Over the last few days, scammers have been sending out phishing mails that disguise bogus URLs with something called Slinks—shortened Linkedin URLs.
The shortened URLs redirect users to a different URL when they are clicked. If you’ve ever seen a Tiny URL, or a Bit.ly link, you’ll already be familiar with how these work. Shortened links are a common tool in the phishing armoury because they obscure the final destination of their links, and because familiar shortening services may be seen as more trustworthy.
As you would expect, a LinkedIn shortened link is going to carry a certain amount of trust for someone on the receiving end. This has been put to the test a number of times. For example, in February of last year Slinks were being used to send people to IRS and PayPal phishes. As Brian Krebs notes, this tactic has been around for some years and was spotted in 2016 being sent out via Skype spam.
Now they're being used in a scam based on Amazon's popular Prime membership.
Fake Prime email
The email claims to have been sent from “Prime” and has the subject "New Membership Statement : Renewal Prime Membership statement was ended - Your renewal scheduled on February 21, 2023." The text reads:
Due to a problem with your card, we were unable to charge your ac͏count $12.99 and applicable taxes for the next 1 month of Amazon Prime. Your membership benefits are currently on hold. If you not update your card information in the next 24 hours, your membership benefits will be cancelled. To continue enjoy your membership benefits, please update your payment information. We are sorry for any inconvenience this may have caused. Sincerely Prime Team
The email includes an Update Now button. Hovering over it reveals the Slink URL, and hitting it redirects you to a site resembling an Amazon login page.
Some folks may wonder why an Amazon email contains LinkedIn links, but many won't. Some won't notice, and some will assume it's OK, becasue they've been trained that way. Email newsletters and promotions often use shorteners and tracking links. As a result, odd-looking URLs won't necessarily alarm recipients as being unusual.
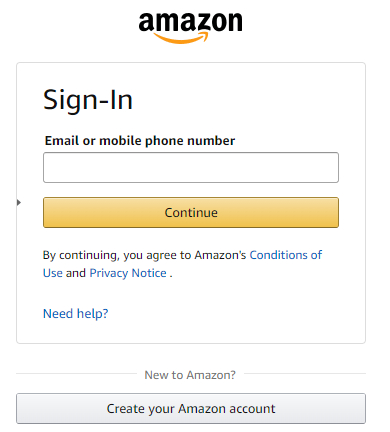
Fake Amazon login
The phishing site asks for an email or phone number tied to an Amazon account.

Next, the site directs you to a tailored password page, using the information you just entered. For example, entering a Gmail address leads to a page asking for the Gmail password. Enter a Microsoft address, and you'll be directed to a Microsoft-centric password request page, and so on.

With these details out of the way, the phishers move on and begin collecting even more personal information. First up, via a “Security Checkup”, the site asks for
- Mother’s maiden name
- Phone number
- Date of birth
Next up:
- Address
- City
- State/province/region
- Zip / postal code
Finally, the site asks for credit / debit card information.
- Cardholder name
- Card number
- Security code
- Expiration date

In terms of damage done, someone filling these sections in and hitting submit has potentially handed over their password, credit card details, and a lot of answers to common security questions.
Not good at all.
How to avoid phishing attacks
- Block known bad websites. Malwarebytes DNS filtering blocks malicious websites used for phishing attacks, as well as websites used to spread or control malware.
- Don't take things at face value. Phishing attacks often seem to come from people or brands you know, and use themes that require urgent attention, such as missed deliveries, account suspensions, and security alerts.
- Take action. If you receive a phishing attempt at work, report it to your IT or security team. I you fall for a phish, make your data useless: If you entered a password, change it, if you entered credit card details, cancel the card.
- Use a password manager. Password managers can create, remember, and fill in passwords for you. They protect you against phishing because they won't enter your credentials into a fake site.
- Use a FIDO2 2FA device. Some forms of two-factor authentication (2FA) can be phished just as easily as a password. 2FA that relies on a FIDO2 device can’t be phished.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.