launching schema as romantic botnet and implements a particularly obfuscated and encoded powershell second stage. It is the only one to lure the victims by onpening a “real” Onenote file before running the stealer.
Classified Samples
- Sha256: 482a4763c8cf9c448fc851e6fe4554cc48abc563c49847ed040cdaee8a12003c (Async Rat)
- Sha256: b45ace5a35914dcd4beb7486f3ddad4bbd84be245d403b9e6a3f1b907aa4ae03 (Quakbot)
- Sha256: b13c979dae8236f1e7f322712b774cedb05850c989fc08312a348e2385ed1b21 (Remcos)
- Sha256: eb674dc2e3787de0948e0af5a50aa365b21eb2dd40c0ef9034e44ed1c46b11d1 (Redline)
Involved IoC
NB: following involved IoC found, not necessary malicious but involved in the found infection chains
hash256: a870d31caea7f6925f41b581b98c35b162738034d5d86c0c27c5a8d78404e860
hash256: 00000f6dc506c0893973cde12e43be88be103b7f07c3f1f12dc97f4d157e29f8
hash256: bbc994d3a91480e58678eea6c15baf8ceb136b8ad1493d38715e9d8a24921a43
hash256: 215c5b5c3b1ae20b73798732cd53039b6cf867e044e3e1ceba49191634434439
hash256: 78632bbb0a21acb272a6238c54434b3df1e89bf95104a2ea6f0a7c880acf0d13
hash256: 892e637a6c3909097d99972b8210947f4a228c49b9ad88ff802ce94f3c10b3cd
hash256: 1fc609cb8e092b587826b300535cea12be24960dfa6ebab11c2104736cc3bd8e
hash256: b45ace5a35914dcd4beb7486f3ddad4bbd84be245d403b9e6a3f1b907aa4ae03
hash256: 91da7c5ea5ab92ac99bb4e4c7da27fd840868c533eeee7804f3ed85394faa012
hash256: bf8c7c35cb5b8f47ad7fe7e89322960e105efa754360953ca854925a6b914092
hash256: 58fd23e02ba5d6ae4b6662f427c047d62ed34eafc4e547aa62f059313de75397
hash256: 323ceb872e5f0256281968b5a2a3142986f2938a44b18f0d3d23ff2b1c9287a3
hash256: 046a0333f2957ca268168775b23ad4c467c7e76744887cc52f6aedd377888a95
hash256: db53c5052be26fbe49e0430fc1d60ab602d87918cad8dd7892974316c3eff0be
hash256: bd040a74f99bd767652abc940a4939361d214ba6407781724fde55e48fa7aecf
hash256: 002fe00bc429877ee2a786a1d40b80250fd66e341729c5718fc66f759387c88c
hash256: 319db59d8a4addfd6956413af7da48b33cd355cbeb9ca90a191ddf57f45e681d
hash256: 0d781feece557451c861cf2b6eff3e121d7aaac9b156f17ae10d20702a1f962d
hash256: 5aa30c40e7c57ad818881e70c431fc3e0477a7193ee33ad0ed53df89d5dc172d
hash256: 495e5b52716772099ac02c9476feabdd7d51856951d5e61f381c7016f90bb247
hash256: 76ac1e659958f6a0ccecf6031c47a762787abb31a00a0807634437f1f79a1992
hash256: 12f21e8b7d02f5f48dc6966ec41307f810ef92bf02f9fce4872839153081dd9c
hash256: 4b30e6ff64e1c2e8c1730778143489a6634c34705bdd2e5effa3e57cddf52907
hash256: b9080762697def380660f61a5f9dcdf0cce6aa4c62139f154cbbfefa18626930
hash256: 186d2972106079c8bf0c9e9000a15056161602dba947d0f85bc7141ef2066d5a
hash256: bf8c7c35cb5b8f47ad7fe7e89322960e105efa754360953ca854925a6b914092
hash256: bd040a74f99bd767652abc940a4939361d214ba6407781724fde55e48fa7aecf
hash256: b9080762697def380660f61a5f9dcdf0cce6aa4c62139f154cbbfefa18626930
hash256: a870d31caea7f6925f41b581b98c35b162738034d5d86c0c27c5a8d78404e860
hash256: 1fc609cb8e092b587826b300535cea12be24960dfa6ebab11c2104736cc3bd8e
hash256: a870d31caea7f6925f41b581b98c35b162738034d5d86c0c27c5a8d78404e860
hash256: 186d2972106079c8bf0c9e9000a15056161602dba947d0f85bc7141ef2066d5a
hash256: 76ac1e659958f6a0ccecf6031c47a762787abb31a00a0807634437f1f79a1992
hash256: 892e637a6c3909097d99972b8210947f4a228c49b9ad88ff802ce94f3c10b3cd
hash256: 1fc609cb8e092b587826b300535cea12be24960dfa6ebab11c2104736cc3bd8e
hash256: 319db59d8a4addfd6956413af7da48b33cd355cbeb9ca90a191ddf57f45e681d
hash256: 319db59d8a4addfd6956413af7da48b33cd355cbeb9ca90a191ddf57f45e681d
hash256: 5aa30c40e7c57ad818881e70c431fc3e0477a7193ee33ad0ed53df89d5dc172d
hash256: 91da7c5ea5ab92ac99bb4e4c7da27fd840868c533eeee7804f3ed85394faa012
hash256: 319db59d8a4addfd6956413af7da48b33cd355cbeb9ca90a191ddf57f45e681d
hash256: 4b30e6ff64e1c2e8c1730778143489a6634c34705bdd2e5effa3e57cddf52907
hash256: bd040a74f99bd767652abc940a4939361d214ba6407781724fde55e48fa7aecf
hash256: a870d31caea7f6925f41b581b98c35b162738034d5d86c0c27c5a8d78404e860
hash256: 4b30e6ff64e1c2e8c1730778143489a6634c34705bdd2e5effa3e57cddf52907
hash256: b9080762697def380660f61a5f9dcdf0cce6aa4c62139f154cbbfefa18626930
hash256: 186d2972106079c8bf0c9e9000a15056161602dba947d0f85bc7141ef2066d5a
hash256: 495e5b52716772099ac02c9476feabdd7d51856951d5e61f381c7016f90bb247
hash256: 76ac1e659958f6a0ccecf6031c47a762787abb31a00a0807634437f1f79a1992
hash256: 002fe00bc429877ee2a786a1d40b80250fd66e341729c5718fc66f759387c88c
hash256: 892e637a6c3909097d99972b8210947f4a228c49b9ad88ff802ce94f3c10b3cd
hash256: 12f21e8b7d02f5f48dc6966ec41307f810ef92bf02f9fce4872839153081dd9c
hash256: b45ace5a35914dcd4beb7486f3ddad4bbd84be245d403b9e6a3f1b907aa4ae03
hash256: 1fc609cb8e092b587826b300535cea12be24960dfa6ebab11c2104736cc3bd8e
hash256: 91da7c5ea5ab92ac99bb4e4c7da27fd840868c533eeee7804f3ed85394faa012
hash256: 319db59d8a4addfd6956413af7da48b33cd355cbeb9ca90a191ddf57f45e681dURL://139[.]99[.]117[.]17/39444[.]dat
URL://95[.]179[.]215[.]225/64715[.]dat
URL://139[.]99[.]117[.]17/51352[.]dat
URL://139[.]99[.]117[.]17/29243[.]dat
URL://139[.]99[.]117[.]17/13056[.]dat
URL://141[.]164[.]35[.]94/70136[.]dat
URL://49[.]50[.]84[.]121/71446[.]dat
URL://45[.]155[.]37[.]124/14449[.]dat
URL://transfer[.]sh/get/5ji4Ye/tp[.]bat
URL://www[.]onenotegem[.]com/uploads/soft/one-templates/four-quadra
URL://transfer[.]sh/get/5ji4Ye/tp[.]bat
URL://transfer[.]sh/get/DVKz31/AsyncClient%20NEW[.]bat
URL://transfer[.]sh/get/DdAbds/window[.]bat
URL://transfer[.]sh/get/44Y2u7/gh[.]ps1
URL://energizett[.]com/1llNOC1/300123[.]gif
URL://rmbonlineshop[.]com/VV71d8/300123[.]gif
URL://khatriassociates[.]com/MBt/3[.]gif
URL://somonoo[.]com/6WB/i[.]gif
URL://finetuning-digital[.]com/wRuLe/01[.]gif
URL://spincotech[.]com/8CoBExd/3[.]gif
URL://135[.]148[.]144[.]191/44607[.]dat
URL://unitedmedicalspecialties[.]com/T1Gpp/OI[.]png
URL://khatriassociates[.]com/MBt/3[.]gif