We wanted to bring to your attention a significant ransomware threat recently reported in the cybersecurity community by French national government computer security incident response team (CERT-FR). The ransomware attack campaign targeting the vulnerabilities in VMware’s ESXi and Cloud Foundation systems, identified by CVE identifier CVE-2021-21974.
These attacks are taking advantage of the vulnerability of ESXi hypervisors that haven’t been updated with security patches quickly enough, with the SLP service being a particular target due to known vulnerabilities (CVE-2020-3992 and CVE-2021-21974). The systems currently targeted are ESXi hypervisors in version 6.x and before 6.7. The CERT-FR confirms that virtual machine disks can be recovered if the .vmdk files are encrypted and renamed with a .args extension.
The attack results from a heap-overflow vulnerability in OpenSLP, which is used in VMware ESXi versions 7.0 before ESXi70U1c-17325551, 6.7 before ESXi670-202102401-SG, and 6.5 before ESXi650-202102101-SG.
Attackers who have access to port 427 on the same network segment as ESXi may be able to trigger the heap-overflow issue and execute remote code, potentially leading to a ransomware attack. This could result in remote code execution. The vulnerability was confirmed and weaponized, being used by the ransomware family ESXiArgs, on February 3, 2023. The vulnerability’s Proof of Concept (PoC) was published on February 24, 2021.
The Common Weakness Enumeration (CWE) categories related to the vulnerability include:
- Buffer overflow.
- Incorrect calculation of buffer size.
- Buffer access with incorrect length value.
The vulnerability has been assigned a high severity score by CVSSv3 (8.8) and is considered one of the top 25 most dangerous software errors (CWE Top 25).
Qualys QID Coverage
Qualys has released four (4) QID on 2021-02-25 to cover these vulnerabilities, starting with IP scanning version VULNSIGS-2.5.133-2.
| QID | Title |
|---|---|
| 216258 | VMware ESXi 6.5 Patch Release ESXi650-202102101-SG Missing (VMSA-2021-0002) |
| 216257 | VMware ESXi 6.7 Patch Release ESXi670-202102401-SG Missing (VMSA-2021-0002) |
| 216256 | VMware ESXi 7.0 Patch Release ESXi70U1c-17325551 Missing (VMSA-2021-0002) |
| 11699 | VMware vCenter Server Remote Code Execution Vulnerability (VMSA-2021-0002) |
Discover Vulnerable VMware’s ESXi Using Qualys VMDR
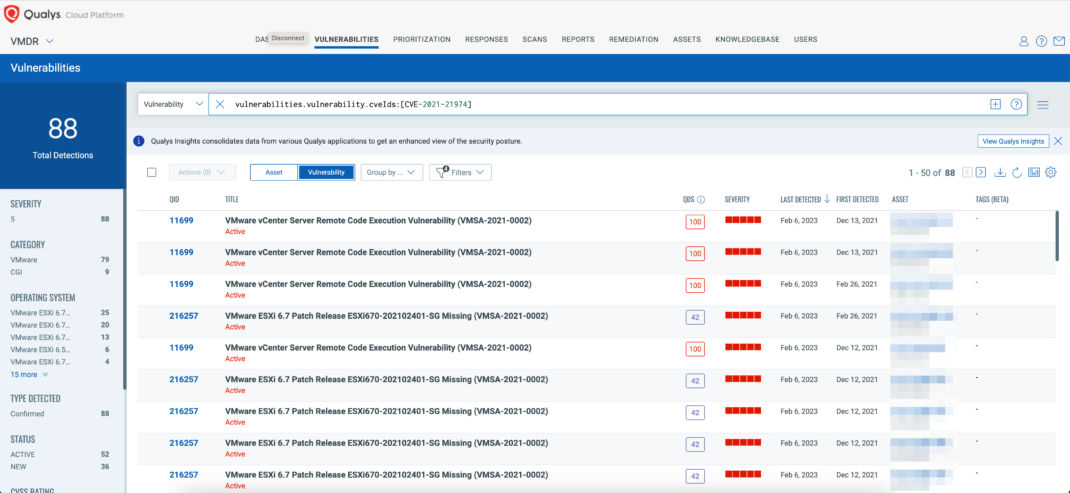
You can see all your impacted hosts for this vulnerability in the vulnerabilities view by using QQL query
vulnerabilities.vulnerability.qid:[`216258`,`216257`,`216256`,`11699`]
or
vulnerabilities.vulnerability.cveIds:[CVE-2021-21974]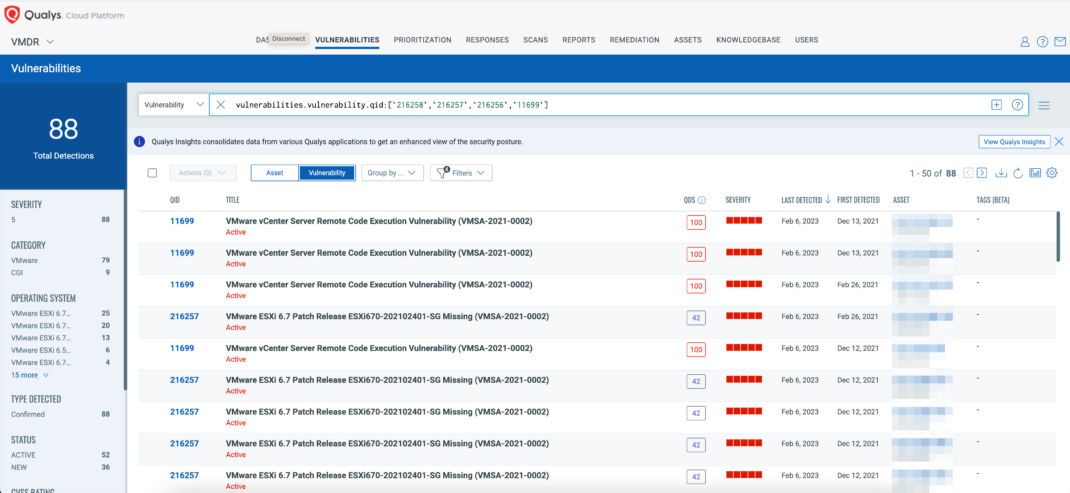
Free Trial
It is strongly recommending that organizations isolate the affected server and conduct an analysis to detect any signs of compromise. A reinstallation of the hypervisor in a version supported by the publisher (ESXi 7.x or ESXi 8.x) is preferred, and security patches should be applied along with the following future vendor security advisories. Additionally, disabling unnecessary services and blocking access to administration services through a firewall is recommended. Updating a product or software should be done with caution, and testing and continuity of service provisions should be in place.
We take the protection of our customers’ systems and data very seriously. We want to remind you of the importance of keeping your systems up-to-date with the latest patches and security updates.